Banker's Algorithm in Operating System
Last Updated :
24 Jan, 2025
Banker's Algorithm is a resource allocation and deadlock avoidance algorithm used in operating systems. It ensures that a system remains in a safe state by carefully allocating resources to processes while avoiding unsafe states that could lead to deadlocks.
- The Banker's Algorithm is a smart way for computer systems to manage how programs use resources, like memory or CPU time.
- It helps prevent situations where programs get stuck and can not finish their tasks. This condition is known as deadlock.
- By keeping track of what resources each program needs and what's available, the banker algorithm makes sure that programs only get what they need in a safe order.
Why Banker's Algorithm is Named So?
The banker's algorithm is named so because it is used in the banking system to check whether a loan can be sanctioned to a person or not. Suppose there are n number of account holders in a bank and the total sum of their money is S. Let us assume that the bank has a certain amount of money Y. If a person applies for a loan then the bank first subtracts the loan amount from the total money that the bank has (Y) and if the remaining amount is greater than S then only the loan is sanctioned. It is done because if all the account holders come to withdraw their money then the bank can easily do it.
It also helps the OS to successfully share the resources between all the processes. The banker's algorithm uses the notation of a safe allocation state to ensure that granting a resource request cannot lead to a deadlock either immediately or in the future. In other words, the bank would never allocate its money in such a way that it can no longer satisfy the needs of all its customers. The bank would try to be in a safe state always.
Components of the Banker's Algorithm
The following Data structures are used to implement the Banker’s Algorithm:
Let ‘n’ be the number of processes in the system and ‘m’ be the number of resource types.
1. Available
- It is a 1-D array of size ‘m’ indicating the number of available resources of each type.
- Available[ j ] = k means there are ‘k’ instances of resource type Rj
2. Max
- It is a 2-d array of size ‘n*m’ that defines the maximum demand of each process in a system.
- Max[ i, j ] = k means process Pi may request at most ‘k’ instances of resource type Rj.
3. Allocation
- It is a 2-d array of size ‘n*m’ that defines the number of resources of each type currently allocated to each process.
- Allocation[ i, j ] = k means process Pi is currently allocated ‘k’ instances of resource type Rj
4. Need
- It is a 2-d array of size ‘n*m’ that indicates the remaining resource need of each process.
- Need [ i, j ] = k means process Pi currently needs ‘k’ instances of resource type Rj
- Need [ i, j ] = Max [ i, j ] – Allocation [ i, j ]
Allocation specifies the resources currently allocated to process Pi and Need specifies the additional resources that process Pi may still request to complete its task.
Banker's algorithm consists of a Safety algorithm and a Resource request algorithm.
Banker's Algorithm
1. Active := Running U Blocked
for k = 1 to r:
New_request[k] := Requested_resources[requesting_process, k]
2. Simulated_allocation := Allocated_resources
for k = 1 to r: // Compute projected allocation state
Simulated_allocation[requesting_process, k] :=
Simulated_allocation[requesting_process, k] + New_request[k]
3. Feasible := true
for k = 1 to r: // Check if projected allocation state is feasible
if Total_resources[k] < Simulated_total_alloc[k]:
Feasible := false
4. if Feasible = true:
while set Active contains a process P1 such that:
for all k, Total_resources[k] - Simulated_total_alloc[k] >=
Max_need[P1, k] - Simulated_allocation[P1, k]:
Delete P1 from Active
for k = 1 to r:
Simulated_total_alloc[k] :=
Simulated_total_alloc[k] - Simulated_allocation[P1, k]
5. if set Active is empty:
for k = 1 to r: // Delete the request from pending requests
Requested_resources[requesting_process, k] := 0
for k = 1 to r: // Grant the request
Allocated_resources[requesting_process, k] :=
Allocated_resources[requesting_process, k] + New_request[k]
Total_alloc[k] := Total_alloc[k] + New_request[k]
Safety Algorithm
The algorithm for finding out whether or not a system is in a safe state can be described as follows:
1. Let Work and Finish be vectors of length 'm' and 'n' respectively.
Initialize: Work = Available
Finish[i] = false; for i=1, 2, 3, 4....n
2. Find an i such that both
2.1 Finish[i] = false
2.2 Needi <= Work
if no such i exists goto step (4)
3. Work = Work + Allocation[i]
Finish[i] = true
goto step (2)
4. if Finish [i] = true for all i
then the system is in a safe state
Resource-Request Algorithm
Let Requesti be the request array for process Pi. Requesti [j] = k means process Pi wants k instances of resource type Rj. When a request for resources is made by process Pi, the following actions are taken:
1. If Requesti <= Needi
Goto step (2) ; otherwise, raise an error condition, since the process has exceeded its maximum claim.
2. If Requesti <= Available
Goto step (3); otherwise, Pi must wait, since the resources are not available.
3. Have the system pretend to have allocated the requested resources to process Pi by modifying the state as
follows:
Available = Available - Requesti
Allocationi = Allocationi + Requesti
Needi = Needi- Requesti
Example: Considering a system with five processes P0 through P4 and three resources of type A, B, C. Resource type A has 10 instances, B has 5 instances and type C has 7 instances. Suppose at time t0 following snapshot of the system has been taken:

Q.1 What will be the content of the Need matrix?
Need [i, j] = Max [i, j] – Allocation [i, j]
So, the content of Need Matrix is:
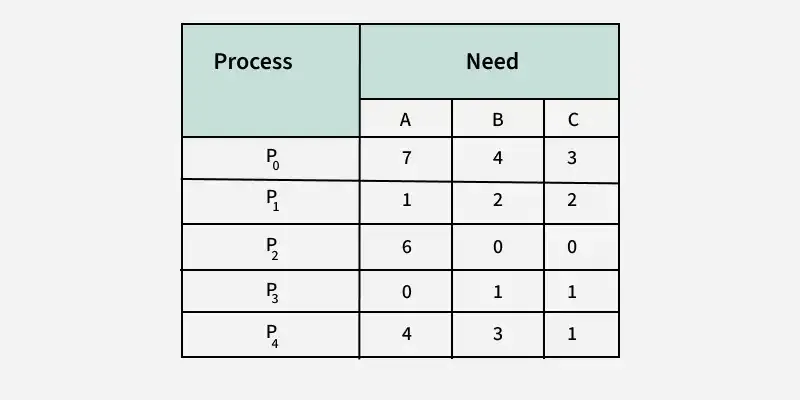
Q.2 Is the system in a safe state? If Yes, then what is the safe sequence?
Applying the Safety algorithm on the given system,
Q.3 What will happen if process P1 requests one additional instance of resource type A and two instances of resource type C?

We must determine whether this new system state is safe. To do so, we again execute Safety algorithm on the above data structures.
Hence the new system state is safe, so we can immediately grant the request for process P1 .
Unsafe State in The Bankers Algorithm
In the context of the Banker's Algorithm, an unsafe state refers to a situation in which, all processes in a system currently hold resources within their maximum needs, there is no guarantee that the system can avoid a deadlock in the future. This state is contrasted with a safe state, where there exists a sequence of resource allocation and deallocation that guarantees that all processes can complete without leading to a deadlock.
Key Concepts in Banker's Algorithm
- Safe State: There exists at least one sequence of processes such that each process can obtain the needed resources, complete its execution, release its resources, and thus allow other processes to eventually complete without entering a deadlock.
- Unsafe State: Even though the system can still allocate resources to some processes, there is no guarantee that all processes can finish without potentially causing a deadlock.
Example of Unsafe State
Consider a system with three processes (P1, P2, P3) and 6 instances of a resource. Let's say:
- The available instances of the resource are: 1
- The current allocation of resources to processes is:
- The maximum demand (maximum resources each process may eventually request) is:
In this situation:
Need = Maximum Demand - Allocation
Process | Maximum Demand | Allocation | Need |
|---|
P1 | 4 | 2 | 2 |
P2 | 5 | 3 | 2 |
P3 | 3 | 1 | 2 |
P1 may need 2 more resources to complete.P2 may need 2 more resource to complete.P3 may need 2 more resources to complete.
However, there is only 1 resource available. Even though none of the processes are currently deadlocked, the system is in an unsafe state because there is no sequence of resource allocation that guarantees all processes can complete.
Code Implementation
Similar Reads
CPU Scheduling in Operating Systems CPU scheduling is a process used by the operating system to decide which task or process gets to use the CPU at a particular time. This is important because a CPU can only handle one task at a time, but there are usually many tasks that need to be processed. The following are different purposes of a
8 min read
Preemptive and Non-Preemptive Scheduling In operating systems, scheduling is the method by which processes are given access the CPU. Efficient scheduling is essential for optimal system performance and user experience. There are two primary types of CPU scheduling: preemptive and non-preemptive. Understanding the differences between preemp
5 min read
Starvation and Aging in Operating Systems Starvation occurs when a process in the OS runs out of resources because other processes are using it. This is a problem with resource management while Operating systems employ aging as a scheduling approach to keep them from starving. It is one of the most common scheduling algorithms in batch syst
6 min read
Introduction of System Call A system call is a programmatic way in which a computer program requests a service from the kernel of the operating system on which it is executed. A system call is a way for programs to interact with the operating system. A computer program makes a system call when it requests the operating system'
11 min read
Difference between User Level thread and Kernel Level thread User-level threads are threads that are managed entirely by the user-level thread library, without any direct intervention from the operating system's kernel, whereas, Kernel-level threads are threads that are managed directly by the operating system's kernel. In this article, we will see the overvi
5 min read
Introduction of Process Synchronization Process Synchronization is used in a computer system to ensure that multiple processes or threads can run concurrently without interfering with each other.The main objective of process synchronization is to ensure that multiple processes access shared resources without interfering with each other an
10 min read
Critical Section in Synchronization A critical section is a segment of a program where shared resources, such as memory, files, or ports, are accessed by multiple processes or threads. To prevent issues like data inconsistency and race conditions, synchronization techniques ensure that only one process or thread accesses the critical
8 min read
Inter Process Communication (IPC) Processes need to communicate with each other in many situations. Inter-Process Communication or IPC is a mechanism that allows processes to communicate. It helps processes synchronize their activities, share information, and avoid conflicts while accessing shared resources.Types of Process Let us f
5 min read
Semaphores in Process Synchronization Semaphores are a tool used in operating systems to help manage how different processes (or programs) share resources, like memory or data, without causing conflicts. A semaphore is a special kind of synchronization data that can be used only through specific synchronization primitives. Semaphores ar
15+ min read
Mutex vs Semaphore In the Operating System, Mutex and Semaphores are kernel resources that provide synchronization services (also known as synchronization primitives). Synchronization is required when multiple processes are executing concurrently, to avoid conflicts between processes using shared resources. In this ar
8 min read