Why does DNS use UDP?
If you have ever wondered why DNS primarily relies on UDP (User Datagram Protocol) instead of other...
Routing Information Protocol: Explaining One of the Oldest Routing Protocols
Routing Information Protocol (RIP) is one of the first dynamic routing protocols ever developed. While it’s no longer the top choice...
DMARC, the solution for your phishing problems
DMARC emerges as the solution for phishing attacks that are a real danger for every business. They can severely damage the brand name, and...
BIND Explained: A Powerful Tool for DNS Management
Welcome to the fascinating world of BIND – the force behind the seamless web browsing...
DNS vs DHCP. Are they connected?
In networking, two fundamental protocols are vital in connecting devices and enabling seamless communication: DNS (Domain Name System) and...
DDoS amplification attacks by Memcached
In our increasingly interconnected world, cybersecurity threats continue to evolve, and one particularly concerning method is the Memcached...
What is Cybersquatting and Why Should You Care?
In the digital age, a strong online presence is essential for businesses, influencers, and...
DNS Troubleshooting – tools and commands
In the vast universe of network management and IT troubleshooting, issues related to the Domain Name System (DNS) often crop up. DNS is a...
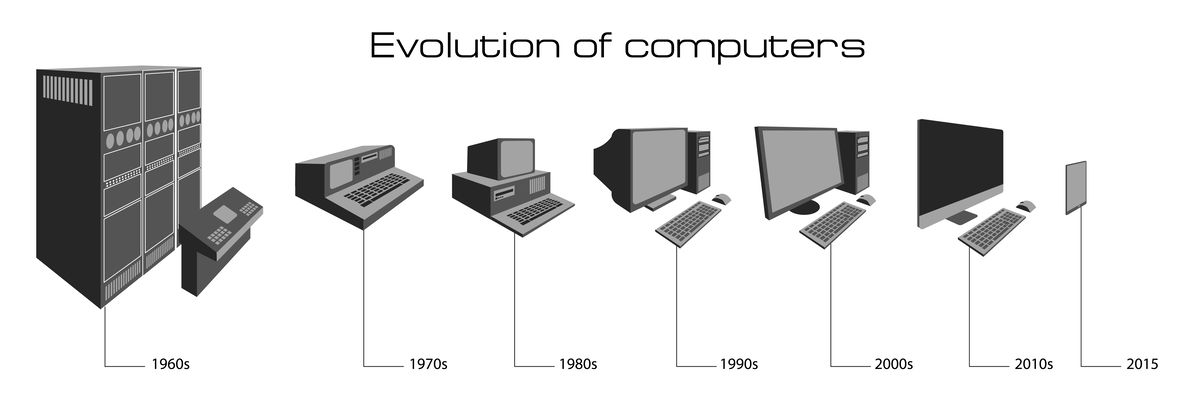
DNS history. When and why was DNS created?
We have talked a lot about DNS. How does it work, and all the related topic around it. But we have never spent some time about the DNS...
ccTLD – Building Trust and Credibility with Country-Specific Domains
In today’s globalized world, establishing trust and credibility is paramount for any company...