What is Network Security Key & How to Find It?
Last Updated :
22 Feb, 2023
If you ever come across the Wi-Fi settings, you have probably heard of the network security key. This security key is nothing but another name for the Wi-Fi password. These security keys consist of strings or codes of characters that are used to connect the devices to the wireless network.

However, many users don't know about the network security key and end up getting errors while finding it. So in this guide, we will give you complete details about a network security key and the methods to find it.
What is a Network Security Key?
As we have mentioned, a network security key is a set of characters that authorize you to access a network. This key gives a secure connection between the serving network and the requesting client.
A powerful network security key must contain more than 8 characters mixed with letters and numbers. If you don't make the network security key complex, it might become vulnerable to third-party attacks.
Moreover, hackers and cybercriminals can easily access the network if it does not contain any security key. Majorly, there are three types of wireless security encryptions which are used to lock the network security key:
1. WEP (Wired Equivalent Privacy)
Wired Equivalent Privacy, or WEP, is one of the oldest wireless security encryptions used in outdated systems. This network encryption provides minimum protection, which is easy to break but difficult to configure simultaneously.
WEP uses the static encryption code, which you can access through any decryption software. Many security experts don't recommend WEP due to the lesser secured encryption.
2. WPA (Wi-Fi Protected Access)
Wi-Fi Protected Access, also known as WPA, is the advanced version of WEP. This security encryption eliminates some vulnerabilities of the WEP key because it contains advanced protocols and additional features.
Although WPA comes in computing devices with wireless connections, it is not secure enough from cyber attacks. WPA network security key was developed to work with network adaptors but may not work properly with older routers.
3. WPA2 (Wi-Fi Protected Access 2)
WPA 2, or Wi-Fi Protected Access 2, is the most advanced network security key. This security key is the upgraded version of WPA to eliminate the chances of cyber attacks.
It uses AES encryption, making this security key the most suitable choice for business and home networks. WPA 2 encrypts the internet data to prevent it from any unauthorized access.
Also Read:
How to Find a Network Security Key?
Let's now look at the methods to find the network security keys in different devices such as Linux, Windows, Android, etc.
On Windows
Open the Control Panel and change the icon view to Large icons. Here you will see "Network and Sharing Center," so click and open it:

In the Network and Sharing Center option, click on the Wi-Fi connection to open the Wi-Fi Status:

In the pop-up window of Wi-Fi Status, you will see the Wireless Properties, so click and open it:
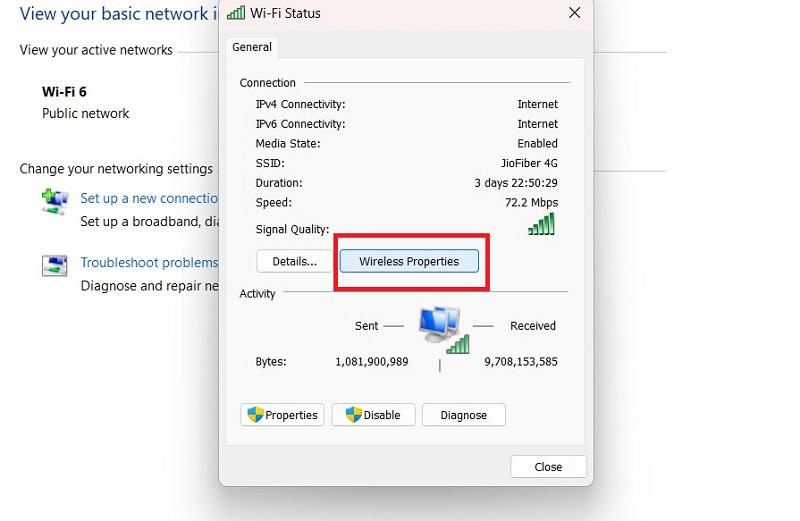
Click on the Security pane, and you will see the details about your Wi-Fi. Now, click on the Show characters to display the password:

On Linux
You can check the network security key from the terminal in Linux. First, please run the cd command to make the system.connections as the current directory of the terminal:
cd /etc/NetworkManager/system-connections/

Now, run the ls command to check the files of the system-connections directory:

Here, you will get the file that contains all the information about the wireless connection, so you can display it through the cat command:
sudo cat <Wi-Fi NAME>

As you can see in the above image, the psk contains the network security key of the connected Wi-Fi.
Note: We are using Rocky Linux for this process, but you can run the above commands in any other Linux distribution.
Protecting Network Security Key is Essential
The network security key is important to connect your device to the wireless network. If you are using an ethernet (LAN) connection, you don't require a network security key. However, protecting the network security key is essential because it gives anyone access to your network and can sometimes become problematic.
That's why we have explained everything about the network security key and ways to find it. We have included a few simple steps for Windows and Linux to get a security key.
Similar Reads
How to Become a Network Security Engineer in 2025 In a world where cyber attacks result in an average annual loss of $10.3 billion, network security engineers have become crucial to the cybersecurity strategies of organizations of all sizes. Unlike broader cybersecurity roles that protect an entire digital infrastructure, network security engineers
8 min read
Top 10 Network Security Best Practices in 2025 Are your network defenses strong enough to withstand today's advanced cyber threats? What measures have you implemented to protect your organization's data? As cyberattacks become more frequent, sophisticated, and devastating, these questions are more critical than ever. Organizations face a constan
8 min read
192.168.0.1 Admin Login Before even beginning the discussion, one needs to be clear about the concept of an IP Address. The IP address, or the Internet Protocol address, is defined as a numerical tag that is assigned to each and every computer that is a part of a computer network. The reason for reserving a few IP addresse
6 min read
How to View Wired and Wireless NIC Information? NIC stands for Network Interface Card. NIC is additionally called an Ethernet or physical or network card. NIC is one of the major and imperative components to associate a gadget to the network. Each gadget that must be associated with a network must have a network interface card. Even the switches
5 min read
What is Network Security? Every company or organization that handles a large amount of data, has a degree of solutions against many cyber threats. This is a broad, all-encompassing phrase that covers software and hardware solutions, as well as procedures, guidelines, and setups for network usage, accessibility, and general t
10 min read