CRLFuzz - A Linux Tool To Scan CRLF Vulnerability Written in Go
Last Updated :
03 Jun, 2024
CRLF injection is a software application coding vulnerability that occurs when an attacker injects a CRLF character sequence where it is not expected. Checking the CRLF Vulnerability manually on the target domain becomes very complicated. So there should be an automated approach for studying the vulnerability. CRLFuzz is a computerized tool designed in the Golang language that scans the CRLF Vulnerability target with a single click. CRLFuzz tool is open-source and free to use.
Note: As CRLFuzz is a Golang language-based tool, so you need to have a Golang environment on your system. So check this link to Install Golang in your system. - Installation of Go Lang in Linux
Installation of CRLFuzz Tool on Kali Linux
Step 1: If you have downloaded Golang in your system, verify the installation by checking the version of Golang, use the following command.
go version

Step 2: Open up your Kali Linux terminal and move to Desktop using the following command.
cd Desktop

Step 3: You are on Desktop now create a new directory called CRLFuzz using the following command. In this directory, we will complete the installation of the CRLFuzz tool.
mkdir CRLFuzz

Step 4: Now switch to the CRLFuzz directory using the following command.
cd CRLFuzz

Step 5: Now you have to install the tool. You have to clone the tool from GitHub.
git clone https://github.com/dwisiswant0/crlfuzz

Step 6: The tool has been downloaded successfully in the CRLFuzz directory. Now list out the contents of the tool by using the below command.
ls
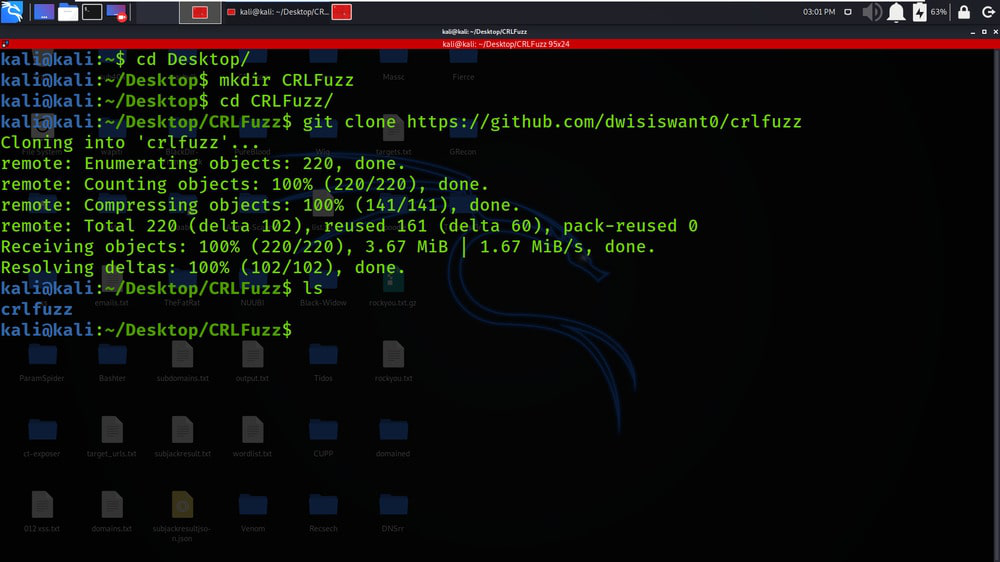
Step 7: You can observe that there is a new directory created of the CRLFuzz tool that has been generated while we were installing the tool. Now move to that directory using the below command:
cd crlfuzz/cmd/crlfuzz

Step 8: Build the tool using the following command.
go build

Step 9: Move the tool in /bin directory for quick usage from anywhere.
mv crlfuzz /usr/local/bin

Step 10: Now we are done with our installation, Use the below command to view the help (gives a better understanding of tool) index of the tool.
crlfuzz -h

Working with CRLFuzz Tool on Kali Linux
Example 1: Single URL
crlfuzz -u "http://geeksforgeeks.org"
In this example, we will be performing a CRLF Vulnerability scan on our target domain geeksforgeeks.org. -u tag is used to specify the domain URL.

Example 2: GET Method
crlfuzz -u "http://geeksforgeeks.org" -X "GET"
In this example, we will be changing the method of Scan from POST to GET method. -X tag is used to specify the method of the scan.

Example 3: Silent
crlfuzz -u "http://geeksforgeeks.org" -s
In this example, we will be performing a silent scan. In Silent Scan only the vulnerable targets will be displayed. As geeksforgeeks.org is a secure Website, the tool has not detected any vulnerable target.

Example 4: Verbose
crlfuzz -u "http://geeksforgeeks.org" -v
1. In this example, we will be displaying the verbose or detailed output of our scan. -v tag is used to display output in verbose mode.

2. In the below Screenshot, we have got the detailed reason why the query was not executed on the geeksforgeeks.org target.

Example 5: Version
crlfuzz -V
In this example, we will be displaying the version of the CRLFuzz tool. -V tag is used to display the version of the tool.

Example 6: URLs from a list
crlfuzz -l target.txt
1. In this Example, we are scanning the targets from the text file. In the below Screenshot, We have displayed the targets.txt file.

2. In the below Screenshot, we have got the results of our Scan.

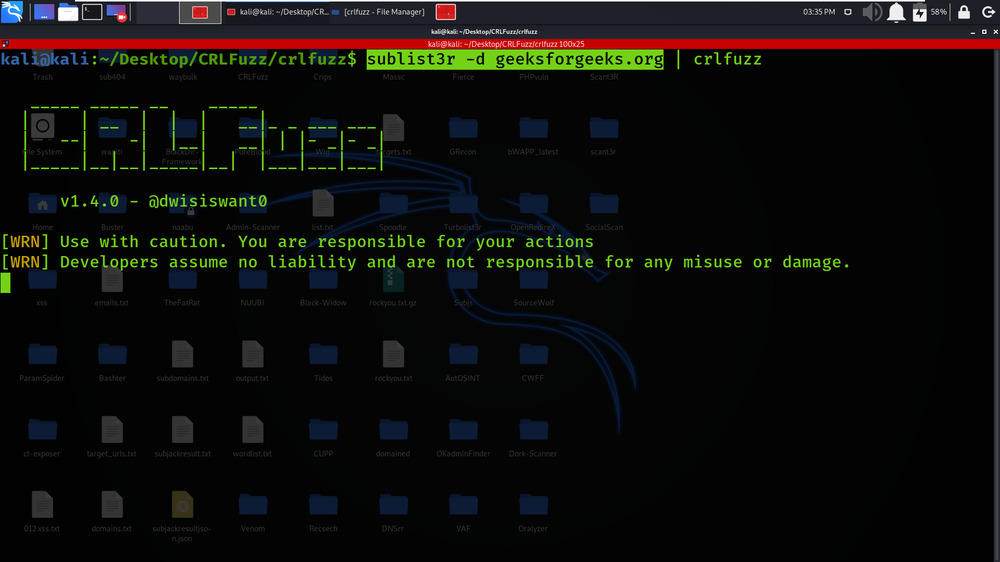
Example 7: From Stdin
sublist3r -d geeksforgeeks.org | crlfuzz
In this example, We are using the crlfuzz tool with the sublist3r tool.
Example 8: Data
crlfuzz -u "http://geeksforgeeks.org" -X "POST" -d "data=body"
In this example, we are using the -d tag for using the custom data.
-copy-2.webp)
Example 9: Adding Headers
crlfuzz -u "http://geeksforgeeks.org" -H "authtoken:dba9cad7701495309c43f93e6bd1b3d2"
In this Example, we are adding the Header to the request by using the -H tag.

Example 10: Using Proxy
crlfuzz -u "http://geeksforgeeks.org" -x http://127.0.0.1:8080
In this example, we are using the proxy server specified in the -x tag.

Example 11: Concurrency
crlfuzz -l target.txt -c 50
In this example, we are changing the concurrency value. Concurrency is the number of fuzzing at the same time

Example 12: Output
crlfuzz -l target.txt -o results.txt
In this Example, we are saving the results in the text file. We have used the -o tag for saving the results.

In the below Screenshot, we are displaying the results .txt file.

Example 13: Library
go run library.go
1. In this example, we are using CRLFuzz as a library.

2. In the below Screenshot, we are running the file.

Similar Reads
ffuf - Fast Web Fuzzer Linux Tool Written in Go
Fuzzing is the automatic process of giving random input to an application to look for any errors or any unexpected behavior. But finding any hidden directories and files on any web server can also be categorized under fuzzing. If we try to perform this process manually then it can take dozens of mon
3 min read
How to Check and Patch Meltdown CPU Vulnerability in Linux?
Here we will check and Patch Meltdown CPU Vulnerability in Linux. CPU hardware implementations are found vulnerable to side-channel attacks, They are known as: MeltdownSpectre Meltdown: It is a security vulnerability found in hardware that is affecting Intel x86 microprocessors, IBM POWER processors
3 min read
PHPvuln – Linux Tool to Find Vulnerabilities in PHP Code
PHP security vulnerabilities are a major cause for concern when it comes to web applications written in the PHP language since successful exploitation of such safety defects may lead to several regularly exploited attacks. Many vulnerabilities are usually not difficult to fix, but finding them in la
3 min read
RapidScan – The Multi-Tool Web Vulnerability Scanner in Kali Linux
RapidScan is a free and open-source tool available on GitHub which is based upon Open Source Intelligence (OSINT), the easiest and useful tool for reconnaissance. The RapidScan interface is very similar to Metasploit 1 and Metasploit 2, which provides a command-line interface that you can run on Kal
2 min read
What is Vulnerability Scanning in Kali Linux?
To understand vulnerability scanning, it is important to know what is a vulnerability. In the field of Cyber Security, the vulnerability can be defined as the weakness of the computer system which can be exploited by attacking the system to perform unauthorized actions and for gaining unauthorized a
5 min read
Kali Linux - Vulnerability Analysis Tools
Vulnerability Analysis is one of the most important phases of Hacking. It is done after Information Gathering and is one of the crucial steps to be done while designing an application. The cyber-world is filled with a lot of vulnerabilities which are the loopholes in a program through which hacker e
4 min read
Golismero - Scan Website, Vulnerability Scanning, WEB Server in Kali Linux
Golismero is a free and open-source tool available on GitHub. Golismero is an Open Source Intelligence and Information Gathering Tool based on (OSINT). Golismero is capable of doing everything almost you need for reconnaissance as per your need it can perform reconnaissance easily. Golismero works a
2 min read
Vulnnr – Vulnerability Scanner and Auto Exploiter in Kali Linux
Vulnerability Scanning is the methodology for testing the target domain for Security Flaws. These Flaws can be exploited and the attacker can gain access and also perform some malicious activities. There are various automated tools for performing Scanning. Vulnnr tool is a Python language-based scri
2 min read
WPrecon - Vulnerability Recognition Tool In CMS WordPress
A vulnerability is a flaw that could compromise an information system or Web Application's confidentiality, integrity, or availability. Vulnerability identification involves the process of discovering vulnerabilities and documenting these into an inventory within the target environment. Vulnerabilit
3 min read
OpenRedireX – Open Redirection Vulnerability Finder Tool in Linux
Open redirect is a security defect in an app or a web page that causes it to fail to properly authenticate URLs. When apps and web pages have requests for URLs, they are supposed to prove that those URLs are part of the expected page's domain. To test the web-based application manually for Open Redi
4 min read