How to Install Wireshark on Windows?
Last Updated :
16 Dec, 2021
Wireshark is software that is widely used in the analysis of data packets in a network. Wireshark is completely free and open source. This packet analyzer is used for a variety of purposes like troubleshooting networks, understanding communication between two systems, developing new protocols, etc. The original name of Wireshark was Ethereal which was changed in 2006 due to some company's copyright issues. This software is written in C and C++, and its initial release was in the year 1998. Its latest release is 3.6.0 which got released on 22 November 2021. Wireshark is a cross-platform software, it can be run on Linux, windows, mac, and any other operating system.
Installing Wireshark on Windows:
Follow the below steps to install Wireshark on Windows:
Step 1: Visit the official Wireshark website using any web browser.

Step 2: Click on Download, a new webpage will open with different installers of Wireshark.

Step 3: Downloading of the executable file will start shortly. It is a small 73.69 MB file that will take some time.

Step 4: Now check for the executable file in downloads in your system and run it.
Step 5: It will prompt confirmation to make changes to your system. Click on Yes.

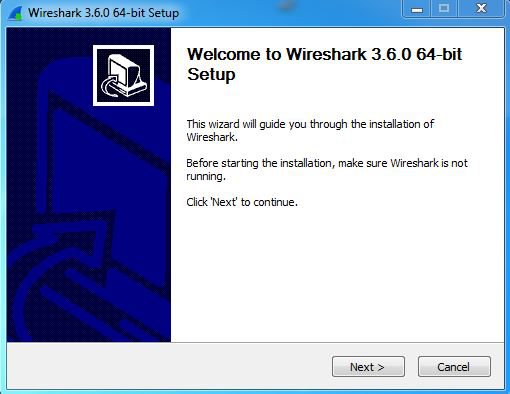
Step 6: Setup screen will appear, click on Next.
Step 7: The next screen will be of License Agreement, click on Noted.

Step 8: This screen is for choosing components, all components are already marked so don't change anything just click on the Next button.

Step 9: This screen is of choosing shortcuts like start menu or desktop icon along with file extensions which can be intercepted by Wireshark, tick all boxes and click on Next button.

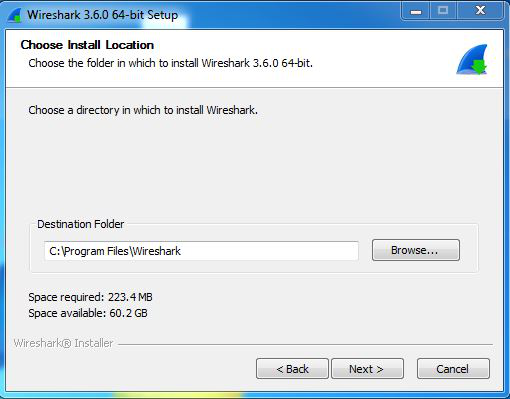
Step 10: The next screen will be of installing location so choose the drive which will have sufficient memory space for installation. It needed only a memory space of 223.4 MB.
Step 11: Next screen has an option to install Npcap which is used with Wireshark to capture packets pcap means packet capture so the install option is already checked don't change anything and click the next button.

Step 12: Next screen is about USB network capturing so it is one's choice to use it or not, click on Install.

Step 13: After this installation process will start.

Step 14: This installation will prompt for Npcap installation as already checked so the license agreement of Npcap will appear to click on the I Agree button.

Step 15: Next screen is about different installing options of npcap, don't do anything click on Install.

Step 16: After this installation process will start which will take only a minute.

Step 17: After this installation process will complete click on the Next button.

Step 18: Click on Finish after the installation process is complete.

Step 19: After this installation process of Wireshark will complete click on the Next button.

Step 20: Click on Finish after the installation process of Wireshark is complete.

Wireshark is successfully installed on the system and an icon is created on the desktop as shown below:

Now run the software and see the interface.

Congratulations!! At this point, you have successfully installed Wireshark on your windows system.
Similar Reads
What is OSI Model? - Layers of OSI Model
The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO). The OSI Model consists of 7 layers and each layer has specific functions and re
13 min read
TCP/IP Model
The TCP/IP model (Transmission Control Protocol/Internet Protocol) is a four-layer networking framework that enables reliable communication between devices over interconnected networks. It provides a standardized set of protocols for transmitting data across interconnected networks, ensuring efficie
7 min read
Types of Network Topology
Network topology refers to the arrangement of different elements like nodes, links, or devices in a computer network. Common types of network topology include bus, star, ring, mesh, and tree topologies, each with its advantages and disadvantages. In this article, we will discuss different types of n
12 min read
Computer Network Tutorial
A Computer Network is a system where two or more devices are linked together to share data, resources and information. These networks can range from simple setups, like connecting two devices in your home, to massive global systems, like the Internet. Below are the main components of a computer netw
7 min read
Basics of Computer Networking
A computer network is a collection of interconnected devices that share resources and information. These devices can include computers, servers, printers, and other hardware. Networks allow for the efficient exchange of data, enabling various applications such as email, file sharing, and internet br
14 min read
RSA Algorithm in Cryptography
RSA(Rivest-Shamir-Adleman) Algorithm is an asymmetric or public-key cryptography algorithm which means it works on two different keys: Public Key and Private Key. The Public Key is used for encryption and is known to everyone, while the Private Key is used for decryption and must be kept secret by t
13 min read
Difference Between IPv4 and IPv6
In the digital world, where billions of devices connect and communicate, Internet Protocol (IP) Addresses play a crucial role. These addresses are what allow devices to identify and locate each other on a network.To know all about IP Addresses - refer to What is an IP Address?Currently, there are tw
9 min read
Domain Name System (DNS)
The Domain Name System (DNS) translates human-readable domain names (e.g., www.google.com) into machine-readable IP addresses (e.g., 142.250.190.14), enabling internet communicationIt enables computers to locate and communicate with each other on the internet.Functions as a hierarchical, distributed
6 min read
Data Encryption Standard (DES) | Set 1
Data Encryption Standard (DES) is a symmetric block cipher. By 'symmetric', we mean that the size of input text and output text (ciphertext) is same (64-bits). The 'block' here means that it takes group of bits together as input instead of encrypting the text bit by bit. Data encryption standard (DE
15+ min read
Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
Network devices are physical devices that allow hardware on a computer network to communicate and interact with each other. Network devices like hubs, repeaters, bridges, switches, routers, gateways, and brouter help manage and direct data flow in a network. They ensure efficient communication betwe
9 min read