Before continuing reading, read about LDAP in general. Lightweight Directory Access Protocol (LDAP) is an Internet protocol that works on TCP/IP, used to access information from directories. The LDAP protocol is used to access an Active Directory.
LDAP enumeration is a method of enumeration of the Active Directory. The service typically operates on TCP ports 389 and 639 by default. LDAP enumeration can enumerate usernames, addresses, and loads of juicy information that can be reused for other attacks, such as social engineering attacks. This may include:
- Usernames: Who's inside the system?
- Groups: Which groups or teams are there?
- Computers: What machines are attached to?
- Addresses: Contact or company details.
For ethical hackers or penetration testers, LDAP enumeration helps understand a network’s structure, which can be useful for security assessments. However, attackers might misuse it for social engineering or other attacks, so it’s critical to perform enumeration only with permission
Several tools make LDAP enumeration easier, each with unique strengths. Here’s a quick overview of the ones we’ll cover:
- Nmap: A network scanning utility with LDAP query scripts.
- enum4linux: An enumerating Linux tool for Windows Active Directory information.
- windapsearch: A Python program for comprehensive LDAP queries in Windows domains.
- ldapsearch: A command-line program for accurate LDAP searches.
- JXplorer: A graphical LDAP client for browsing directories visually.
Before we begin, ensure that the tools are installed on your Linux platform (e.g., Ubuntu or Kali Linux). Open a terminal (Ctrl + Alt + T) and enter these commands:
# Update package list
sudo apt update
# Install Nmap
sudo apt install nmap
# Install enum4linux
sudo apt install enum4linux
# Install ldapsearch (part of openldap-utils)
sudo apt install ldap-utils
# Install JXplorer (GUI tool)
sudo apt install jxplorer
LDAP Enumeration using Nmap:
Using the LDAP-search NSE script of Nmap we can scan for the LDAP service, and then we can attempt other arguments to this script such as LDAP.searchattrib, you can also use the LDAP-brute script, and when you have no valid credentials. It's a good tool for finding LDAP services and pulling details like usernames or server information.
Example 1: Basic LDAP Search
To verify an LDAP service on port 389 and list user accounts:
nmap -p 389 --script ldap-search --script-args 'ldap.username="cn=ldaptest,cn=users,dc=cqure,dc=net",ldap.password=ldaptest,ldap.qfilter=users,ldap.attrib=sAMAccountName' <IP_ADDRESS>
- - p 389: It scans the TCP port 389.
- --script ldap-search: This option runs the ldap-search script.
- --script-args: This option specifies credentials and filters (e.g., sAMAccountName for usernames).
- <IP_ADDRESS>: Replace with the target server’s IP (e.g., 192.168.1.10).

Example 2: Custom LDAP Query
To find Windows servers and their details (e.g., operating system, creation date) use the below command:
nmap -p 389 --script ldap-search --script-args 'ldap.username="cn=ldaptest,cn=users,dc=cqure,dc=net",ldap.password=ldaptest,ldap.qfilter=custom,ldap.searchattrib="operatingSystem",ldap.searchvalue="Windows *Server*",ldap.attrib={operatingSystem,whencreated,OperatingSystemServicePack}' <IP_ADDRESS>- ldap.qfilter=custom: Allows custom filtering.
- ldap.searchvalue="Windows *Server*": Targets Windows Server systems.
- ldap.attrib: Retrieves specific attributes like operatingSystem.
Note: If you don’t have credentials try the ldap-brute to test for weak passwords (only with permission):
nmap -p 389 --script ldap-brute <IP_ADDRESS>
LDAP Enumeration Using enum4linux:
enum4linux is a Linux tool designed for enumerating Windows Active Directory and SMB services, including LDAP. It’s excellent for extracting user accounts, groups, and domain details without needing a GUI.
Example: Enumerate Accounts and Groups
To list accounts and groups from an LDAP server:
enum4linux <IP_ADDRESS> | egrep "Account|Domain|Lockout|group"
- <IP_ADDRESS>: The target server’s IP.
- egrep: Filters output to show only lines with “Account,” “Domain,” “Lockout,” or “group.”
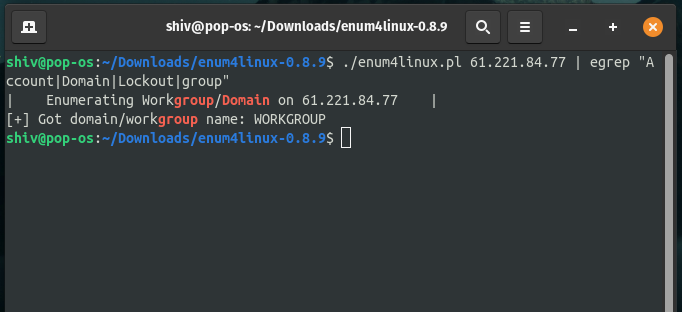
Note: enum4linux is simple and doesn’t require credentials for anonymous queries, though authenticated scans yield more data.
LDAP Enumeration Using Windapsearch:
windapsearch is a Python script that uses LDAP queries to enumerate users, groups, computers, and privileged accounts in a Windows domain. It’s ideal for penetration testers who have valid credentials.
Example 1: Enumerate Computers
To list computers in the domain:
python3 windapsearch.py --dc-ip <IP_ADDRESS> -u <USERNAME> -p <PASSWORD> --computers
- --dc-ip: The domain controller’s IP.
- -u <USERNAME>: A valid domain username (e.g., domain\user).
- -p <PASSWORD>: The user’s password.
- --computers: Targets computer objects.
Example 2: Enumerate Groups
To list groups:
python3 windapsearch.py --dc-ip <IP_ADDRESS> -u <USERNAME> -p <PASSWORD> --groups
Example 3: Enumerate Domain Admins
To find privileged users (e.g., Domain Admins):
python3 windapsearch.py --dc-ip <IP_ADDRESS> -u <USERNAME> -p <PASSWORD> --da
Example 4: Enumerate Privileged Users
To list users with elevated privilege
python3 windapsearch.py --dc-ip <IP_ADDRESS> -u <USERNAME> -p <PASSWORD> --privileged-users
Note: windapsearch is precise and supports CSV output for further analysis, making it a favorite for Active Directory enumeration.
LDAP Enumeration Using Ldapsearch:
LDAP search makes a connection to an LDAP server, and it executes a search by using different paraments. The filter works to the string representation for search filters as defined in RFC 4515 else it uses (objectClass=*).
Example 1: Check Null Credentials
To test if the LDAP server allows anonymous access:
ldapsearch -x -H ldap://<IP_ADDRESS> -D '' -w '' -b "DC=<SUBDOMAIN>,DC=<TLD>"
- -x: Uses simple authentication.
- -H ldap://<IP_ADDRESS>: Specifies the LDAP server.
- -D '' -w '': Attempts anonymous login (no username or password).
- -b "DC=<SUBDOMAIN>,DC=<TLD>": Sets the search base (e.g., DC=example,DC=com).
Example 2: Validate Credentials
To query with valid credentials:
ldapsearch -x -H ldap://<IP_ADDRESS> -D '<DOMAIN>\<USERNAME>' -w '<PASSWORD>' -b "DC=<SUBDOMAIN>,DC=<TLD>"
- -D '<DOMAIN>\<USERNAME>': The user’s domain and username (e.g., MYDOM\john).
- -w '<PASSWORD>': The password.
- -b: The search base.
Note: For secure connections, use LDAPS (-H ldaps://<IP_ADDRESS>:636). If you get a “bind must be completed” error, the credentials are invalid.
LDAP Enumeration with JXplorer
JXplorer is a graphical LDAP client that lets you browse and query LDAP directories visually, like a file explorer for Active Directory. It’s great for beginners who prefer a GUI over the command line.
1. Launch JXplorer from the terminal:
jxplorer
2. Connect to the LDAP server:
- Host: Enter the server’s IP or hostname.
- Port: Use 389 for LDAP or 636 for LDAPS.
- Base DN: Set to DC=<SUBDOMAIN>,DC=<TLD> (e.g., DC=example,DC=com).
- User DN/Password: Enter credentials or leave blank for anonymous access.
3. Browse the directory tree to view users, groups, or computers.
Security Considerations
LDAP enumeration can reveal sensitive data so we need to responsibly use it don't use this without permission, here are some security consideration:
- Ethical Use: Do not enumerate systems unless authorized since it can be equated to illegal hacking.
- Secure Connections: Protect credentials and searches with LDAPS on port 636 to prevent exposing sensitive information.
- Limit Anonymous Access: Servers that support unsecured anonymous searches are vulnerable. Secure access through NTLM or Kerberos authentication.
- Validate Inputs: When using windapsearch or ldapsearch, ensure the credential and filter values are accurate, or else they will be subjected to LDAP
- Monitor Logs: Inspect LDAP server lists and monitor for suspicious searching activity as they might act as indicators of enumeration children reactions.
Why Use LDAP Enumeration
LDAP enumeration is valuable for:
- Security Testing: Direct penetration testers and assist them in determining vulnerabilities within Active Directory.
- Network Management: Assist system administrators while they audit user/group accounts.
- Learning: Teaches cybersecurity students about LDAP and directory services.
Conclusion
LDAP enumeration is a key skill for exploring Active Directory and understanding network structures. By using Nmap, enum4linux, windapsearch, ldapsearch, and JXplorer, you can uncover usernames, groups, and more on TCP ports 389 and 636. Whether you’re securing a network or learning cybersecurity, LDAP enumeration is a must-know technique.
Similar Reads
Ethical Hacking Tutorial This Ethical Hacking tutorial covers both basic and advanced concepts of Ethical Hacking. Whether you are a beginner or an experienced cybersecurity professional, this tutorial is the perfect resource to learn how to tackle vulnerabilities and weaknesses in systems before malicious hackers can explo
13 min read
Introduction to Ethical Hacking
What is Hacktivism ?Now people use social media to protest and raise their voices about political or social issues instead of marching on the street. This is what hacktivism perfectly displays. Hacktivism combines ‘hacking’ with ‘activism’, where a person or organization uses hacking to fulfill a political or social ag
11 min read
The Hackers MethodologyA hacker is someone skilled in computer systems, networking, and programming who uses their expertise to exploit vulnerabilities in a digital system to carry out actions as per their will. The term 'hacker can be used in both positive and negative ways, depending on the hacker's intent. Ethical hack
4 min read
Remote Access in Ethical HackingRemote access is a vulnerability through which attackers can control any device. Most commonly, payloads are used for remote control. Payloads are sent through social engineering or phishing attacks. Once the payload is injected, the actual attack begins. The payload will provide a reverse connectio
5 min read
Information Gathering Tools for Kali LinuxInformation Gathering means gathering different kinds of information about the target. It is basically, the first step or the beginning stage of Ethical Hacking, where the penetration testers or hackers (both black hat or white hat) tries to gather all the information about the target, in order to u
5 min read
ARIN in Ethical HackingARIN is the American Registry for Internet Numbers, a non-profit corporation that assigns IP addresses to organizations in North America and beyond. ARIN stands for the American Registry for Internet Numbers, a non-profit corporation that assigns IP addresses to organizations in North America and be
3 min read
Basic Characteristics of Computer NetworksComputer networks allow multiple devices to connect and share resources like files, printers, and internet access. Key characteristics include the network's size (like local or wide area), the way data is transferred (wired or wireless), and the network's layout (such as star or mesh). These feature
5 min read
Foot Printing and Reconnaissance
Scanning Networks
What is Credentialed Vulnerability Scan?Scanning is the second phase in the hacking methodology and plays an important role in identifying critical vulnerabilities within a system or organization. An effective scanning process helps by detecting weaknesses that can be patched before attackers have a chance to exploit them. However, do vul
4 min read
What are Scanning Attacks?Scanning in ethical hacking is a network exploration technique used to identify the systems connected to an organization's network. It provides information about the accessible systems, services, and resources on a target system. Some may refer to this type of scan as an active scan because it can p
7 min read
Malware Scan in Ethical HackingIn ethical hacking, malware scanning is not like finding a virus—it's about locating deeply hidden threats that traditional antivirus programs often miss. Malware scans are critical for security professionals who must protect confidential data from new threats like spyware, rootkits, keyloggers, and
5 min read
What is Running of a Malware Scan?There are so many types of malware out there that it can be hard to know which ones you should be taking extra precautions for. One type of malware is known as a rootkit, and these are extremely difficult to detect. A rootkit is usually installed on the Windows operating system when an unsuspecting
5 min read
WAScan - web application security scanner in Kali LinuxWAScan stands for Web Application Scanner. It is an open-source web application vulnerability scanner. The tool uses the technique of black-box to find various vulnerabilities. This technique will not scan the whole source code of a web application but work like a fuzzer Which means it scans the pag
2 min read
What is TCP-ACK Scanning?TCP-ACK is a third step of the TCP 3-Way Handshake process (SYN, SYN-ACK, ACK). In TCP-ACK, the client acknowledges the response of the Server, and establish a connection to proceed with the data transfer and any other communication processes. TCP-ACK Scanning: In this scan, the ACK packets are sent
2 min read
Port Scanning Techniques By Using NmapNmap is a security auditing tool used in the security field to actively enumerate a target system/network. It is one of the most extensively used tools by network administrators and conversely attackers for reconnaissance (enumeration), the first step in the 5 phases of hacking. Nmap is used to acti
5 min read
What is SYN Scanning?Internet and its usage have evolved over the years. The Internet has become an integral part of daily human activities, and it becomes hard to imagine life without the Internet. The Cyber world has become so fascinating that it is often the soft target of cyberattackers and hackers to steal personal
3 min read
What is UDP Scanning?UDP scanning is a process in which we scan for the UDP services that are being deployed on the target system or are currently in a running state. UDP is a connectionless protocol, hence it is hard to probe as compared to TCP. Working of UDP scan:In UDP scan usually, we take advantage of any UDP serv
2 min read
Enumeration
Cyber Security - Types of EnumerationEnumeration is fundamentally checking. An attacker sets up a functioning associated with the objective host. The weaknesses are then tallied and evaluated. It is done mostly to look for assaults and dangers to the objective framework. Enumeration is utilized to gather usernames, hostname, IP address
15+ min read
What is DNS Enumeration?In this article, we will learn about DNS Enumeration and the process of DNS enumeration with a practical approach. Domain Name System(DNS) is nothing but a program that converts or translates a website name into an IP address and vice versa. Example: A user enters www.geeksforgeeks.org in a browser,
2 min read
SMTP EnumerationSMTP (Simple Mail Transfer Protocol) is a set of communication guidelines that allow web applications to perform communication tasks over the internet, including emails. It is a part of the TCP/IP protocol and works on moving emails across the network. SMTP enumeration allows us to identify valid us
2 min read
LDAP EnumerationBefore continuing reading, read about LDAP in general. Lightweight Directory Access Protocol (LDAP) is an Internet protocol that works on TCP/IP, used to access information from directories. The LDAP protocol is used to access an Active Directory. LDAP enumeration is a method of enumeration of the A
6 min read
What is NTP Enumeration?NTP Enumeration is a process by which an attacker can discover NTP servers on the network. This information can then be used to find vulnerable NTP servers, or simply to further enumerate the network. Servers that are allowed access from the internet usually have a much higher chance of being exploi
4 min read
What is IPsec Enumeration?In the world of computer hacking, IPsec enumeration is a process by which attackers are able to perform authentication on an IPsec system. It can allow them to gain access to the network and gather information. IPsec Enumeration: IPsec's enumeration is the process of gaining access to security keys
4 min read
What is NetBIOS Enumeration?NetBIOS is an acronym that stands for Network Basic Input Output System. It enables computer communication over a LAN and the sharing of files and printers. TCP/IP network devices are identified using NetBIOS names (Windows). It must be network-unique and limited to 16 characters, with 15 reserved f
5 min read
SNMP EnumerationSimple Network Management Protocol (SNMP) is an application layer protocol that runs on UDP and maintains and manages IP network routers, hubs, and switches. SNMP agents run on networking devices in Windows and UNIX networks.SNMP (Simple Network Management Protocol) is an application layer protocol
6 min read
What is Security Testing in Enumeration?Security Testing in Enumeration is when a tester repeatedly performs the same task on a system to see if vulnerabilities exist. One way that a tester might do this is by creating scripts or programs to test for the existence of security issues in the system's software code. A good example of this ty
4 min read
System Hacking
What is System Hacking in Ethical Hacking?System hacking is the process of exploiting vulnerabilities in electronic systems for the purpose of gaining unauthorized access to those systems. Hackers use a variety of techniques and methods to access electronic systems, including phishing, social engineering, and password guessing. Purpose of S
2 min read
What is Windows Hacking ?Windows OS is a graphical user interface (GUI) operating system developed by Microsoft. It was first released in 1985 as an add-on for MS-DOS, which was the most popular version of MS-DOS at that time. In its early days, Windows OS was known as “Microsoft DOS†or “MS-DOS†and later on it became know
6 min read
Importance of Physical Security in Ethical HackingPhysical security is the security of personnel, hardware, software, networks, and data from physical actions and events that could cause loss or serious damage to a business organization, federal agency, or social group. This includes protection against fire, flood, natural disaster, theft, vandalis
3 min read
What is Non-Electronic Password Attack on a System?Non-electronic password attacks are forms of hacking that seek to bypass any form of authentication or authentication system. Typically, a non-electronic password attack will use an automated script to probe for passwords on the network. One way this may be done is by placing port scanning software
3 min read
What is Password Guessing Attack?There are a number of methods to crack a user's password, but the most prominent one is a Password Guessing Attack. Basically, this is a process of attempting to gain the system's access by trying on all the possible passwords (guessing passwords). If the attacker manages to guess the correct one, h
4 min read
Credential Stuffing in Ethical HackingCredential Stuffing is a cyberattack in which the attacker uses the list of credentials that are publicly available and then breaks into the system with various types of custom bots and other automation along with IP spoofing to prevent getting blocked. But as per the reports, only a small fraction
2 min read
Reverse Brute Force Attack in System HackingThe well-known and frequently utilized method of breaking into a system is brute force. The Reverse Brute Force attack is a different method from Brute Force in certain aspects but is very close to it overall. But first, we must comprehend the former (Brute Force) in order to comprehend the latter.
4 min read
Brute Force AttackA Brute force attack is a well known breaking technique, by certain records, brute force attacks represented five percent of affirmed security ruptures. A brute force attack includes 'speculating' username and passwords to increase unapproved access to a framework. Brute force is a straightforward a
3 min read
What is a Default Password Attack Threat?The term “attack†is used here to denote performing a variety of hacks, including brute force and social engineering, that require access to the target's computer system or network. Here are some terms and processes related to this skill boot camp: Brute ForcingPassword HashingCapture The Flag (CTF)
3 min read
USB Drop Attack in System HackingThe USB drop attack is a client-side attack in system hacking. This means that an attacker must be physically near the victim and plug a malicious USB device into the victim's computer to launch this type of attack. This type of cybersecurity hack is often used by cybercriminals to steal data or ins
5 min read
What is Sniffing Attack in System Hacking?A sniffing attack in system hacking is a form of denial-of-service attack which is carried out by sniffing or capturing packets on the network, and then either sending them repeatedly to a victim machine or replaying them back to the sender with modifications. Sniffers are often used in system hacki
4 min read
How to Prevent Man In the Middle Attack?In a web application, there are two things usually: the client and the server. The third entity that remains unnoticed most of the time is the communication channel. This channel can be a wired connection or a wireless connection. There can be one or more servers in the way forwarding your request t
9 min read
How To Generate Rainbow Table Using WinRTGen?Rainbow Tables are a large set of pre-computed hashes that are used for reversing cryptographic hash functions generally used for password cracking. It makes password cracking easy. Rainbow tables can be used to recover many types of password hashes for example MD4, MD5, SHA1, etc. In simpler terms,
4 min read
What is Elcomsoft Distributed Password Recovery?Elcomsoft Distributed Password Recovery is software to help you break the password on various types of computers, including standard Windows and Linux PCs. In order to use Elcomsoft Distributed Password Recovery, you will need a Home Agent application installed on your computer. The Home Agent is a
4 min read
pwdump7 in System HackingHackers gain access to specific computers on a network through system hacking. System hacking is the process of exploiting vulnerabilities in electronic systems with the goal of gaining unauthorized access to those systems. Hackers use a variety of techniques and methods to gain access to electronic
3 min read
FGDUMP in System HackingFgdump in system hacking in Ethical hacking is a tool and technique used by the ethical hacker that helps the intruder gain full access to the operating system of a remote machine. This tool can be quite useful when you are trying to find vulnerabilities within a company's computer systems, or if yo
5 min read
Password Auditing With L0phtcrack 7 ToolIn essence, password auditing programs make guesses about the credentials being used on your network. They accomplish this using a combination of brute force and dictionary assaults, among other techniques, and then inform you of any other ways the passwords may be compromised, such as by being pwne
5 min read
What is Salted Password Hashing?Salted password hashing can be used to improve password security by adding additional layers of randomness on top of the hashing process. Salt is a cryptographically secure random string that is added to a password before it's hashed, and the salt should be stored with the hash, making it difficult
4 min read
How to Defend Against Password Cracking of Systems?To Defend against Password Cracking of systems in Ethical Hacking, you need to know how password cracking functions. Password cracking is the act of using a computer program to try to guess an inputted password. There are many forms of attacks that can be used in this process, but they all result in
6 min read
How to Defend Against Wi-Fi Pineapple?A Hack Wi-Fi Pineapple is a wireless auditing platform that enables network security managers to do penetration testing. Penetration tests are a sort of ethical hacking in which white hat hackers look for security flaws that a black hat attacker may exploit. A Wi-Fi Pineapple resembles a typical Wi-
6 min read
What is DLL Hijacking?Each Windows program relies on small assistive files named DLLs (Dynamic Link Libraries). These provide applications with functionality for simple activities such as printing, saving a file, or going online. When a malicious DLL is hidden inside by a hacker with the same name, the application picks
8 min read
How to Prevent Privilege Escalation?Privilege escalation is the process of exploiting a bug or design flaw in an operating system and obtaining elevated privileges to access information, change data, or exploit vulnerabilities. This blog post explores some common ways privilege escalation could be mitigated. Prevent Privilege Escalati
4 min read
Malware Analysis
Most Popular Methods Used By Hackers to Spread RansomwareRansomware is a malicious malware code usually designed to deny users access to their own systems until a ransom payment is paid to the creator of ransomware to achieve a decryption key. Ransomware is far more dangerous than normal malware, it is spread through many ways like phishing emails that co
3 min read
What is Malvertising? Working and ExamplesCyber attacks are extremely dangerous attacks executed on the Internet. Cyber attacks give unauthorized access to hackers/ cyber criminals of the users or the organizations of the computer system. Modern times have recorded a huge increase in cyber attacks conducted every second. MalvertisingCyber a
8 min read
How to Find Trojan on Computers?A Trojan virus, or Trojan malware, is actually malicious code or software that looks legitimate to the victim but can take full control over the victim's computer. It is designed to steal, manipulate, disrupt, damage, or do some other destructive action on your data, network, and computer system. It
4 min read
Malwares - Malicious SoftwareMalware is malicious software and refers to any software that is designed to cause harm to computer systems, networks, or users. Malware can take many forms. Individuals and organizations need to be aware of the different types of malware and take steps to protect their systems, such as using antivi
8 min read
What is WannaCry and How does WannaCry ransomware worksIn May 2017, a massive cyberattack shook the world when the WannaCry ransomware outbreak spread rapidly across hundreds of thousands of computers in more than 150 countries. This ransomware targeted organizations ranging from government agencies to healthcare providers, including the UK’s National H
5 min read
Working of Stuxnet VirusStuxnet is a powerful and malicious computer worm that first appeared in 2010. It is also reported to be the largest and most expensive malware of this type. It exploited a previously unknown Windows zero-day vulnerability to infect the targeted system and spread to other systems. The virus primaril
6 min read
CryptoLocker Ransomware AttackRansomware is a malicious malware code specifically designed to deny users access to their own systems until a ransom payment is paid to the ransomware creator to obtain a decryption key. Far more dangerous than normal malware, ransomware is spread through phishing emails with malicious files, links
4 min read
Storm WormIn this article we will know about the one of biggest malware attacks in 2007, It actually brings a change to the world of cyber security, It is known as Storm Worm. Storm Worm:Storm Worm in technical terms is a trojan horse that pretends itself to be a legit program. This malware is so dangerous th
3 min read
What is Zeus Malware?Malware is a malicious program designed to gain access to a computer system without the user's permission. Malware includes various types of unwanted programs such as computer viruses, worms, Trojans, ransomware, spyware, etc.You’re browsing the internet, and suddenly your computer starts acting str
8 min read
What is SQL Slammer Virus?The SQL Slammer is a computer virus that began in January 2003 and caused a denial of service on some Internet hosts, significantly slowing general Internet traffic. It spread rapidly and within 10 minutes he infected most of his 75,000 victims. Although the program is called the “SQL Slammer Wormâ€,
2 min read
How to Install Trojan Virus on Any Computer?A Trojan virus, or Trojan malware, is actually malicious code or software that looks legitimate to the victim but can take full control over the victim's computer. It is designed to steal, manipulate, disrupt, damage, or do some other destructive action on your data, network, and computer system. It
5 min read
Different Ways to Remove Trojan Horse MalwareA Trojan virus, or Trojan malware, is actually malicious code or software that looks legitimate to the victim but can take full control over the victim's computer. It is designed to steal, manipulate, disrupt, damage, or do some other destructive action on your data, network, and computer system. Ma
5 min read
How to Defend Against Botnets ?A botnet is a network of computers or devices that have been compromised and are controlled by an attacker, without the knowledge of the owners. These devices, once infected with malware, are controlled by the attacker to carry out activities, such as sending spam emails, launching distributed denia
5 min read
What is Proxy Trojan?A proxy Trojan is a type of computer virus that disguises itself as something else, such as a harmless file or website. When a user accesses it, the proxy Trojan hijacks their browser and sends the user to bogus websites or downloads malicious files. Proxy Trojans can be used in two ways: for steali
3 min read
What are Banking Trojans?A banking Trojan is a piece of malware that is used primarily to steal banking credentials by remotely installing malicious software on a victim's computer system. Banking Trojans are tailored to specific types of computers and may use the Windows registry for installation. On the infected computer,
3 min read
What is a Computer Virus?A computer virus is a type of malicious software program ("malware") that, when executed, replicates itself by modifying other computer programs and inserting its code. When this replication succeeds, the affected areas are then said to be "infected". Viruses can spread to other computers and files
9 min read
Virus HoaxVirus hoaxes are warning messages of viruses that are distributed via pop-ups, emails, and spam messages, the main objective of the virus hoax is to create fear and doubts in the user's mind. When the user panics, they usually fall into the trap of a virus hoax and get infected with phishing or rans
2 min read
Difference between Worms and VirusTwo of the most common and often misunderstood types of malware are worms and viruses. Although they are sometimes confused with each other, they function in different ways. Both can cause serious damage to computers or compromise personal data. Understanding the differences between them is importan
5 min read
Port Scanning AttackPrerequisite: What is scanning attacks? Cyber-Attackers use various different methods to carry out the execution of Cyber-Attacks on the computer network, depending on the ease through which the computer network can be attacked on its vulnerability. Each type of Cyber-Attack is risky and harmful in
3 min read
What is System Integrity Check?A system integrity check is a part of the system hardening process to confirm that we have taken all the necessary measures to prevent any unauthorized access to our systems and files. System integrity check verifies the integrity of different system components, such as operating systems, applicatio
6 min read
Code Emulation Technique For Computer Virus DetectionCode emulation is a technique for detecting technical events that are attributable to computer viruses. The technique is used in antivirus software and in intrusion detection systems. It compares an executable file or memory dump from one system with an archival copy of the same that has been saved
5 min read
Heuristic VirusA heuristic virus is a type of computer virus that replicates by guessing. It does this by analyzing what it perceives as the user's behavior and creating an infection that tries to mirror it. The aim of viruses like these is to make the user feel as if their data are being collected, so they could
6 min read
How to Prevent Backdoor Attacks?Cyber security or security of the web deals with the security mechanism of the cyber world. Cyber security is extremely necessary as it is important that computer networks have strong cyber security mechanisms set up to prevent any form of attack that may lead to compromise of computer network secur
3 min read
Sniffing
What are Active Sniffing Attacks?Active Sniffing Attacks in Ethical Hacking can lead to using the intercepted data for malicious purposes. The most common use of sniffing is to steal passwords, credit card numbers, and other sensitive data. Sniffers are software programs that let you intercept network traffic in a convert way witho
6 min read
What is Protocol Analyzer?The network protocol is a set of rules that regulates the communication and exchange of data over the internet or network. Both the sender and receiver should follow the same protocols in order to communicate and exchange the data. Whenever we access a website or exchange some data with another devi
3 min read
What is MAC Spoofing Attack?MAC Spoofing is a type of attack used to exploit flaws in the authentication mechanism implemented by wired and wireless networking hardware. In layman’s terms, MAC spoofing is when someone or something intercepts, manipulate or otherwise tampers with the control messages exchanged between a network
5 min read
How to Prevent MAC Flooding?A flood of MAC addresses is a serious concern for ethical hackers because it can leave your system vulnerable to attack. In order to prevent this from happening, consider some of the following precautions: Use secure passwords.Install and use antivirus software.Update your operating system on a regu
4 min read
What is Port Stealing?Cyber security is the security of the web and related services related to the web. Cyber security is the way to prevent many cyber attacks from taking place. Cyber security ensures that awareness of the cyber-attacks along with the different forms of cyber attacks are well-known to people so that th
3 min read
Dynamic Host Configuration Protocol (DHCP)Dynamic Host Configuration Protocol is a network protocol used to automate the process of assigning IP addresses and other network configuration parameters to devices (such as computers, smartphones, and printers) on a network. Instead of manually configuring each device with an IP address, DHCP all
14 min read
DHCP Starvation AttackDHCP (Dynamic Host Configuration Protocol) is used to assign IP addresses to machines within any network automatically. It is also known as zeroconf protocol, as network administrators don't need to assign IP addresses to machines manually. To assign IP addresses, DHCP makes use of DORA packets whic
4 min read
What is Rogue DHCP Server Attack?Rogue DHCP server attacks are gaining popularity but can be mitigated. The hacker sets up a rogue DHCP server and creates an IP address conflict by broadcasting a duplicate IP address. Hackers infiltrate a network by attacking the wireless router, which they do with ARP poisoning in order to inject
4 min read
What is ARP Spoofing Attack?Spoofing is a type of attack in which hackers gain access to the victim's system by gaining the trust of the victim (target user) to spread the malicious code of the malware and steal data such as passwords and PINs stored in the system.In Spoofing, psychologically manipulating the victim is the mai
3 min read
How to Prevent DNS Poisoning and Spoofing?The domain name system, or DNS, is a naming system for computers, services, and other internet resources that is hierarchical in nature. It's essentially the internet's phone book. Each domain name has a corresponding set of ten or so numbers that make up the domain name's IP address. Simple, user-f
6 min read
DNS Spoofing or DNS Cache poisoningPrerequisite - Domain Name Server Before Discussing DNS Spoofing, First, discuss what is DNS.A Domain Name System (DNS) converts a human-readable name (such as www.geeksforgeeks.org) to a numeric IP address. The DNS system responds to one or more IP-address by which your computer connects to a websi
3 min read
How to Detect Sniffer in Your Network?Sniffers are software or hardware devices that can be used for wiretapping over a computer network, such as LAN or WAN. They are used to collect data by listening and capturing IP packets. These devices usually have the ability of recording data which includes email, chat, web browsing, and informat
5 min read
Mitigation of DHCP Starvation AttackIn a DHCP starvation attack, an attacker creates spoofed DHCP requests with the goal of consuming all available IP addresses that a DHCP server can allocate. This attack targets DHCP servers. The attack could deny service to authorized network users. In other words, a malicious cyberattack that targ
5 min read
Social Engineering
What is Social Engineering? Working, Types, Prevention and ImpactSocial Engineering is an umbrella term for multiple malicious activities done by cyber criminals over the internet through human interaction. It doesn't involve the use of technical hacking techniques. Attackers use psychology and manipulation to trick users into performing actions that could compro
8 min read
What is Insider Attack?Cyber attacks on organizations are increasing both in number and magnitude. Often carried out by attackers with intentions to harm an organization, gain financial benefits, pursue political motives, spread terror, etc., these attacks always cost organizations in one form or another. Cyber security i
6 min read
What is an Impersonation Attack?An impersonation attack is a threat where hackers impersonate trusted people or organizations—such as your boss, bank, or a well-known service used by companies, to the trick victims so that they can give sensitive information, funds, or access to systems. Unlike classical malware-based attacks (e.g
6 min read
What are Tailgating?Tailgating is a term that refers to the practice of parking along the side of a road, usually by an open field or parking lot. Tailgaters are not only prohibited from entering the highway itself, but also have no right to drive on it at all. The term “tailgater†comes from tail-end Charlie, which me
5 min read
How Hackers Use Social Engineering to Get Passwords on Facebook?Social engineering is a powerful method for hackers to exploit computer systems without the use of malware or computer hacking tools. To carry out a successful social engineering hack, ethical hackers need to understand how to effectively use social media and human interaction to obtain sensitive in
4 min read
Pretexting in Social EngineeringPretexting is a social engineering technique that's used by hackers, spammers, and pranksters to assume and exploit the trust of an individual. It's been defined as the act of taking on an identity (usually those of a trusted person, such as a customer service representative) for the purpose of gain
4 min read
Credit Card FraudsThis era belongs to technology where technology becomes a basic part of our lives whether in business or home which requires connectivity with the internet and it is a big challenge to secure these units from being a sufferer of cyber-crime. Wireless credit card processing is a tremendously new serv
2 min read
Active Social Engineering Defense (ASED)A proactive tactic called Active Social Engineering Defense (ASED) is used to lessen the risk of being the target of social engineers. We must first comprehend social engineering in order better to comprehend active social engineering defense (ASED). Social Engineering Attack:Without the use of malw
6 min read
Cyber Crime - Identity TheftIdentity Theft also called Identity Fraud is a crime that is being committed by a huge number nowadays. Identity theft happens when someone steals your personal information to commit fraud. This theft is committed in many ways by gathering personal information such as transactional information of an
5 min read
Penetration Testing - Software EngineeringIn this guide, we'll explore the fundamentals of penetration testing, its importance in cybersecurity, and how it fits into the software development lifecycle (SDLC). From network security to web application security, we'll be going into various aspects of pen testing, equipping you with the knowled
10 min read
Denial-of-Service
Distributed Denial of Service DDoS attackImagine a scenario where you are visiting some websites and one of them seems to be a little slow. You might blame their servers for improving their scalability as they might be experiencing a lot of user traffic on their site. Most of the sites already take this issue into account beforehand. Chanc
6 min read
What are Bandwidth Attacks?Bandwidth attacks in ethical hacking target a network's bandwidth, and by extension, its available computing resources. A hacker can overload a network by sending a high number of packets to the computer or server at once. The processing power and memory in the system is limited and once it reaches
6 min read
HTTP Flood AttackCyber crimes are increasing with the growing demand for the internet. With an increasing number of cybercrime cases reported each year, awareness of cyberattacks is very important. Cyber crimes/cyberattacks are done by hackers who unethically want to breach user data and steal sensitive information
9 min read
ICMP Flood DDoS AttackIn today's world, Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks have become a major threat to present computer networks. DDoS is a kind of attack in which an attacker targets the victim's network resources such as bandwidth or memory so that the victim may stop responding
12 min read
Ping Flood AttackA Ping Flood Attack, or ICMP Attack (Internet Control Message Protocol Attack), is a type of offensive cyberattack utilized to attack the targeted device—computer, server, or network—with a flood of false requests. It is a Denial of Service (DoS) attack, as it is intended to disrupt normal operation
6 min read
What is a Permanent DoS (PDoS) Attack?In today's modern world, we often come across the term Cybercrime or Cyberattacks very frequently. With the increasing demand for the internet, cybercrime occurrence has taken a great spike. Cyber crimes are crimes involving cyber technology/computer networks. Cyberattacks are extremely dangerous as
6 min read
What is Phlashing?Phlashing is a type of Denial of Service (DoS) Attack, also known as a Permanent Denial of Service Attack (PDoS) which is very severe because there is no way to undo this attack's consequences as it damages/corrupts the system to such an extreme level that there is no other way except to replace or
4 min read