Amazon Web Services - Restricting S3 Access Only From CloudFront
Last Updated :
28 Mar, 2023
In this article, we will look into how to restrict access to Simple Storage Service (S3) from CloudFront only. When developers are using S3 REST API endpoint as the origin to CloudFront, they can restrict access to S3 from CloudFront only by setting up the Origin Access Identity(OAI). This is a special CloudFront user, which they will associate with the distribution.
Users can then add permissions on the S3 bucket, or the objects in an S3 bucket, to allow access only to this origin access identity. When the user accesses the S3 object through CloudFront, the origin access identity gets the object on behalf of the users. If the users try to access the S3 URL directly, their access is denied.
This makes sure that the client can access objects in the S3 bucket but only by CloudFront. This is an additional layer of security and customers can control traffic by integrating WAF with CloudFront to secure their websites.
To create a closure on Origin access identity using the CloudFront console follow the below steps:
Step 1: Login to the AWS management console and go to CloudFront console:

Step 2: Select the distribution ID you want to add origin access identity
.

Step 3: Then change to Edit mode and choose the Origins tab and then select the S3 origin that you want to edit.

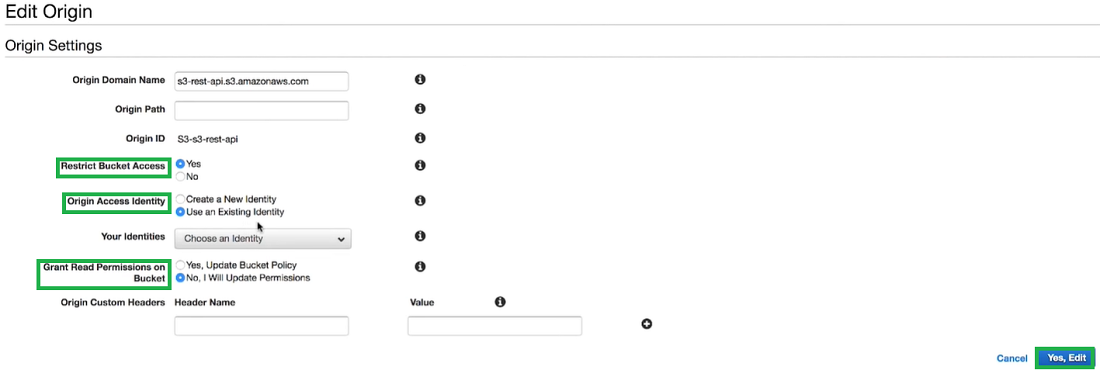
Step 4: For Restrict Bucket Access click Yes, if you already have OAI you can choose the existing identity or you can create a new one. Here we will be choosing the existing identity, then to have CloudFront automatically update the origin access identity permission to read the objects in the S3 bucket specified in the origin domain name choose Yes, Update Bucket Policy and then click Yes, Edit.
Step 5: Now we can check if the bucket policy's updated in the S3 bucket. To do that open S3 console in a new tab, click the S3 bucket, which is the origin of the CloudFront distribution.

Step 6: Select the permissions tab and choose bucket policy. The bucket policy is set to allow access to origin access identity associated with the CloudFront distribution.

Now if we try accessing the S3 object by directly accessing the S3 URL, we can see there is an access denied error so the user will have access to the S3 object by only CloudFront.

Similar Reads
Amazon Web Services - Correctly Accessing CloudFront from Amazon S3 Sometimes users of Amazon Cloudfront get a 403 Access Denied error when using an Amazon S3 website endpoint as an origin in Amazon CloudFront distribution. So, in this article, we will work through resolving this error. To resolve the Access Denied Error follow the below steps: Step 1: After signing
2 min read
Amazon Web Services - Introduction to CloudFront CDN Amazon CloudFront is a global web service that allows you to securely deliver content to your users with low latency and high availability. It does so by further delivering content safely. This service helps to built high performance and security in your application. CloudFront works for both static
3 min read
Amazon Web Services - Amazon S3 Notifications to SNS In this article, we will see how the Amazon S3 bucket publishes notifications to SNS topics on object creation events. An object that creates an event is of four types. They are Put, Post, Copy, Multipart Upload, Remove, Replicate and Restore. Thus, whenever any of the event occur in our S3 bucket,
3 min read
Amazon Web Services - Identities When you will create your AWS account by submitting your credentials(e.g. email id, credit card/debit card details) it is called a root user account. The root user has access to all AWS services and resources in the account. Hence, Identity Access Management(IAM) system helps root users to create di
6 min read
Amazon Web Services - Introduction to Amazon FSx In this article, we will look into Amazon's fully managed native File Server service called Amazon FSx, and it is integrated with the rest of AWS. So what does fully managed mean? It means that you no longer need to manage the hardware or the software to provide File server services to your users. A
5 min read
Amazon Web Services - Denying Access using IAM policy for EC2 and EBS Instance In this article, we will look into how to use AWS identity and access management policy conditions to create an IAM policy that denies access to create amazon elastic compute cloud instances and amazon elastic block store volumes when the required tags are not passed along with the creation request.
4 min read