KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Cyberattacks have been escalating, driven by evolving tactics and technologies that were previously exclusive to state actors but are now widespread among cybercriminals. Global supply chains and organizations, already weakened by the Covid-19 pandemic, face heightened risks due to geopolitical tensions, demanding more sophisticated cybersecurity responses. Security Information and Event Management (SIEM) systems, while foundational, struggle with high costs, a deluge of false positives, and operational inefficiencies. The rise of Security Orchestration, Automation, and Response (SOAR) platforms aims to address these challenges by automating and streamlining incident response, augmenting SIEM capabilities with centralized coordination and enriched threat intelligence.
SOAR solutions have gained traction among large organizations needing robust, automated incident response mechanisms. These platforms integrate various security tools and provide comprehensive coverage from network to application layers, leveraging endpoint protection, cloud security, and identity management. SOAR systems, when integrated with SIEMs, effectively collect and enrich data, automate workflows, and manage incidents. The use of playbooks allows for automated responses to common security events, minimizing manual intervention and enhancing efficiency.
Furthermore, modern SOAR platforms must support seamless integration with existing security infrastructures, offer extensive API compatibility, and provide robust case management and automation capabilities. The industry's adoption of Extended Detection and Response (XDR) solutions highlights a continued evolution towards more comprehensive, integrated cybersecurity architectures.
Given the current cybersecurity landscape, every organization must urgently enhance its infrastructure and equip Security Operations Centers (SOC) with advanced tools. Vendors are expanding SOAR capabilities to ensure effective threat detection, analysis, and response, forming the backbone of contemporary security operations frameworks.
Cyberattacks have been intensifying over the past few years as cybercriminals continue to devise new strategies to launch sophisticated attacks and gain unauthorized access. The tactics, techniques, and procedures (TTPs) that were once only used by well-funded state actors are being commoditized by cybercriminals. As a result, some vendors realized that the traditional approaches and tools of cybersecurity have failed to keep up.
Global supply chains and private organizations, which are already in a precarious state due to the Covid-19 pandemic, are facing an increased risk of cyber-attacks as a result of geopolitical instability. To stay secure and compliant, organizations need to actively seek out new ways to assess and respond to cyber threats while providing Security Operations Centers (SOC) analysts with the right tools.
Large organizations, whether they are part of critical infrastructure or not, need to be able to detect and respond to incidents by monitoring security and analyzing real-time events. Security Information and Event Management (SIEM) products were once hailed as the ultimate solution for managing security operations. In many organizations, they still form the foundation of modern SOCs. However, visibility of potential security events alone does not help analysts to assess each discovered threat, nor does it reduce the amount of time spent on repetitive manual tasks in incident response processes.
High deployment and operational costs, lack of intelligence to react to modern cyberthreats, and the growing skills gap to staff the security teams needed for efficient security operations were the most common problems of legacy SIEM tools. SIEMs did and still do provide value, but some SIEM users report that the volume of false positives causes problems in trying to sift out what is worthy of attention and follow-up and what is not.
Parallel to SIEM solutions, a class of incident investigation and response platforms has emerged focusing on creating more streamlined and automated workflows for dealing with security incidents. Security Orchestration, Automation, and Response (SOAR) products are the latest iteration of this evolution. SOAR vendors provide solutions that offer centralized coordination, collaboration, and management for forensic analysis and incident response.
Driven by the growing demand to implement centralized, automated control over incident analysis and response workflows across disparate security solutions, vendors are expanding their existing security intelligence, security orchestration, or incident response platforms to combine the key capabilities across all three of these market segments.
Complementing or directly integrating with SIEMs, SOAR platforms aim to become the foundation of contemporary SOCs. Large organizations were the early adopters of SOAR solutions as they were more susceptible to cyberattacks. Whether or not your organization has a mature and established SOC, SOAR capabilities have the potential to augment SIEM/SOC deployments beyond the detection stage.
Modern cybersecurity architectures must include tools and services that cover everything from the network layer to the application layer and all the devices in between. Network layer security tools include firewalls, VPNs, routers/switches, Software Defined Networking (SDN) control planes, Intrusion Detection and Prevention Systems (IDS/IPS), email gateways, web gateways, Network Detection & Response (NDR) solutions, and Distributed Deception Platforms (DDPs). Associated cloud resources should have Cloud Access Security Brokers (CASBs) for both network and application layer controls, and Cloud Workload Protection Platforms (CWPPs) to secure workloads in IaaS and PaaS.
Endpoints need Endpoint Protection (EPP) suites and Endpoint Detection & Response (EDR) capabilities. EPP should contain a multiplicity of security functions: advanced anti-malware agents that can proactively discover and prevent malware from executing, utilizing ML-enhanced behavioral and memory analysis, exploit prevention, and other measures. EPP should also perform application control, integrate with or provide endpoint firewall protection, URL filtering, critical system file monitoring, asset inventory and patch management, and vulnerability management. EDR solutions have deeper monitoring and analysis functions that look for signs of attacks on endpoints that may have gone unnoticed by EPP. EDR should have automatic analysis and remediation capabilities. All kinds of endpoints should be considered, not just desktops and laptops, but also servers, virtual servers, containers, mobile phones, and IoT devices. Most vendors now offer Endpoint Protection Detection & Response (EPDR) tools that combine EPP and EDR.
Application security starts with secure coding practices. Nevertheless, additional security mechanisms are needed and when deployed can help protect apps from attacks. Defenses at the application layer may include protocol gateways, reverse proxies, API gateways, and Web Application Firewalls (WAFs). CASB and CWPP solutions are useful for cloud hosted applications.
Databases, Big Data systems, data lakes, and data analytics tools must be considered. Databases have built-in security constructs that must be employed to control access and protect against sabotage. SQL database security is well established but can be harmonized with enterprise security policies using SQL proxies and API security gateways. Big Data tools and related storage units require a mix of application, network, and cloud security tools for proper coverage.
Last but certainly not least is identity. We have heard for years that “Identity is the new perimeter”. This means that Identity and Access Management (IAM) systems play a critical role in the overall security architecture. Traditional security perimeters have become more porous over the years to allow higher level traffic to communicate directly with business or mission-critical applications. Digital identity is what allows for better protection of all resources along the path from “outside” to “inside”, by enforcing strong authentication and granular authorization. Thus, IAM concepts, systems, and controls must pervade all digital environments.
SOAR systems can be fed by all these kinds of security solutions, albeit indirectly through the aforementioned SIEMs. SOARs that are tightly integrated with SIEMs can take in telemetry via APIs or in CEF and syslog format. SOAR systems generally have OOTB connectors (software configurations and code in the form of packaged API calls) to facilitate data collection from upstream sources. In some cases, analysts need access to full packet captures, so NetFlow and PCAP are supported by some vendors. In those cases, vendors have appliances that can connect on SPAN/TAP ports on network devices to achieve full packet capture.
The orchestration aspect of SOAR involves not only the collection of telemetry from these different sources, but also initiating a workflow, opening cases and tickets where appropriate, and correlation and enrichment of event information. Many large organizations, especially the type looking for SOAR systems, have IT Service Management (ITSM) Suites that dispatch and track activities in the form of tickets. SOAR solutions have case management capabilities by design, but they must also interoperate with existing ITSM solutions.
For example, a ransomware attack will generate alerts from one or more endpoints and possibly network monitoring and data storage monitoring systems. SOAR’s job is to distinguish between related and unrelated events across all connected systems, assemble it coherently, enrich the event information by acquiring additional intelligence about observed entities (files, URLs, IP addresses, user accounts, etc.), create and/or coordinate tickets with ITSMs, with the goal of assisting human analysts and/or taking pre-programmed responses in playbooks.
Enrichment of event data can be facilitated by SOAR systems by the automatic collection of additional forensic evidence on-site, such as outputs of EPP scans, obtaining non-standard log files, memory dumps, etc. Some vendor solutions can kick off somewhat automated threat hunts (looking for IOCs across multiple nodes in an environment) and add the results to preliminary investigation. SOAR solutions should also be able to generate queries to threat intelligence sources based on suspicious items and patterns observed from upstream telemetry.
Some vendors have extensive threat intelligence capabilities which are utilized by their SOAR solutions. External threat intelligence sources may and ideally should be used to supplement internal threat intel sources. Examples of threat intelligence content include IOCs (files, hashes, IPs, URLs, and so forth), compromised credential intelligence, device intelligence (often from Mobile Network Operators [MNOs]), and domain/file/IP/URL reputation information. Ideally SOAR solutions will accomplish all the foregoing actions automatically prior to or while alerting a human analyst.
When an analyst is alerted and assigned a case, all pertinent information related to the event should be constructed and presented by the SOAR platform to the analysts for their investigation. The SOAR platform should package information coherently, with descriptions and recommendations for actions.
Most SOAR vendors adhere to the paradigm of a playbook, sometimes called a runbook. Playbooks typically address common security scenarios and can be triggered either by manual analyst action or automatically if allowed by policy and supported by the vendor. Examples of security events that may trigger playbooks are phishing, malware, ransomware, failed login attempts, excessive or abnormal use of privileged credentials, prohibited communication attempts, attempts to access unauthorized resources, file copying or moving, attempts to transfer data using unauthorized webmail providers, attempts to transfer data to blocked IPs or URLs, unusual process launches, unusual application to network port activities, unusual network communication patterns, and so on. The end goal of SOAR is to be able to automate incident responses among the various security systems. To this end, SOAR platforms often support dozens to hundreds of playbook scenarios and offer hundreds to thousands of possible incident response actions.
Given the current geopolitical climate, every organization must act with extreme urgency to secure its information technology infrastructure. As rogue nations continue to foster an environment for cybercriminals and ransomware attackers to thrive, organizations need to be prepared and build a strong security foundation while providing SOC analysts with the right tools.
As a result, some vendors have recently started to adopt Extended Detection and Response (XDR) solutions. XDR has been considered as the next evolution of EDR because it takes a holistic approach to threat detection and response that facilitates data ingestion, analysis, and prevention workflows across an organization’s IT infrastructure. Although XDR is intended to be “SOAR-like”, SOAR is still relevant and appropriate for large organizations that have SOCs and those that have taken a best of breed security architecture approach. SOAR can be beneficial and help bring those best of breed products together in a unified way.
Ultimately, the selection of any SOAR solution will depend on the organization’s particular requirements, which depend strongly on the currently deployed and planned IT security and IAM infrastructure. Careful consideration must be given to evaluating which SOAR solutions have integrations for the tools in use and on the roadmap. The maximum utility is achieved by selecting a SOAR that has pre-packaged connectors for all the security and identity elements in your portfolio.
As the number and sophistication of cyberattacks have continued to increase over the years, organizations need to be prepared and build a strong security foundation while providing SOC analysts with the right tools.
SOAR products have been driven by the growing demand to distinguish between related and unrelated events across all connected systems, enrich the event information by acquiring additional intelligence, create and/or coordinate tickets with ITSMs, and assist human analysts with pre-programmed responses in playbooks.
The SOAR market is mature and as such has a reasonably well-defined terminology and includes capabilities such as data collection, correlation, enrichment, orchestration, automation, and incident response and mitigation.
Some vendors provide SOAR as a service for their customers, and most license their products to Managed Security Service Providers (MSSPs) who run it on behalf of their customers.
SOAR vendors deliver solutions that often require complex on-premises deployments. However, SOAR systems also offer support for various cloud hosted environments such as IaaS, PaaS, and SaaS applications as well.
The selection of any SOAR solution will depend on the organization’s particular requirements, which depend strongly on the currently deployed and planned IT security and IAM infrastructure.
The Overall Leaders (in alphabetical order) are D3 Security, Fortinet, IBM Security, Logpoint, Microsoft, Palo Alto Networks, Splunk, and ServiceNow.
The Product Leaders (in alphabetical order) are D3 Security, Fortinet, IBM Security, Logpoint, Microsoft, Palo Alto Networks, ServiceNow, Splunk, Swimlane, and ThreatQuotient.
The Innovation Leaders (in alphabetical order) are Fortinet, IBM Security, Logpoint, Palo Alto Networks, and ServiceNow.
The Market Leaders (in alphabetical order) are Fortinet, IBM Security, Microsoft, Palo Alto Networks, ServiceNow, and Splunk.
The SOAR market is mature and as such has a reasonably well-established terminology and core set of capabilities. The term “SOAR” itself is embraced by many vendors.
Some vendors in the market started out with a mission to address what they saw as missing functionality in the broader cybersecurity market. These start-ups may have gone through several rounds of funding and grown a sizable customer base. Furthermore, some of the bigger specialty start-ups in the SOAR market have been acquired by large cybersecurity stack vendors who were desirous to add these types of capabilities to their already extensive suites of products and services. In other cases, SOAR has been an outgrowth to complementary product offerings (most commonly SIEM) at some of the mid-tier vendors in the market.
Customers in the SOAR market tend to be somewhat mid-sized businesses, enterprises, and government agencies. Organizations that have established IT security departments, especially those with SOCs, are the most likely to see a need for SOAR. SMBs and some enterprises that are either outsourcing IT functions or adding security capabilities but not adding staff are turning to MSSP options that have SOAR.
The SOAR market is valid globally, but the greatest uptake has been in North America, followed by Europe. However, many companies are expanding into the APAC region. This region comprises some of the world’s largest economies, such as China, India, Japan, Singapore, and Australia. With the threat landscape constantly changing, cyber threats experienced by organizations in these countries are increasing at an alarming rate. We expect to see more organizations across the world adding SOAR to their cybersecurity portfolios in the years ahead. SOAR as an outsourced function provided by MSSPs is also likely to grow in popularity.
SOAR solutions often require complex deployment models. In most cases, on-premises components must be implemented, including software agents and API connectivity for upstream security systems from which telemetry will be gathered, and appliances and/or virtual appliances that serve as collection, analysis, operational, and management nodes for the SOAR solution.
Over the past few years, digital transformation has been driving organizations to adopt cloud-based solutions and change their operating models. SOAR systems also generally provide support for various cloud hosted environments such as IaaS and PaaS, which requires agents or images to be installed or the use of customized APIs. Some support specific SaaS applications as well. Cloud-based deployment offers several benefits to organizations, such as scalability and agility, reduced physical infrastructure, less maintenance cost, flexibility, and continuous accessibility of data.
In addition to APIs and connectors for security tools, SOAR platforms have user interfaces for administrators and analysts. Some vendors offer this as a capability on the components installed on-premises and others offer it as a cloud-hosted service.
Nevertheless, it’s worth reiterating that we expect a Security Orchestration, Automation, and Response platform to implement all three of the core set of capabilities mentioned below:
Security data collection, correlation, and enrichment: a SOAR platform can collect historical and real-time security data either on its own or ingest security events from a SIEM solution. The data should be enriched with additional business context, external threat intelligence, or other data sources according to established workflows.
Security Orchestration and Automation: a SOAR platform should implement comprehensive workflow management capabilities to ensure that tasks across multiple environments and security tools can be efficiently coordinated. Whenever possible, repetitive parts of these workflows should be automated to free the analyst’s time for more creative tasks. For manual steps, intelligent guidance and decision support capabilities are a major plus.
Incident Response and mitigation: for identified security incidents, a SOAR platform should be able to offer a range of predefined resolutions: ranging from simple actions like creating a ticket for manual processing or blocking an infected machine in a firewall to more sophisticated playbooks that coordinate response processes across multiple departments: from IT to legal and public relations.
The specific set of features we consider in SOAR solutions are:
We are looking for vendors that only cover full-featured and mature SOAR products and solutions. Vendors that only focus on a specific IT environment or a subset of security information will be excluded from this list.
However, there are no further exclusion criteria such as revenue or number of customers. We cover vendors from all regions, from start-ups to large companies.
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Leadership Compass. The Leadership Compass provides a comparison based on standardized criteria and can help identifying vendors that shall be further evaluated. However, a thorough selection includes a subsequent detailed analysis and a Proof of Concept of pilot phase, based on the specific criteria of the customer.
Based on our rating, we created the various Leadership ratings. The Overall Leadership rating provides a combined view of the ratings for
The Overall Leadership rating provides a consolidated view of all-around functionality, innovation, market presence, and financial position. However, these vendors may differ significantly from each other in terms of product features, platform support, and integrations. Therefore, we strongly recommend looking at all the leadership categories as well as each entry in chapter 5 to get a comprehensive understanding of the players in this market and what use cases they support best.
The Overall Leadership chart is linear, with Followers appearing on the left side, Challengers in the center, and Leaders on the right.
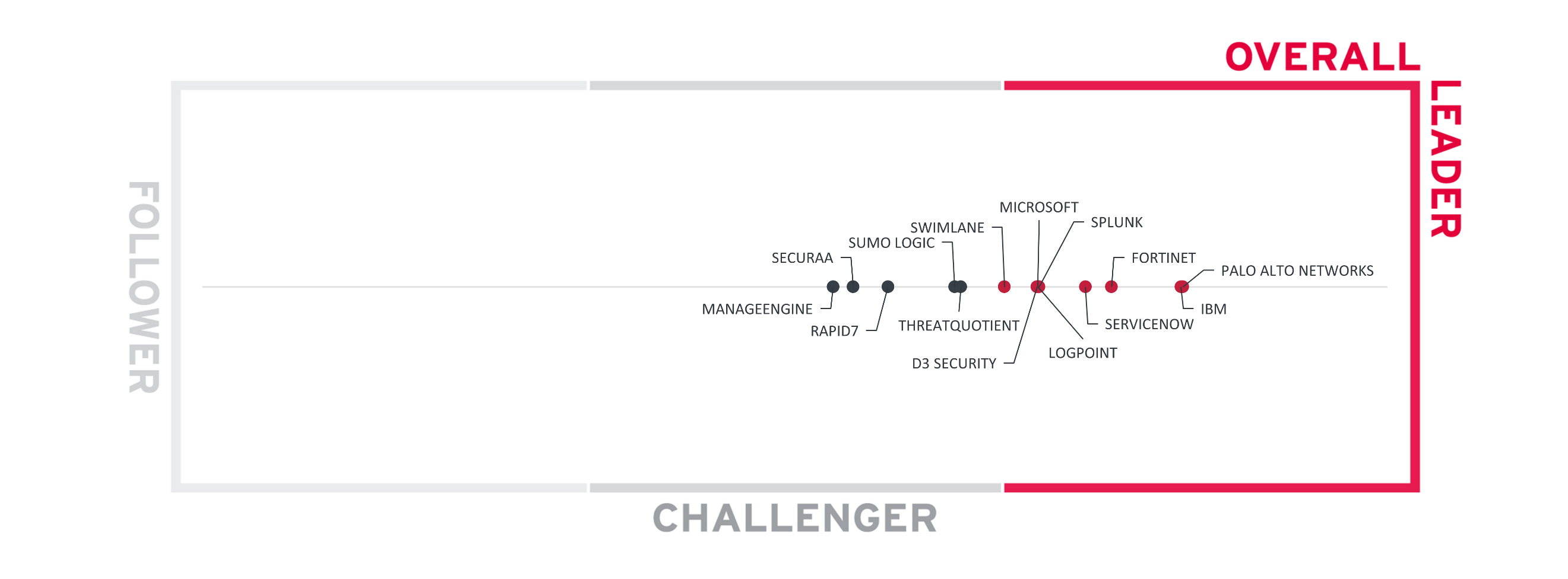
Figure 1: The Overall Leaders in the Leadership Compass SOAR
The Overall Leaders are (in alphabetical order):
The Overall Challengers are (in alphabetical order): ManageEngine, Rapid7, Securaa, Sumo Logic, and ThreatQuotient.
Product Leadership is the first specific category examined below. This view is mainly based on the presence and completeness of required features as defined in the Required Capabilities section above. The vertical axis shows the product strength plotted against the combined/overall strength on the horizontal axis. The Product Leadership Chart is rectangular and divided into thirds. Product Leaders occupy the top section. Challengers are in the center. Followers are in the lower section.
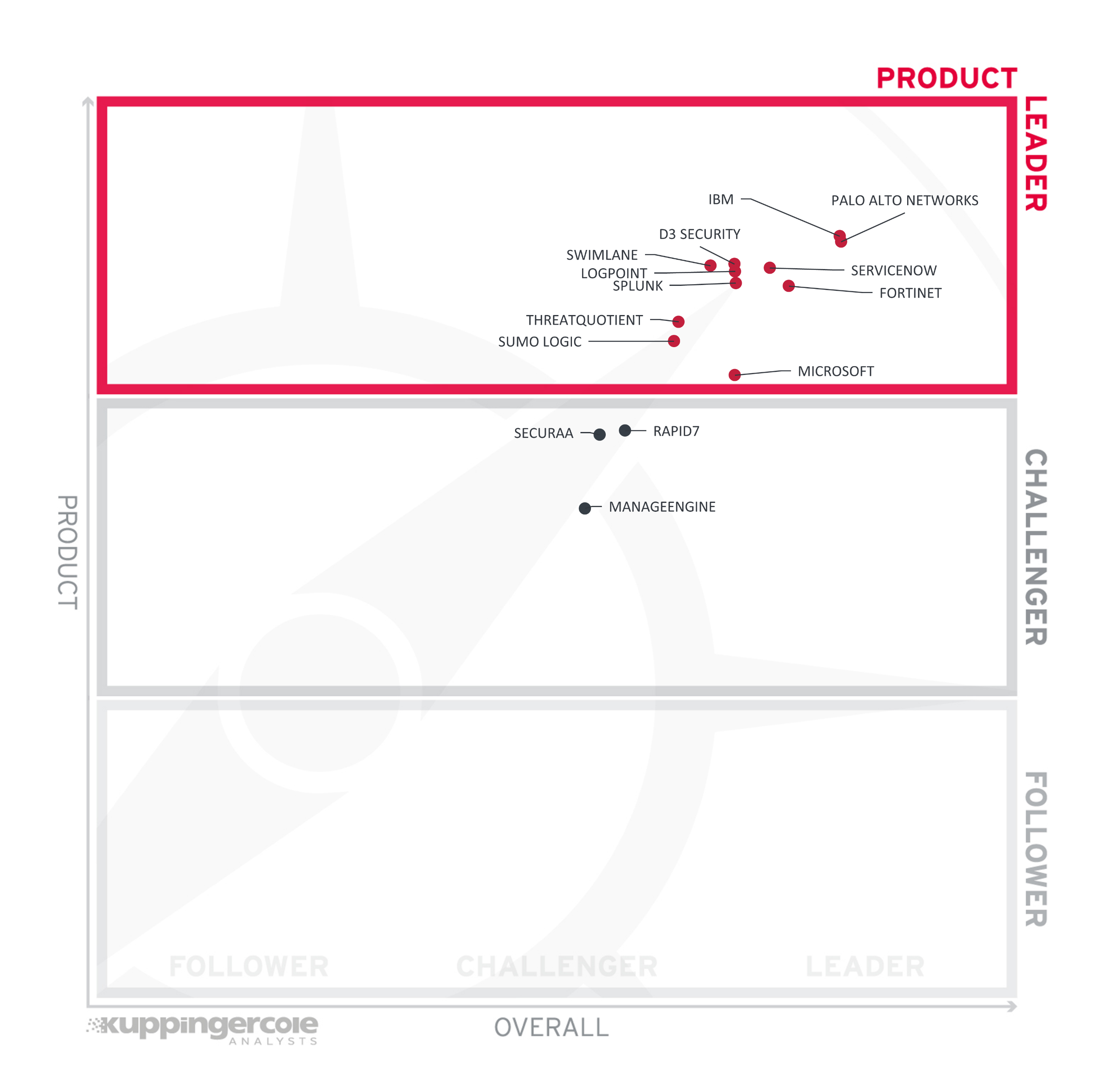
Figure 2: The Product Leaders in the Leadership Compass SOAR
All vendors in the Product Leadership deliver leading-edge capabilities across the depth and breadth of the SOAR capability spectrum evaluated for the purpose of scoring the vendors in this Leadership Compass. However, we can also observe several much smaller vendors among the leaders, which nevertheless are able to offer their solutions with comprehensive capabilities, flexible deployment options and lower operational complexity than the market giants.
Product Leaders (in alphabetical order):
The Product Challengers are (in alphabetical order): ManageEngine, Rapid7, and Securaa. All these vendors have striking offerings but lack certain advanced capabilities that we expect to see, either in the depth or breadth of functionalities seen in the Leadership segment offerings. There are no Followers in the Product Leadership rating.
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements. Innovation is not about delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
This view is mainly based on the evaluation of innovative features, services, and/or technical approaches as defined in the Required Capabilities section. The vertical axis shows the amount of innovation plotted against the combined/overall strength on the horizontal axis. The Innovation Leadership Chart is rectangular and divided into thirds. Innovation Leaders occupy the top section. Challengers are in the center. Followers are in the lower section.
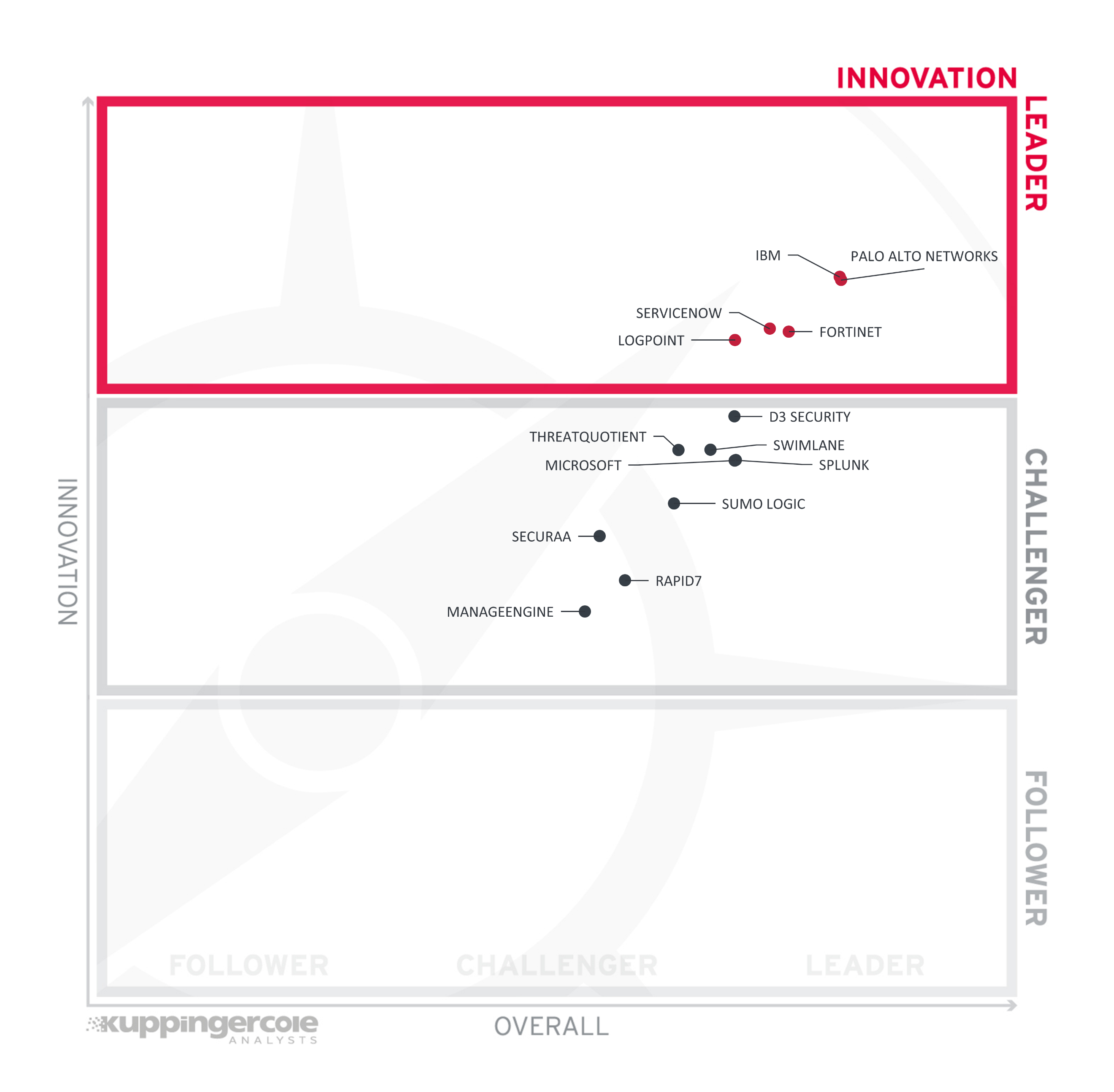
Figure 3: The Innovation Leaders in the Leadership Compass SOAR
Innovation Leaders are those vendors that are delivering cutting edge products, not only at customer request but also because they are driving the technical changes in the market by anticipating what will be needed in the months and years ahead. There is a strong correlation between the Overall, Product, and Innovation Leaders, which demonstrates that leadership requires feature-rich products that are looking over the horizon to bring advancements to help their customers.
Innovation Leaders (in alphabetical order):
The Innovation Challengers are (in alphabetical order): D3 Security, ManageEngine, Microsoft, Rapid7, Securaa, Splunk, Sumo Logic, Swimlane, and ThreatQuotient. These companies also have some specific innovations that make their offerings attractive to their customers but lack the breadth of innovation that other vendors demonstrate.
Lastly, we analyze Market Leadership. This is an amalgamation of the number of customers, the geographic distribution of customers, the size of deployments and services, the size and geographic distribution of the partner ecosystem, and financial health of the participating companies. Market Leadership, from our point of view, requires global reach.
The vertical axis shows the market strength plotted against the combined/overall strength on the horizontal axis. The Market Leadership Chart is rectangular and divided into thirds. Market Leaders occupy the top section. Challengers are in the center. Followers are in the lower section.
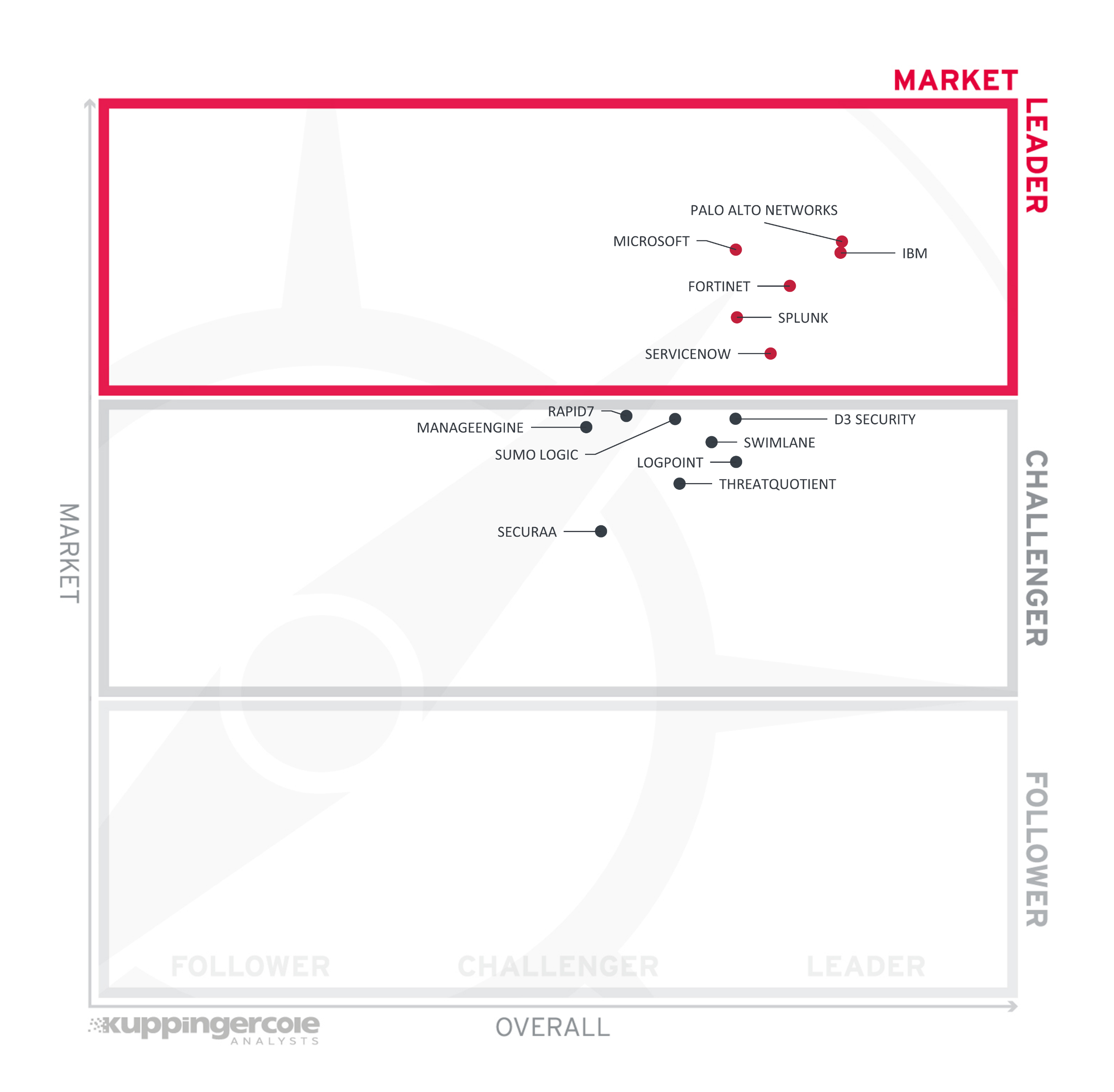
Figure 4: The Market Leaders in the Leadership Compass SOAR
Market Leadership is a combined measure of customers, managed users, partners, the geographic distribution of customers, support, and partners, and overall financial position. These vendors have financial strength, geographic distribution of customers and partner, and extensive ecosystems of system integrators.
Market Leaders (in alphabetical order):
The Market Challengers are (in alphabetical order): D3 Security, Logpoint, ManageEngine, Rapid7, Securaa, Sumo Logic, Swimlane, and ThreatQuotient. Some of these vendors are relatively young, lack a comprehensive global presence, focus mainly on their home markets, or are still in their growth phase.
While the Leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader, but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the Product Leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various Leadership categories and delivers an additional level of information and insight.
The following charts are rectangular and divided into nine equal sections. A dashed line intersects the rectangle at the point where x- and y-axis values are equal.
The first of these correlated views contrasts Product Leadership and Market Leadership.
The vertical axis represents the market position plotted against product strength rating on the horizontal axis.

Figure 5: The Market/Product Matrix for Leadership Compass SOAR
This comparison shows which vendors are better positioned in our Product Leadership analysis than their position in the Market Leadership analysis. Vendors above the line are somewhat "overperforming" in the market. It comes as no surprise that these are often very large vendors, while vendors below the line may more often be innovative but focused on specific regions as an example.
In the upper right segment, we find "Market Champions". Given that the SOAR market is mature, we see Palo Alto Networks, Microsoft, IBM, Fortinet, Splunk, and ServiceNow as market champions positioned in the top right-hand box.
In the middle right-hand box, we see five vendors that deliver strong product capabilities for SOAR but are not yet considered Market Champions. D3 Security, Logpoint, Sumo Logic, Swimlane, and ThreatQuotient have a strong potential to improve their market position due to the more robust product capabilities they are already delivering.
In the middle of the chart, we see the vendors that provide good but not leading-edge capabilities and therefore are not market leaders. These vendors include ManageEngine, Rapid7, and Securaa. They also have moderate market success as compared to market champions. However, we believe that each has a chance for significant growth. For example, Securaa has a strong market position in the APAC region, while Rapid7 has a significant presence in North America as well as growing presence in Europe.
This view shows how Product Leadership and Innovation Leadership are correlated. It is not surprising that there is a pretty good correlation between the two views with a few exceptions. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
The vertical axis represents the product strength rating plotted against innovation on the horizontal axis.
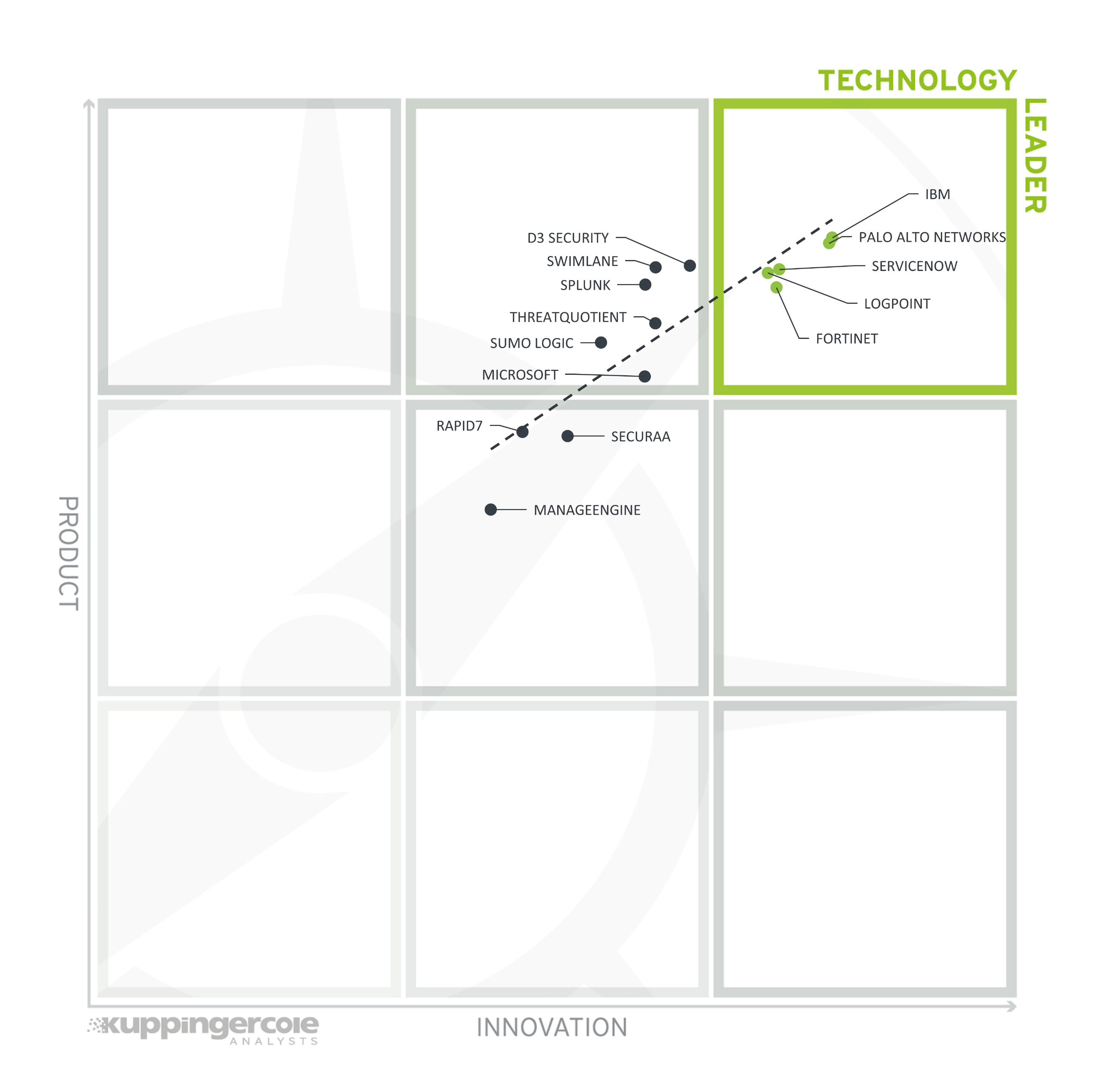
Figure 6: The Product/Innovation Matrix for Leadership Compass SOAR
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative.
Here, we see a good correlation between the product and innovation rating. Many vendors placed close to the dotted line, indicating a healthy mix of product and innovation leadership in the market. Looking at the Technology Leaders segment, we find most leading vendors scattered throughout the box in the upper right corner. The leading vendors are (in alphabetical order) Fortinet, IBM, Logpoint, Palo Alto Networks, and ServiceNow. IBM Security is placed closest to the axis depicting a good balance of product features and innovation. Palo Alto Networks, Fortinet, Logpoint, and ServiceNow are following closely behind. While these vendors all take different approaches for delivering a SOAR platform, all perform well in both the current product offering and the innovation they demonstrate.
Six vendors appear in the top middle box with good products but less innovation than the leaders, including D3 Security, Microsoft, Splunk, Sumo Logic, Swimlane, and ThreatQuotient. Several vendors appear in the middle box, showing both innovation and product capabilities. However, they remain at a Challenger level in both product and innovation ratings. These vendors include (in alphabetical order) ManageEngine, Rapid7, and Securaa. These vendors have a strong potential in further increasing their position in the SOAR market.
The third matrix shows how Innovation Leadership and Market Leadership are related. Some vendors might perform well in the market without being Innovation Leaders. This might impose a risk for their future position in the market, depending on how they improve their Innovation Leadership position. On the other hand, vendors which are highly innovative have a good chance for improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
The vertical axis represents the market position rating plotted against innovation on the horizontal axis.
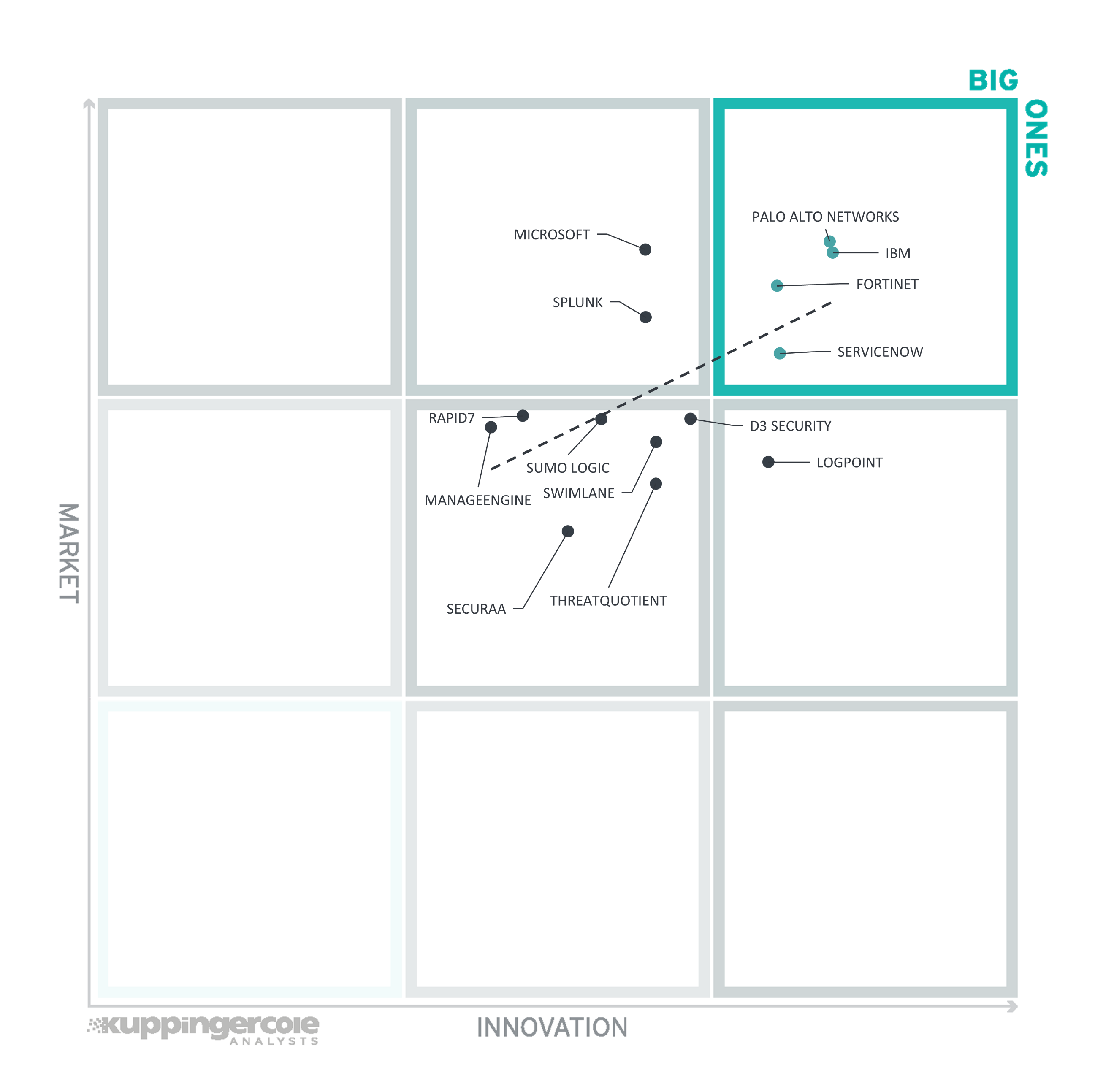
Figure 7: The Innovation/Market Matrix for Leadership Compass SOAR
Vendors above the line are performing well in the market as well as showing Innovation Leadership; while vendors below the line show an ability to innovate though having less market share, and thus the biggest potential for improving their market position.
In the upper right-hand corner box, we find the "Big Ones" in the SOAR market. We see (in alphabetical order) Fortinet, IBM, Palo Alto Networks, and ServiceNow. IBM Security and Palo Alto Networks. These companies are being rewarded by the market for the level of innovation they provide in their products and services.
Only one vendor (Logpoint) appears in the middle right box showing good innovation with slightly less market presence than the vendors in the "Big Ones" category.
Microsoft and Splunk are shown in the top middle box with a stronger market, although less innovation than the leaders. The segment in the middle of the chart contains a few of the vendors rated as challengers both for market and innovation, which includes (in alphabetical order) D3 Security, ManageEngine, Rapid7, Securaa, Sumo Logic, Swimlane, and ThreatQuotient.
This section provides an overview of the various products we have analyzed within this KuppingerCole Leadership Compass on SOAR Platforms. Aside from the rating overview, we provide additional comparisons that put Product Leadership, Innovation Leadership, and Market Leadership in relation to each other. These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1.
| Product | Security | Functionality | Deployment | Interoperability | Usability |
|---|---|---|---|---|---|
| D3 NextGen SOAR |  |
 |
 |
 |
 |
| Fortinet FortiSOAR |  |
 |
 |
 |
 |
| IBM QRadar SOAR |  |
 |
 |
 |
 |
| Logpoint SOAR |  |
 |
 |
 |
 |
| ManageEngine Log360 |  |
 |
 |
 |
 |
| Microsoft Sentinel |  |
 |
 |
 |
 |
| Palo Alto Cortex XSOAR |  |
 |
 |
 |
 |
| Rapid7 InsightConnect |  |
 |
 |
 |
 |
| Securaa |  |
 |
 |
 |
 |
| ServiceNow Security Incident Response (SIR) |  |
 |
 |
 |
 |
| Splunk SOAR |  |
 |
 |
 |
 |
| Sumo Logic Cloud SOAR |  |
 |
 |
 |
 |
| Swimlane |  |
 |
 |
 |
 |
| ThreatQuotient Platform |  |
 |
 |
 |
 |
Table 1: Comparative overview of the ratings for the product capabilities
In addition, we provide in Table 2 an overview which also contains four additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for Financial Strength applies to the vendor, the other ratings apply to the product.
| Vendor | Innovativeness | Market Position | Financial Strength | Ecosystem |
|---|---|---|---|---|
| D3 Security |  |
 |
 |
 |
| Fortinet |  |
 |
 |
 |
| IBM |  |
 |
 |
 |
| Logpoint |  |
 |
 |
 |
| ManageEngine |  |
 |
 |
 |
| Microsoft |  |
 |
 |
 |
| Palo Alto |  |
 |
 |
 |
| Rapid7 |  |
 |
 |
 |
| Securaa |  |
 |
 |
 |
| ServiceNow |  |
 |
 |
 |
| Splunk |  |
 |
 |
 |
| Sumo Logic |  |
 |
 |
 |
| Swimlane |  |
 |
 |
 |
| ThreatQuotient |  |
 |
 |
 |
Table 2: Comparative overview of the ratings for vendors
This section contains a quick rating for every product/service we’ve included in this KuppingerCole Leadership Compass document. For many of the products there are additional KuppingerCole Product Reports and Executive Views available, providing more detailed information.
Spider graphs
In addition to the ratings for our standard categories such as Product Leadership and Innovation Leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective Leadership Compass. For the LC SOAR, we look at the following six categories:
D3 Security was founded in 2002 in Vancouver, Canada. Between 2002 and 2014, the company provided incident and case management for IT security teams. D3 Security views SOAR as a pathway to fundamental improvements in the security operations of enterprises and MSSPs in finance, tech, and healthcare. Coverage is primarily focused on North America, but with growing presence in EMEA, APAC, and Latin America.
D3 Security is vendor-agnostic. NextGen SOAR is their full-scale SOAR platform and can be deployed on-premises, private cloud, public cloud, and as a service offered through MSSPs. With 500+ out-of-the-box integrations and a flexible API-based architecture, the platform aims to eliminate false positives by cross-referencing events with data held in network, firewall, SIEM logs, and DLP tools.
The platform’s Event Pipeline is an innovative feature that includes capabilities such as normalization which extracts fields, IOCs, and other data to create a clear and consistent picture of each alert. This capability also includes threat triage which enriches and rates events on severity via third-party threat intelligence sources, auto dismissal and escalation which applies rule-based filters to auto-close false-positive events, and triggers incident response playbooks. The system drastically eliminates false positives and other noise, leaving only real incidents for SOC analysts to deal with.
For playbooks, D3 NextGen SOAR comes with a library of out-of-the-box playbooks for common use cases, including NIST 800-61 and SANS methodologies. The platform does not run playbooks in a serial fashion. Instead, it runs things in parallel and compresses the time it takes for the playbook to run. In addition, the platform triggers an incident-specific playbook when a MITRE ATT&CK technique is identified by a security tool and ingested into the SOAR platform. The playbook also queries, extracts, and enriches incidents with contextual data from threat intelligence tools, and searches for related TTPs.
The platform integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Microsoft Azure Sentinel, Coralogix, Exabeam, FireEye Helix, Fortinet FortiSIEM, LogRhythm, McAfee, IBM QRadar, Rapid7, Securonix, Splunk, and Sumo Logic. D3 also supports STIX, TAXII, and YARA. D3 Security has connectors for a comparatively substantial number of other tools, and also supports all the right standards thereby enabling their customers to extend their solution as needed.
D3 Security positions itself as strong alternative to the established offerings supporting mid-market to enterprise organizations. Organizations looking for SOAR functionality, particularly those in North America should consider D3 Security. The company appears in the product leadership category.

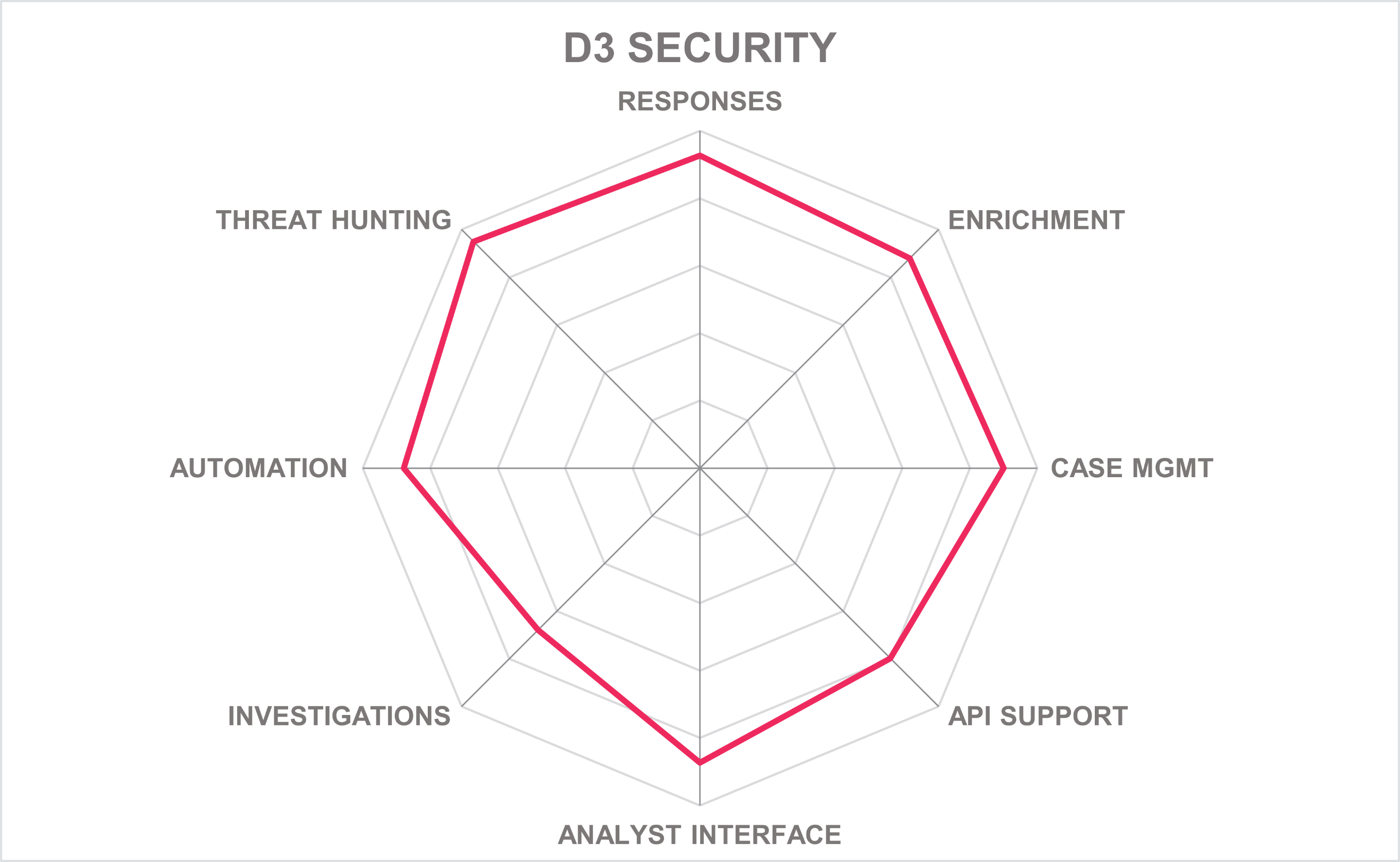
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 3: D3 Security’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Fortinet is an American cybersecurity company with headquarters in Sunnyvale, California, USA. Established in 2000, it provides a wide range of network security and threat protection solutions for carriers, data centers, enterprises, and distributed offices. Its solutions are integrated into the Fortinet Security Fabric. The Fortinet security operations portfolio includes SIEM, SOAR, and XDR capabilities, as well as more advanced security analytics and automation tools. Fortinet’s sweet spot is the mid-market and large enterprises in North America and the EMEA region.
FortiSOAR is the champion product when it comes to automation and having the ability to maximize existing tools. FortiSOAR can be deployed on-premises, in private cloud, public cloud, and can be deployed as a SaaS and VM. FortiSOAR supports advanced multi-tenancy, wherein the tenant's data could either be on the Master Server (called as Shared Tenancy) or a Dedicated SOAR node (called Dedicated Tenant Node).
The platform can also be deployed standalone, with native integrations within FortiSIEM, or as a container inside FortiAnalyzer. Threat intelligence comes with the product and does not need to be purchased separately. In addition, FortiSOAR has a dedicated mobile application for both iOS and Android platforms.
The platform includes 450+ connectors, advanced case management, and low/no-code playbooks. When it comes to playbooks, FortiSOAR supports the advanced agnostic playbooks concept, wherein a playbook for tenant is auto selected based on the context. Common use cases include triage, threat investigations, response actions, mitigation actions, enrichments, and SLA computation and enforcement. The platform’s recommendation engine provides analysts with suggested actions, correlated alerts, and critical data.
FortiSOAR’s dashboard shows alerts, alerts by type, incidents, incidents by severity, critical incidents, and incidents resolved. Furthermore, the platform integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Microsoft Azure Sentinel, Exabeam, FireEye Helix, Fortinet FortiSIEM, Logpoint, LogRhythm, McAfee, IBM QRadar, Rapid7, Securonix, Splunk, and Sumo Logic. FortiSOAR also supports STIX and TAXII.
Overall, Fortinet’s FortiSOAR provides a highly modular and flexible solution. The platform enables quick deployment even for companies lacking the required operational expertise yet can offer a flexible upgrade path to support the largest and most complex architectures. FortiSOAR should be near the top of any organization’s SOAR RFP list. Fortinet appears in the product, innovation, and market leadership categories.

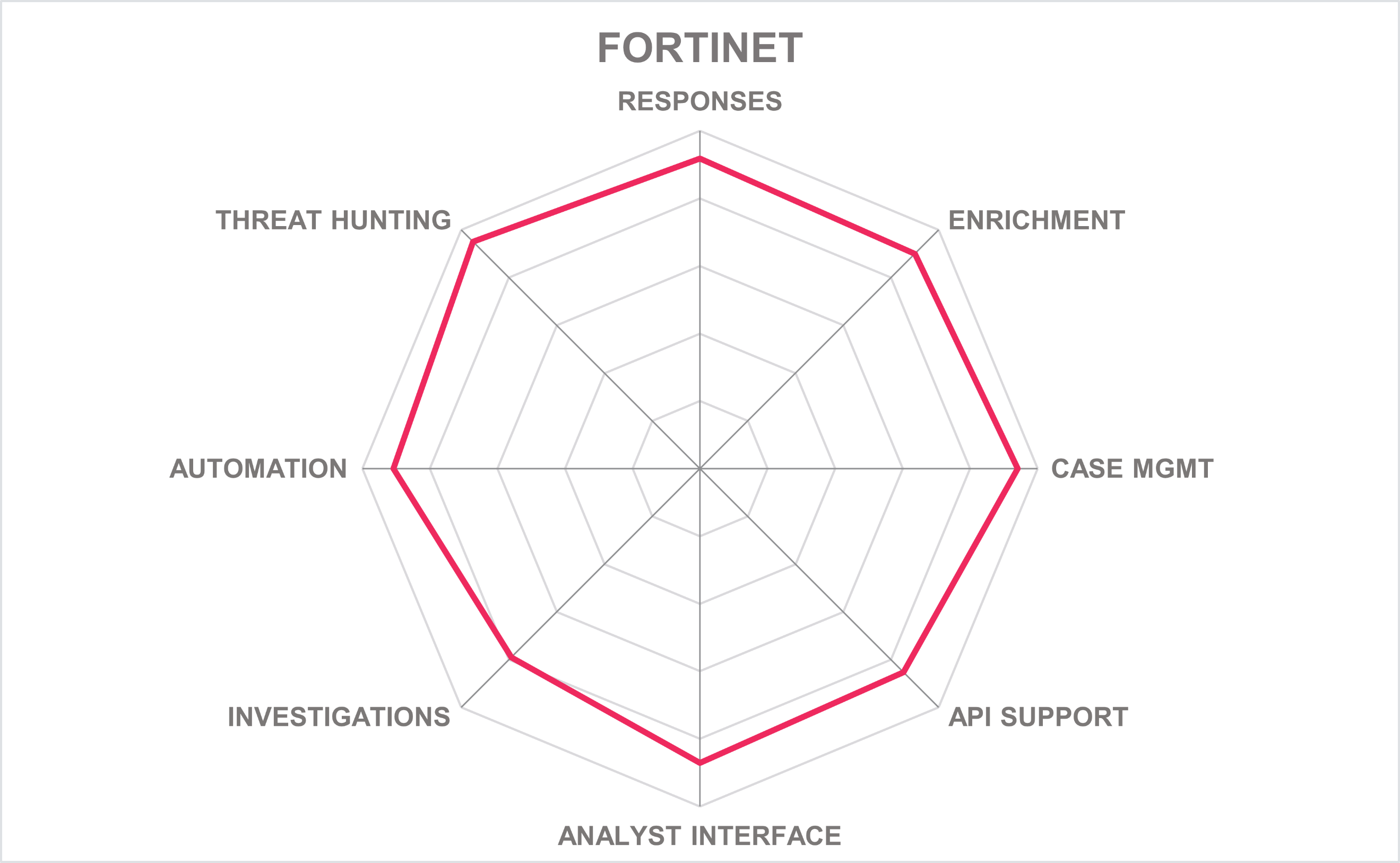
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 4: Fortinet’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
IBM Corporation is a multinational technology and consulting company headquartered in Armonk, New York, USA. Founded in 1911, IBM has evolved from a computing hardware manufacturer into offering a broad range of software solutions, infrastructure hosting, and consulting services in such high-value markets as business intelligence, data analytics, cloud computing, virtualization, cybersecurity, and identity and access management. With a strong global presence and customers and partners across the globe, IBM is a major player in the market.
IBM has a full suite of cybersecurity, identity and data management solutions which consist of multiple components. QRadar SIEM, for instance, is a leading SIEM solution. QRadar provides an XDR ecosystem that integrates EDR, NDR, SIEM/UBA, SOAR and Threat Intelligence capabilities. QRadar SOAR can be consumed as part of a fully integrated suite (through IBM Security QRadar XDR Platform) or as a set of integrated products or services. However, QRadar SOAR can also be consumed as standalone product with threat intelligence available (IBM X-Force Threat Intelligence) or third-party threat intelligence integrations.
The platform leverages powerful orchestration and automation capabilities to accelerate incident response and build automations. QRadar SOAR offers a comprehensive solution to build, edit, and deploy playbooks in the Incident Response process through the Playbook Designer. Playbook Designer is a streamlined approach to automation, providing a unified canvas that allows creation of playbooks through drag and drop of different elements and quick editing. Clients can also develop sub-playbooks for repeatable automations in their environment to be used in different playbook contexts. QRadar SOAR's playbooks are dynamic and adaptive. Playbooks evolve with the incident as analysts uncover further details about it, enabling them to add new tasks and trigger additional workflows.
In addition, SOAR offers a Breach Response module with a global knowledgebase of 180+ regulations and Privacy related Incident Responses. This knowledgebase includes breach notification regulations across the world such as GDPR, CCPA, and LGPD. It also includes industry-specific regulations with a privacy breach reporting requirement, such as HIPAA. This allows customers to align Privacy and Security Operations to meet regulatory requirements. Breach Response helps connect the Security and Privacy teams in one platform, allowing different business units teams to collaborate and monitor their process within the same platform.
Recently, IBM acquired Randori, a leading attack surface management (ASM) and offensive cyber security provider. This acquisition will help to further simplify threat detection and response, adding more visibility about the attack surface and asset discovery. Advanced cognitive technologies provided by IBM Watson AI provide dramatic improvements in analyst productivity and enable quick response to cyberthreats. Clients can also extend their SOAR capabilities and help correlate, prioritize, and effectively investigate alerts with an attack timeline and MITRE mapping. Furthermore, IBM’s SOAR can utilize admin and analyst MFA methods, including SAML for federation. IBM positions itself as a leader in the SOAR space and appears in the product, market, and innovation leadership categories.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 5: IBM’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Logpoint is a multinational software company originally founded in 2003 in Copenhagen, Denmark. At present, the company has global presence with multiple offices across Europe, North America, and Asia. The company is notable for offering SIEM, UEBA, SOAR, and Business Critical Security (BCS) technologies converged into a complete platform that aims to detect threats, minimize false positives, autonomously prioritize risks, and respond to incidents. Its client base is mainly composed of mid-market and large enterprises in government, manufacturing, and healthcare industries.
The platform can be deployed on-premises, SaaS, and as a service through MSSPs. SOAR is their latest product, it includes out-of-the-box integrations and open APIs. Logpoint SOAR is included at no extra charge in the SIEM license. The SIEM licensing is based on number of nodes. Logpoint SOAR integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Microsoft Azure Sentinel, Exabeam, FireEye Helix, Fortinet FortiSIEM, LogRhythm, IBM QRadar, Rapid7, Securonix, Splunk, and Sumo Logic.
Logpoint is primarily a standalone, tightly integrated platform doing SIEM, SOAR, UEBA and BCS. It is not meant to serve as a SOAR add-on to an existing SIEM. However, it is possible to forward logs from the above SIEMs to Logpoint SIEM and enjoy all the Logpoint SOAR capabilities. Moreover, Logpoint also supports STIX, TAXII, and YARA.
The Logpoint SIEM and SOAR Threat Intelligence application comes with a ready-to-use Threat Intel Analytics package that includes general-purpose vendor alerts, rules, and dashboards for threat intelligence. In addition, Logpoint is one of the few vendors with SAP-domain knowledge and services for MDR providers. With BCS for SAP, organizations can integrate complex SAP data into a centralized SIEM system while providing SOC analysts with monitoring and automation capabilities.
The system allows generic user supplied scripts from customers allowing any protocol to be supported. Also, its native multi-tenant capabilities and support for distributed deployments make it especially appealing to large enterprises with complex requirements, as well as to MSSPs. The company's European roots are clearly visible in the solution's strong focus on privacy and data protection according to regulations like GDPR.
In 2021, the company announced the acquisition of Tel Aviv-based SecBI, an important player in automated cyber threat detection and response. As a result of this acquisition, SecBI has enabled Logpoint to create a native SOAR that is available for all SIEM users without any additional cost. Logpoint’s agility and innovativeness make them a worthy choice for potential customers ranging from small businesses to large enterprises. Organizations looking for SOAR functionality, particularly those in Europe who are mindful about GDPR, should consider Logpoint for RFPs. Logpoint appears in the product and innovation leadership categories.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 6: Logpoint’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Headquartered in Pleasanton, California, USA with development and operations happening out of Chennai, India, ManageEngine provides over 180,000 customers around the world with over one hundred solutions for managing IT operations for endpoints, servers, networks, and the cloud, as well as security tools for desktops and mobile devices. ManageEngine is a division of privately held ZOHO, founded in 1996. ManageEngine also has products for IT Help Desk management, patch and vulnerability management, MDM, SIEM, PAM, and other areas of IT management and security.
ManageEngine Log360 is not a single product, but a suite of multiple specialized tools integrated into a single management console. Log360 is available for on-premises, in the cloud as a SaaS-based SIEM (Log360 Cloud), and some components are available on AWS Marketplace and Azure Marketplace. Licensing is per server. Log360 also supports STIX, TAXII, and YARA.
SOAR capabilities are built within Log360 and include security analytics, anomaly detection using ML algorithms, automated incident response workflows, visual workflow builder, etc. Moreover, Log360 allows users to customize the dashboard and the widgets displayed. This allows them to instantly view the network events they deem as important. Anomaly risk modelling is customizable as well. Log360 can also trigger alerts and tickets in ITSM systems.
Log360 provides automated responses through incident workflows (playbooks), which lay out the sequence of steps to be taken following a security incident. In case indicators of compromise are detected, actions can automatically be taken to suspend or disable the user. Furthermore, Log360 allows users to build automated workflows using visual flowcharts from a set of actions available in the workflow menu. The platform can also interoperate with PAM solutions such as PAM360, which is an offering from ManageEngine.
Since Log360 is a SIEM, it has limited connectors to other SIEMs. What Log360 lacks in certain functions compared to other SOAR specialists, it compensates with a broad range of additional (and extremely useful) security and compliance features, which are incorporated into a convenient unified management console with impressive out-of-the-box reporting capabilities.
ManageEngine Log360 has both SIEM and SOAR in a single package. The company is focusing more on its cloud SIEM offering called Log360 Cloud which is currently in development. Organizations that are already ManageEngine and Zoho customers may find it easy to add SIEM and some SOAR functionality to their security portfolios.

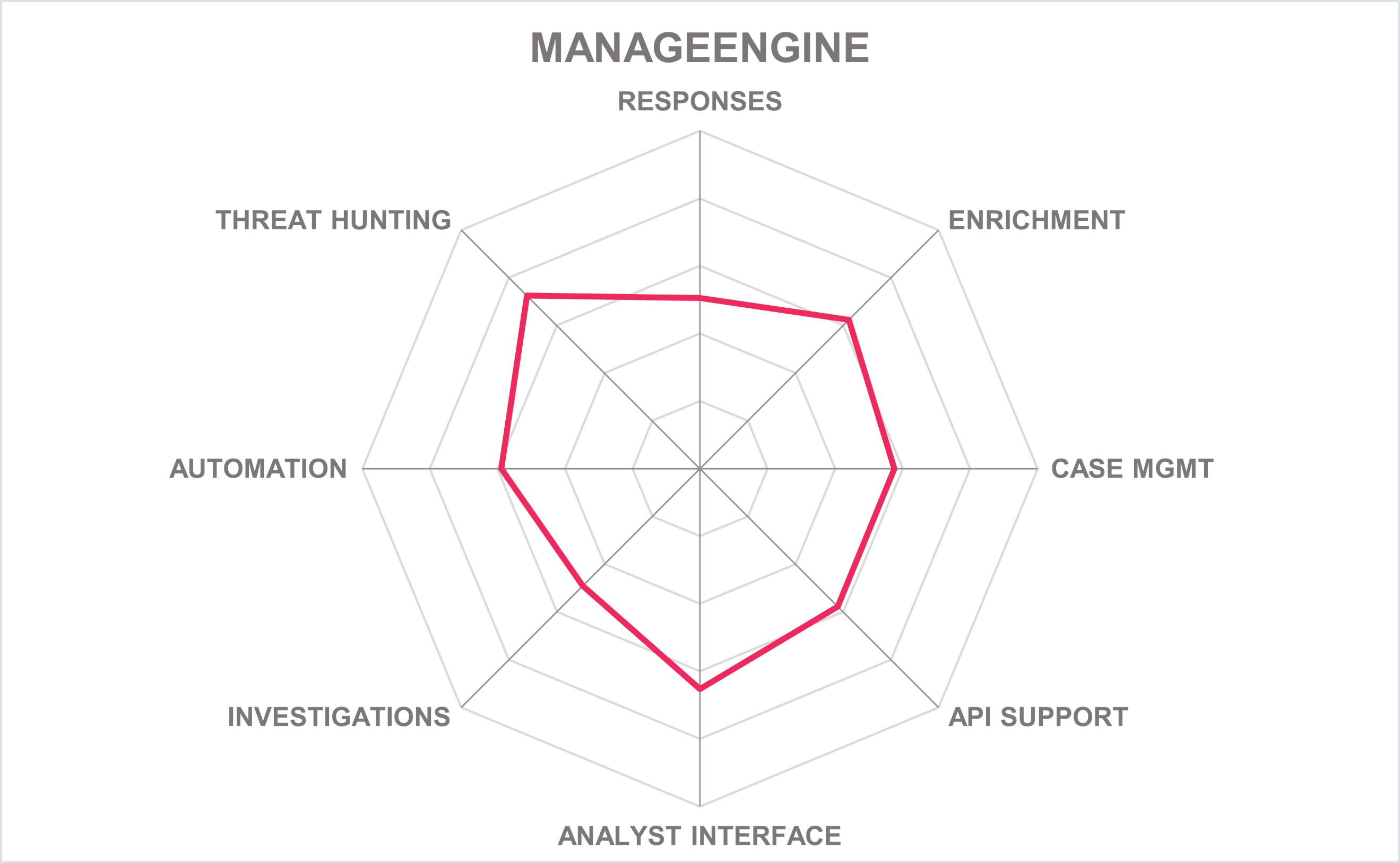
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 7: ManageEngine’s rating
| Strengths |
|
| Challenges |
|
Microsoft, founded in 1975 and based in Redmond, USA, is a familiar figure in hardware and software, digital services, and cloud infrastructure businesses. The company is the world's largest software company and one of the top corporations by market capitalization. Microsoft Sentinel, previously known as Azure Sentinel, is a cloud-native SIEM and SOAR platform that delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
Microsoft Sentinel customers are not charged extra for SOAR capabilities. The platform is a SaaS offering and utilizes the cloud economics model based on consumption of the service. Licensing is subscription based and pricing is based on volume of data ingested. The product started as a modern SIEM that helped customers scale out the number of alerts and amount of data into one single platform. Essentially, Sentinel is the place where all the data from all the devices and entities in the organization is ingested.
SOAR capabilities are integrated natively with the SIEM, so incidents, automations and investigations happen where the data is. Sentinel automated workflows (playbooks) are based on Azure Logic Apps platform, which runs billions of actions for thousands of organizations. With 250+ available OOTB connectors, Sentinel playbooks can integrate with Azure services, as well as with 3rd-party ticketing systems, collaboration platforms, and custom APIs. Microsoft also supports STIX and TAXII.
Furthermore, customers and partners can add more solutions, ingest data from any other SIEM platforms, as well as interact with and orchestrate any other 3rd-party security tool. Microsoft offers substantial freedom of customization for the platform, by allowing customers to integrate other Azure services, enabling advanced analytics and threat hunting, own machine learning models, custom automation, external threat intelligence, etc.
Each organization has different requirements and needs when it comes to adopting a SOAR solution. However, Microsoft Sentinel has the scalability and performance to provide organizations with alert detection, threat visibility, proactive hunting, and threat response capabilities. The solution should be on the shortlist for any organization looking for robust enterprise SOAR services. Microsoft appears in the product and market leadership categories.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 8: Microsoft’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Palo Alto Networks, founded in 2005 in Santa Clara, CA, was the pioneer in Next Generation Firewall (NGFW) technology, and is also a major player in the SOAR market after the acquisition of Demisto. Palo Alto also offers endpoint security, XDR, threat intelligence feeds, and other security products. XSOAR includes an engine that enables connecting cloud to on-prem, on-prem to cloud, and cloud to cloud. Customers can deploy multiple engines. Palo Alto hosts a managed service, and some MSSPs use their software for SOAR functions as well. XSOAR is licensed per admin/analyst user.
XSOAR provides full multi-tenancy with complete data segregation between customers in a single deployment, as well as the option to scale the architecture horizontally by deploying multiple hosts, each carrying multiple tenants. Palo Alto’s multi-tenancy allows the master (MSSP) to view incidents across all tenants, deploy automation (playbooks, scripts, dashboards and more) to all tenants, or selectively to some tenants.
The SOAR component integrates with many threat detection tools including EDRs, NTAs, NDRs, firewalls, and SIEMs such as Micro Focus ArcSight, Microsoft Azure Sentinel, Coralogix, Exabeam, FireEye Helix, Fortinet FortiSIEM, Logpoint, LogRhythm, McAfee, IBM QRadar, Rapid7, Securonix, Splunk, and Sumo Logic. Palo Alto supports CyBox, STIX, YARA, CSV, JSON, and TAXII feeds from other providers.
Reports can be customized to suit the needs of the stakeholders. The report widget allows customers to build any type of report needed from the underlying data. They can add widgets, schedule report generation and distribution, add recipients, select incident time ranges, etc. XSOAR has an integrated threat intelligence management module, case management, IAM, NetOps, cloud security, IoT security and vulnerability management automation content packs, beyond SecOps use cases. The solution has its own mobile app which allows users to leverage SOAR capabilities anywhere. The app runs on both Android and iOS.
Playbooks in XSOAR automate most responses. The solution uses several mechanisms (such as a pre-processing policy) that eliminate false positives, and de-duplicate and cluster events. In addition, users have the option to clone and edit 800+ out-of-the-box playbooks using a drag and drop visual editor. The company also provides 1,000+ scripts of common automation tasks that can serve as building blocks for playbooks. The platform supports sub-playbooks that can be nested and reused across multiple playbooks, allowing for complex workflows. The user can easily view the code and choose to code playbooks if preferred.
The substantial number of connectors available, plus the ability to extend the platform, make Palo Alto’s XSOAR one of the dominant products on the market today. Palo Alto’s agility and scalability make them a worthy choice for mid-market organizations and large enterprises. Palo Alto appears on the product, market, and innovation leadership categories.

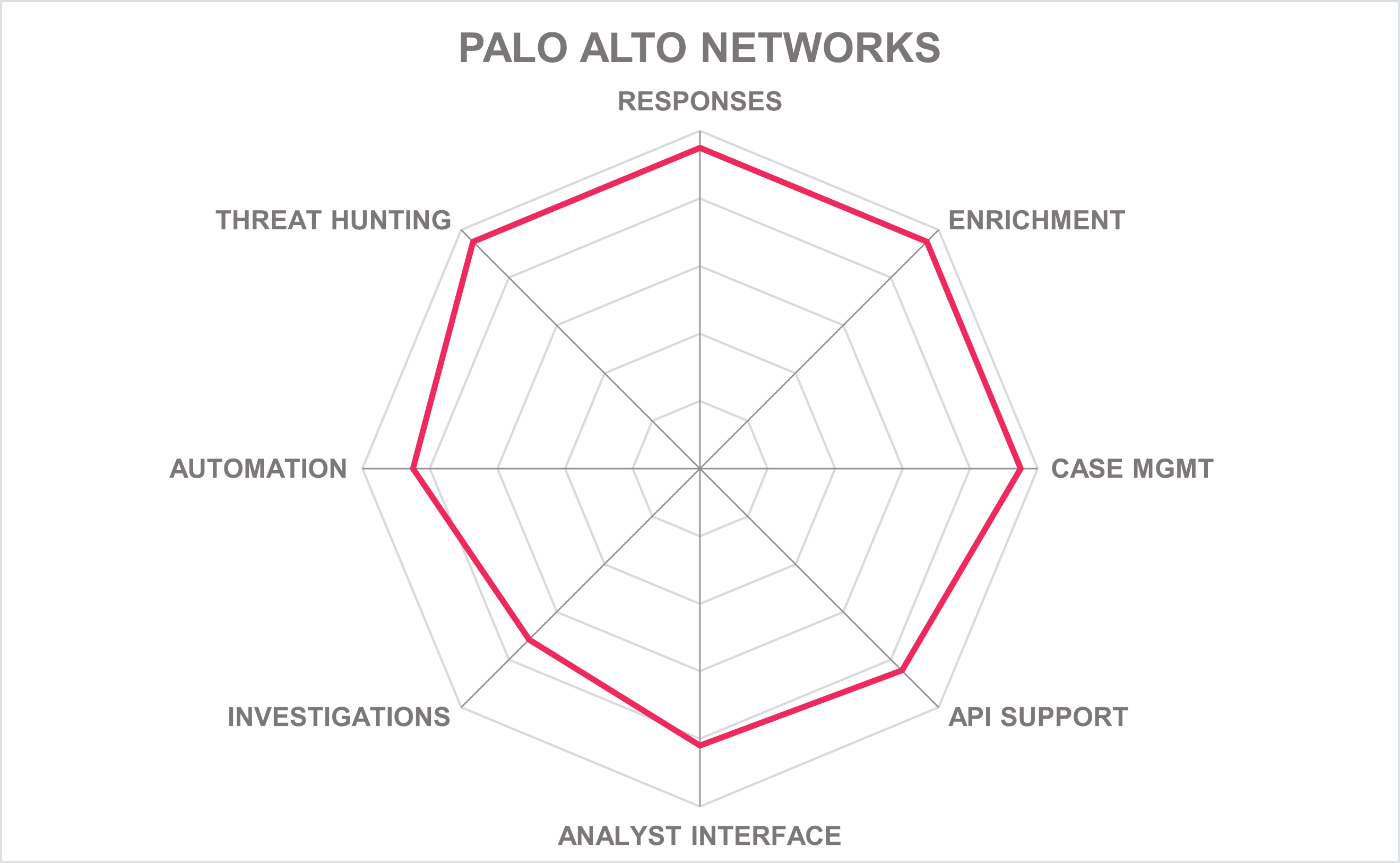
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 9: Palo Alto Networks’ rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Founded in 2000 and headquartered in Boston, Rapid7 originated as a vulnerability management solution provider. Currently, the company offers a broad range of cybersecurity products and services, with most of its portfolio built upon the unified, cloud-native Insight platform. These include but are not limited to vulnerability management, application and cloud security, SIEM/XDR, threat detection and response, threat intelligence, security orchestration and automation and related managed services. The company is focused on North America, but with a growing number of customers in the EMEA and APAC regions.
Rapid7 Insight Platform delivers a security operations platform with a portfolio of products. It includes cloud security (InsightCloudSec), application security (Insight AppSec), vulnerability management (InsightVM), orchestration and automation (InsightConnect), threat intelligence (Threat Command), and XDR and SIEM (InsightIDR). InsightConnect licensing is based on a per time period subscription (generally 1-3 years) and is primarily based on a percentage of other Rapid7 products in use, is included in multiple product combination packages (which themselves are node based), and also has a per-user pricing that is used in situations when no other Rapid7 product is in use. The Insight Platform can be consumed as a cloud service as well as via select MSSPs, and as the detection, investigation, and response layer in Rapid7’s own Managed Detection & Response service.
SOAR capabilities are delivered through two methods: via embedded and integrated capabilities with their other Insight Platform solutions - such as InsightIDR and InsightVM can also be delivered as a standalone SOAR solution. In both scenarios it can be used to implement and automate use cases that both extend the Rapid7 platform and to interoperate with 3rd-party IT and security products. Some common use cases when implementing the Rapid7 SOAR include detection and response (collecting data within the environment, enriching and prioritizing alerts into more actionable alerts, and implementing automation features and decision steps on top of those actionable alerts), automation and orchestration for SIEM and XDR tools (in particular Rapid7 InsightIDR), alert enrichment and validation (automatically gather context for analysts to make a rapid decision), network, user, and endpoint containment (reduce or quarantine the spread of a potential malicious event within the environment), and vulnerability management related automations (identifying, evaluating, mitigating, and reporting on security vulnerabilities) as well as ITSM ticketing as appropriate for all the above. In addition, STIX support is provided at the InsightDR level.
InsightConnect offers over 200 off-the-shelf automation workflows that can be imported and used with no custom development required. For users interested in building or customizing their own automation workflows, InsightConnect's no-code workflow builder allows users to build, test, and run custom automation workflows with a graphical user interface. Playbooks are edited with a visual workflow builder. Prebuilt templates can also be easily imported and edited to suit a customer's unique process. Moreover, the platform uses regular code reviews and 3rd-party vulnerability scanning tools to identify issues. Patches are applied using automated and manual patch management tools and processes.
With the Rapid7's Insight Platform, customers are able to combine multiple security solutions according to their needs and requirements. InsightConnect is an excellent choice for customers who need cloud-native automation with no on-premises components. For smaller customers experiencing skill shortages, Rapid7 offers several managed security services as well.

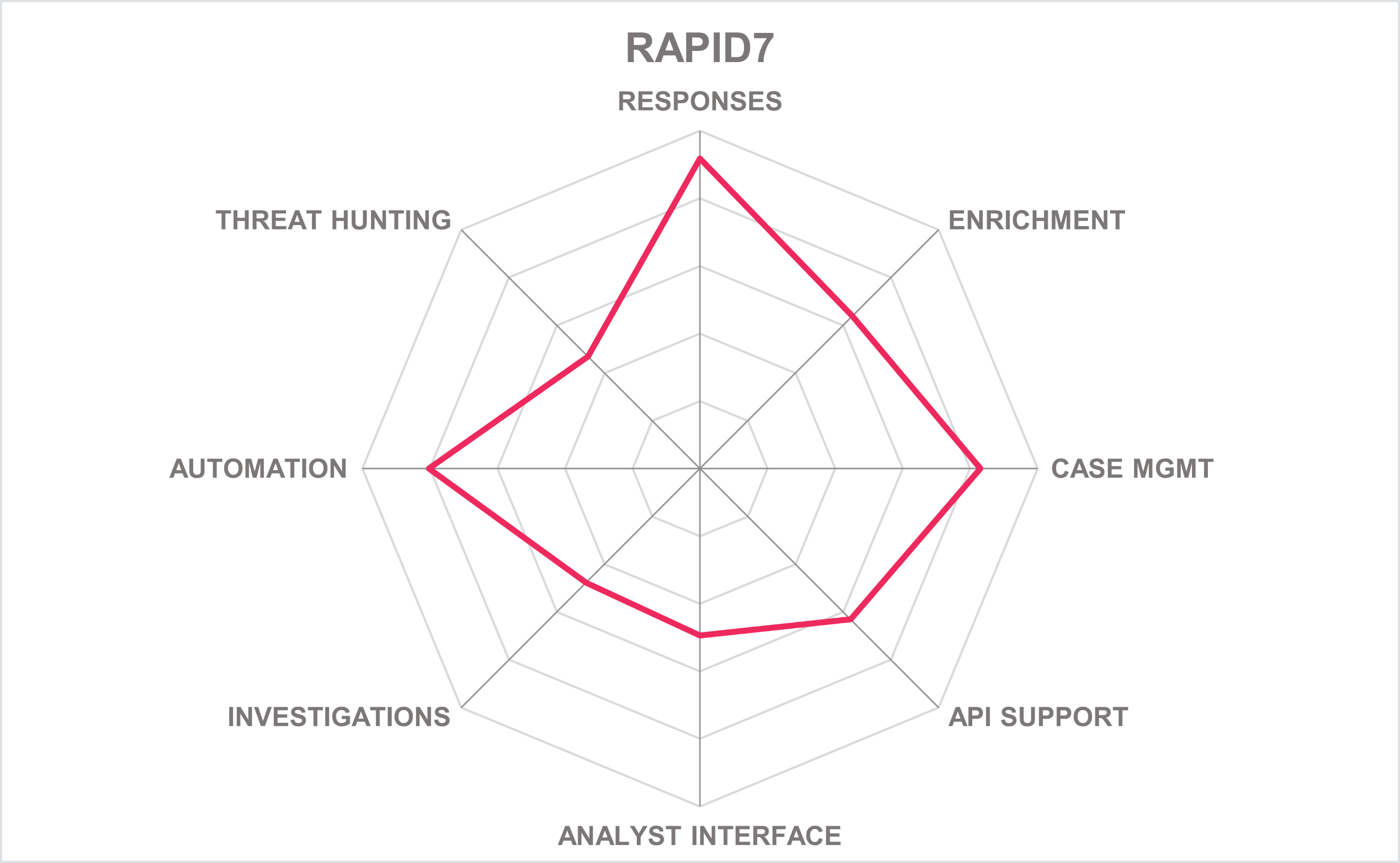
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 10: Rapid7’s rating
| Strengths |
|
| Challenges |
|
Securaa was founded in 2018 and its headquarters are in Bangaluru, India. Securaa is a SOAR platform that enhances SOC’s capabilities with automation, threat enrichment, and real-time visibility and control. Despite being a young and small vendor, Securaa is fully multi-tenant and built on a container-based microservices architecture. The platform is completely modular, and components can be deployed across hybrid environments. Their customer base is primarily located in the APAC region, but with growing presence in the Middle East and North America. The solution is deployable on-prem, in IaaS, and SaaS.
The platform includes Securaa’s Threat Intelligence Platform (TIP) which correlates indicators of compromise and Securaa’s Asset and Vulnerability Intelligence Platform (AVIP) which provides a proactive approach to cyber asset and controls management. The two platforms are fully integrated as well as available as a modular product. Subscriptions are per-user and fixed cost options are also available.
Securaa is a no-code platform. The platform provides a visual workflow editor for analysts to build or modify playbooks. Playbooks are out of the box for most common use-cases like C2C, phishing, malware analysis, etc. It also includes manual, semi-automated, and fully automated execution of playbooks for orchestration and response automation (500+ automated tasks and 100+ ready-to-use playbooks).
Securaa is a very configurable platform, from dashboards to widgets, to reports, and to case management. The platform is packed with a lot of configurable capabilities through which customization can be done in an agile manner. Custom layouts can be built for each incident category and menu options can be restricted based on role-based access control. For case management, the platform captures case data, enrichment from Securaa SecBot, link analysis, etc. It also allows collaboration between analysts and can be used for audits.
Furthermore, the platform integrates with SIEMs and security analytics tools such as Elastic, Micro Focus ArcSight, Microsoft Azure Sentinel, LogRhythm, McAfee, IBM QRadar, Rapid7, RSA Netwitness, Securonix, Splunk, and Sumo Logic. Securaa also supports STIX and TAXII.
Securaa is one of the few SOAR platforms that has a AVIP (Asset and Vulnerability Intelligence Platform) along with a Threat Intelligence Platform which empowers security teams to get all the internal context around assets, vulnerabilities, exploits and business impact. Securaa positions itself as an alternative to the established offerings, which should be of interest to organizations in the APAC region. However, being a rather small vendor, Securaa has a still relatively small global partner ecosystem. On the other hand, the company provides a modern solution that fits well to the requirements of a SOAR solution.

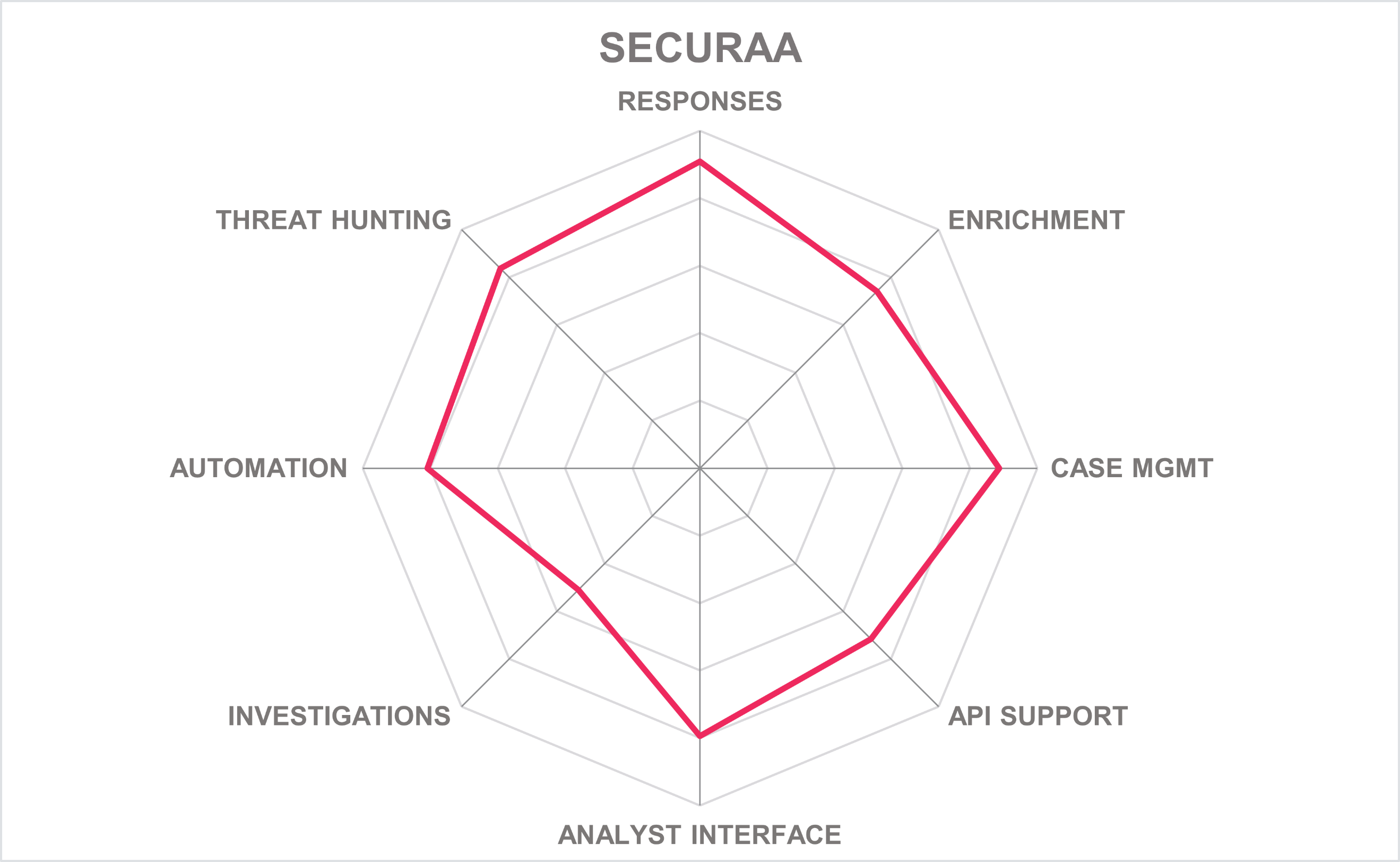
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 11: Securaa’s rating
| Strengths |
|
| Challenges |
|
Processes and workflows are not automatically updated whenever regulations change, but improvements are on the roadmap
ServiceNow, founded in 2004 and headquartered in Santa Clara, is a large IT management, operations, and business management software vendor. They also have products in the IT security, asset management, GRC, and DevOps areas, providing solutions for both employee and customer facing enterprises. Their SOAR offering can be deployed on-premises, private cloud, public cloud, and as a service through MSSPs. ServiceNow has a strong presence in North America, but with growing customers in the EMEA and APAC regions. The solution is licensed per user.
ServiceNow integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Microsoft Azure Sentinel, LogRhythm, McAfee, IBM QRadar, Rapid7, Securonix, Splunk, Sumo Logic and many more. The integrations above are for out of box configurations, however, using ServiceNow Platform's REST API, any external system can submit security incident records for investigation. Additionally, with the IntegrationHub feature bidirectional integrations with any SIEM can be built.
The IntegrationHub is a companion feature, which makes it easier to create integrations. Among other things, this capability enables customers to build orchestration capabilities with numerous third-party systems in a no-code/low-code fashion and integrate any sandbox with a modern API. Integrations with IaaS/PaaS solutions are also available on the ServiceNow store.
Their Flow Designer is a visual interface for creating and managing workflows. It is a visual workflow designer with a drag and drop interface which also supports the creation of re-usable sub-flows. It enables mature playbook designs and customized actions that can be added into forms for specific actions. Workflow automation is a focus and core strength for ServiceNow across all product lines.
The Security Incident Response Platform is aligned with MITRE ATT&CK. The company has an innovative SOAR system management application for mobile devices which includes iOS, Android, and BlackBerry devices. Moreover, ServiceNow supports SAML federation and JWT, Key Exchange, and OAuth2 authentication. The company also supports CyBox, STIX, and TAXII.
ServiceNow is quite scalable and has excellent case management features. It has built out integrations with many diverse sets of threat intelligence for enrichment. Furthermore, the platform integrates with Data Loss Prevention (DLP) products to facilitate automation and remediation workflows. Organizations who use ServiceNow for ITSM or other functions may find it easy to gain SOAR functionality by adding Security Incident Response. ServiceNow is continuously adding more integrations and innovative features to its platform. The company appears in the product, market, and innovation leadership categories.

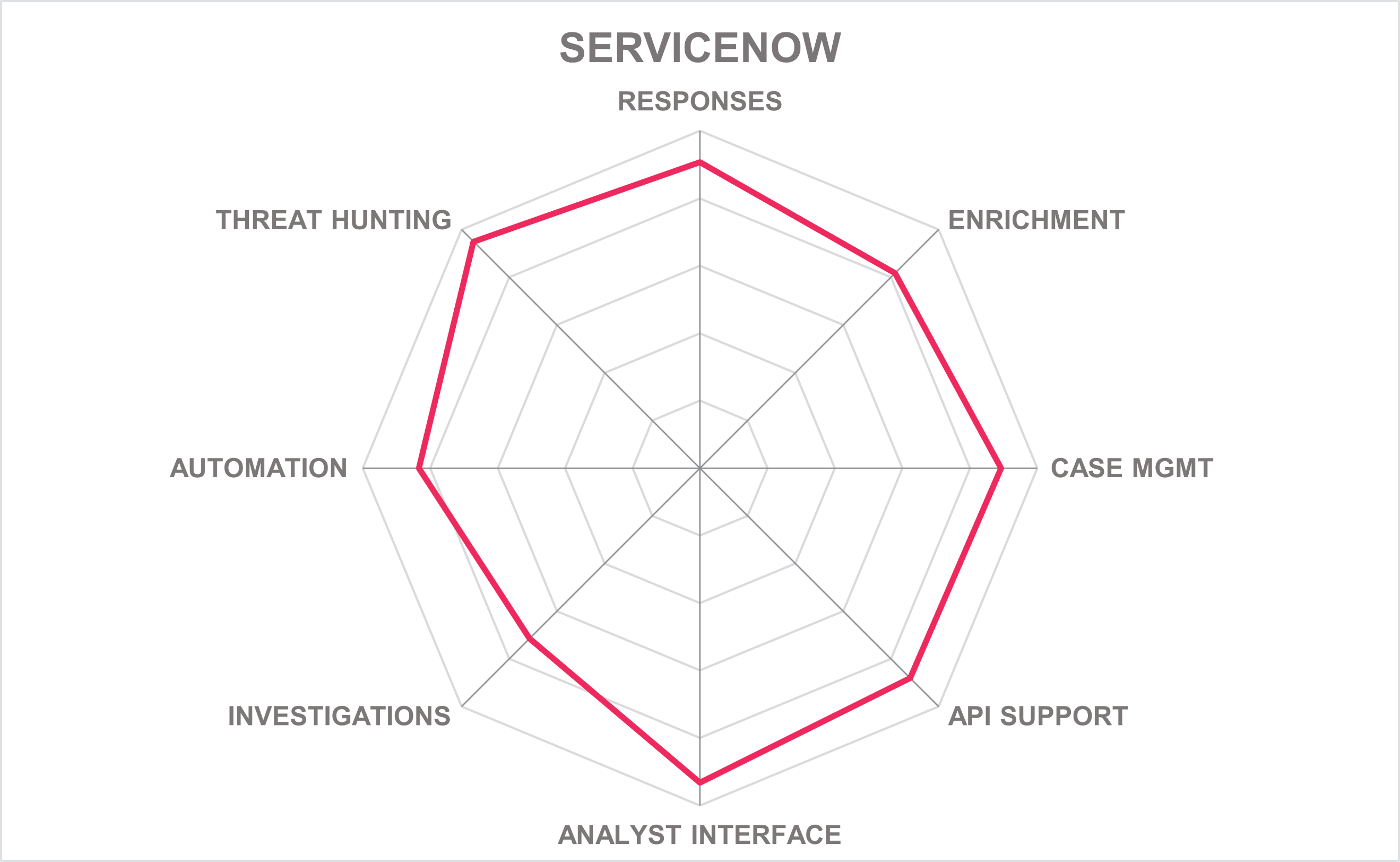
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 12: ServiceNow’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Splunk was founded in 2003 and is headquartered in San Francisco, California. Since then, the company has been producing solutions for searching, monitoring, and analyzing many kinds of machine-generated data. With its worldwide market presence and a strong global partner ecosystem, Splunk is often considered a de facto standard for operational analytics and intelligence solutions. Splunkbase includes over 2,800 apps, 70+ intel integrations, 375+ SOAR integrations that support multiple security operations actions, and high-value security integrations with over 2,500 partners. Two major licensing paradigms are available: per-user or per-Virtual Compute.
Splunk SOAR is offered as a standalone product with the ability to integrate with other Splunk products. Splunk SOAR integrates with Splunk Enterprise Security to provide a seamless and intuitive SecOps platform to prevent, detect and respond to advanced and emerging threats. The solution supports hybrid and multi-cloud environments. It can also support cloud, on-premises, and hybrid deployments. Splunk SOAR integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Exabeam, FireEye Helix, Fortinet FortiSIEM, LogRhythm, IBM QRadar, Rapid7, Splunk, and Sumo Logic. Splunk supports CyBox, STIX, and TAXII.
The Splunk Enterprise Platform includes streaming, machine learning, search and visualization, collaboration and orchestration, and scalable index. Splunk SOAR comes with one hundred pre-made playbooks out of the box. Splunk SOAR integrates across 350+ third-party tools and supports over 3,000+ different automatable actions. Moreover, playbooks can be edited via visual flow-chart within their Visual Playbook Editor, where users apply coding and copy from templates.
SOAR’s visual playbook editor makes it easy to create, edit, implement, and scale automated playbooks to help your team eliminate security analyst grunt work, and respond to security incidents at machine speed. In addition, Splunk SOAR’s orchestration, automation, response, collaboration, and case management capabilities are also available from mobile devices. For Case Management, the solution includes the use of playbooks to automate response tasks to force multiply team efforts, execute automated response tasks in a short time, and support decision making, evidence capture and improve overall response performance.
Splunk SOAR apps provide a mechanism to extend Splunk SOAR by adding connectivity to third party security technologies in order to run actions. Not only does Splunk have more connectors to third- party apps than competitors, but they also test all the apps. In addition to testing all the apps, the company has open-sourced the connectors on GitHub which drives more quality and community contributions as a result.
The ability to scale the platform makes Splunk’s SOAR an excellent choice for mid-market and large enterprises. Organizations looking to get started on a SOAR journey should consider Splunk's products and services. Splunk appears on the product and market leadership categories.

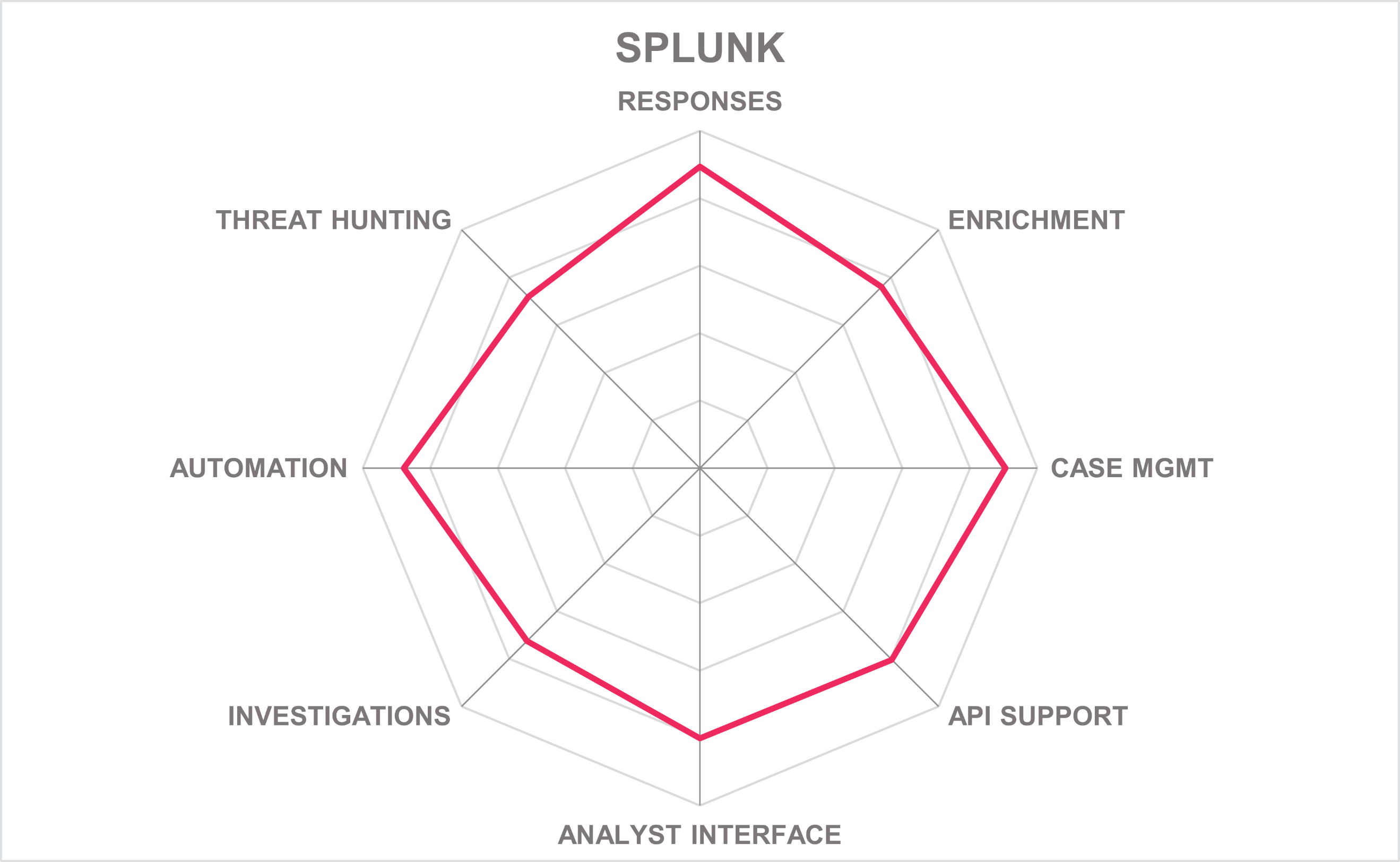
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 13: Splunk’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Sumo Logic is a cloud-native data analytics company based in Redwood City, California, USA. Founded in 2010, the company focuses on developing and operating an elastic cloud platform for collecting and analyzing enterprise log data. Sumo Logic offers a range of operational, security, and business intelligence solutions that are entirely cloud-based and low maintenance. The company has a strong presence in North America and the EMEA region.
Cloud SOAR is part of the overall Sumo Logic platform. Sumo Logic’s Cloud SOAR takes a proactive approach toward alert investigation, collecting security data and alert information from various sources, including SIEM. It leverages machine learning to significantly reduce false positives and duplicate events. Licensing is per user. However, licensing for MSSP customers varies from the standard user model to license per tenant instance. The company's Cloud SIEM solution is, as the name implies, an entirely cloud-based SaaS offering with on-premises components and offered as a service by MSSPs.
In 2019, the company acquired JASK Labs Inc. The acquisition brings together Sumo Logic’s Continuous Intelligence Platform, including its pioneering cloud SIEM and security compliance solutions, with JASK’s ASOC offering to deliver a leading cloud-native security intelligence solution built for today’s digital businesses that leverage modern applications, architectures, and multi-cloud infrastructures. In 2021, Sumo Logic acquired DFLabs, a SOAR specialist vendor headquartered in Italy.
One of the main differentiators is the fact that the company is investing in the Open Integration Framework (OIF). The OIF is an integration framework created to make it easier for organizations to connect disparate security tools for a more seamless security remediation workflow. OIF changes the way integrations are being utilized within a platform, allowing users to easily integrate with third-party technologies, develop external connectors and trigger various automated actions. It provides integration flexibility by allowing developers to extend integrations, modify action parameters, personalize action results, create custom table views, etc.
Furthermore, the OIF feature allows daemons to be customized and adjusted according to the needs of the user. Daemons are also used to leverage the automation capabilities. The most common daemons are the ones that are instructed to take care of verifying the content of a mailbox, retrieving new threat feeds from external repositories, and analyzing databases external to Cloud SOAR. Different rules apply to different time frames in which daemons are launched and these can be adjusted to align with customer’s needs.
Cloud SOAR performs automatic analysis, creates incidents, and allows security event data export. Security analysts can see all the information generated by the playbooks and other analysts’ actions. There is also the possibility to nest an existing playbook inside another playbook and to connect multiple playbooks into a master playbook.
Sumo Logic’s Cloud SOAR offers an entirely cloud-based and low maintenance solution with flexible pricing. It should be of interest to organizations within the EMEA region and North America.

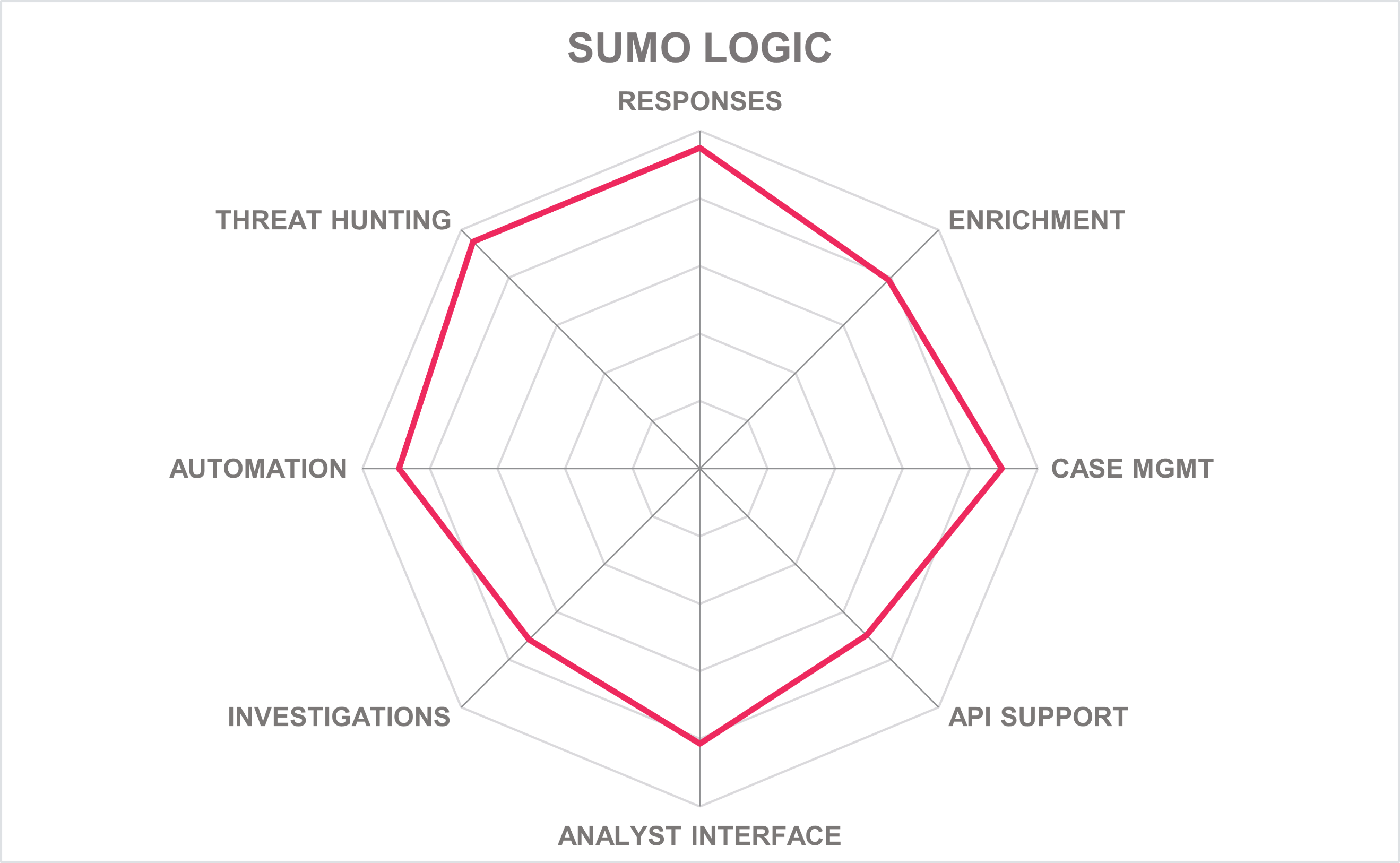
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 14: Sumo Logic’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Swimlane is a low-code SOAR specialist that was launched in 2014 and headquartered in Boulder, Colorado. The company has regional offices in London, Sydney, Dubai, and Kuala Lumpur. Coverage has been primarily focused on North America, but is now growing across Europe, APAC, the Middle East, Turkey, and Africa (META). Swimlane Turbine is reportedly favored by government agencies, large enterprises, and service providers for its fully multitenant architecture and the ability to accommodate extremely high event throughputs. Swimlane is licensed on a per-user basis.
The Swimlane platform has been delivering low-code security automation and SOAR solutions to the market since 2017. Swimlane Turbine is a more recent breakthrough in low-code security automation that captures hard-to-reach telemetry and expands actionability to the typically closed extended detection and response (XDR) ecosystem.
The Swimlane platform is built to integrate with any API, so virtually any integration that a customer requires is an option. The company offers customers on-demand integrations at no additional costs, so the business applications they support are constantly changing. The platform integrates with SIEMs and security analytics tools such as Micro Focus ArcSight, Microsoft Azure Sentinel, Exabeam, FireEye Helix, Fortinet FortiSIEM, Logpoint, LogRhythm, McAfee, IBM QRadar, Rapid7, Securonix, Splunk, and Sumo Logic. The platform also integrates with popular endpoint security tools from SentinelOne, CrowdStrike, VMware and more. Swimlane also supports CyBox, STIX, TAXII, and YARA. More recent integrations include those for securing OT/IoT environments with the likes of Nozomi Networks and Dataminr.
Turbine’s Autonomous Integrations extend visibility and response to closed XDR ecosystems. This technology enables security teams to connect siloed technologies like cloud, IoT, and edge computing. Moreover, Turbine’s Adaptable Playbooks make it easy to build modular, repeatable automations that are flexible enough to align to any security priorities or established business processes.
In addition, the platform provides robust CISO-level dashboards and real-time reporting, compliance and audit reporting, and powerful case management for incident response and investigation workflows. Swimlane’s reporting and dashboards are also adaptable. It conforms to how different organizations work, the processes they track, how they report, their compliance or regulatory requirements, internal intricacies, and risk management practices. This provides customers with autonomy and control over their system which may be more difficult with less adaptable solutions.
Swimlane and its innovative capabilities provide a suitable alternative for customers in complex and highly regulated industries. Organizations looking for configurable low-code playbooks and autonomous integrations should consider Swimlane Turbine. While Swimlane already has a sizeable number of customers, obtaining more security certifications will appeal to customers in certain regulated industries and others that have strict security requirements. The company appears in the product leadership category.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 15: Swimlane’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Founded in 2013, ThreatQuotient is a threat intelligence and SOAR specialist headquartered in Ashburn, Virginia. In the early days, ThreatQuotient focused on threat intelligence management and called its platform a security operations platform. In addition to the base platform, use case specific modules are available. These include ThreatQ TDR Orchestrator, ThreatQ Investigations, and ThreatQ Data Exchange. Licensing is based on data size, number of users and modules enabled. Coverage includes North and South America, Europe, Middle East / North Africa (MENA), and APAC regions.
The platform includes a Threat Library where all the data resides. It enables dynamic scoring and smart collections, provides context for automatic scoring and prioritization, and automatically aggregates and normalizes data. In addition, the platform offers a DataLinq Engine. This feature allows the platform to ingest a wide variety of information from multiple sources (external and internal) to identify bits of data that could be relevant inside those existing sources and in between those existing data sources. The engine normalizes data which allows it to do correlation and prioritize information. Once information is prioritized, the engine can deliver a result of more actions that can be taken automatically with higher confidence.
The platform consumes information using the DataLinq engine and stores it in the Threat Library. The data is presented alongside a series of relations including courses of action, tasks, and related Threat Intelligence. The platform also includes the ThreatQ Data Exchange which enables and manages intel collaboration across organizations or multiple organizations of any size and complexity. ThreatQ Data Exchange makes it simple to set up bidirectional sharing of any intelligence data within the ThreatQ platform and scale sharing across many teams and organizations of all sizes.
Built on the foundation of ThreatQuotient’s support for open intelligence sharing standards, the solution is designed for customization and collaboration. This means individual teams can operate according to their specific needs and collaborate with partners without limiting the breadth of data they want to share or leaking data they want to keep private.
Furthermore, ThreatQuotient has prioritized the development of ThreatQ TDR Orchestrator to help organizations enable more efficient and effective operations. Through a data-driven approach, ThreatQ TDR Orchestrator looks to simplify the complexity of process-driven playbooks and accelerate threat detection and response across disparate systems and sources. Innovations including Automation Packs, Atomic Automation, and a ‘no code’ interface further simplify the platform. ThreatQ has many integrations with security tools including EDR, NDR, Cloud, SIEM, IAM that allow both manual and automated workflows.
ThreatQuotient supports many standard data formats including CyBox, STIX, TAXII, and YARA. The ThreatQ platform supports a good variety of integrations and offers good scalability. The company should be on the shortlist for organizations looking for a flexible and data-driven approach. ThreatQ appears in the product leadership category.

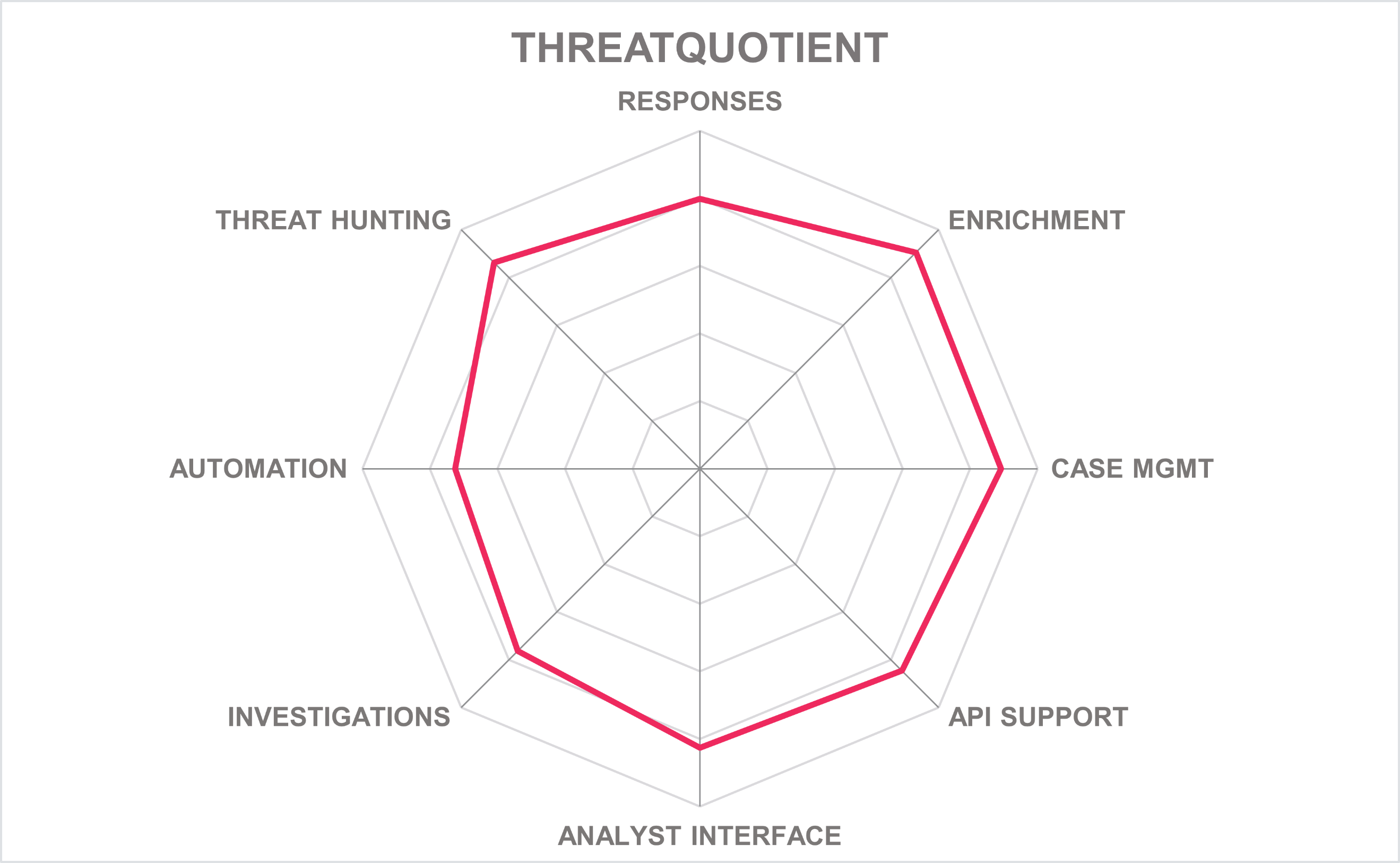
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 16: ThreatQuotient’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
Besides the vendors covered in detail in this document, we observe some other vendors in the market that readers should be aware of. These vendors may not fully fit the market definition but offer a significant contribution to the market space. This may be for their supportive capabilities to the solutions reviewed in this document, for their unique methods of addressing the challenges of this segment or may be a fast-growing start-up that may be a strong competitor in the future.
Analyst1 – Analyst1 was founded in 2012 and it’s headquartered in Washington DC. The company offers a platform that includes threat intelligence, threat detection and response, and SOAR features.
Why worth watching: The solution automates the creation of threat actor and malware profiles while providing contextual and actionable insights from multiple data sources. It also identifies an organization’s assets and systems with vulnerabilities known to be exploited by adversaries.
CrowdStrike – CrowdStrike was founded in the Bay Area in 2011 as a cloud-native endpoint protection platform. CrowdStrike has expanded their product offerings beyond EDR and has acquired several security specialist firms in recent years.
Why worth watching: The Falcon Fusion SOAR platform leverages CrowdStrike’s Security Cloud which facilitates visibility into endpoints, identities, and applications across IaaS, PaaS, and SaaS environments. The platform also uses conditional branching and sequence logic features to increase flexibility and build workflows with any set of conditions.
Elastic – The company was founded in 2012 and it is headquartered in Mountain View, California. Elastic makes data usable in real time and at scale for enterprise search, observability, and security. Elastic Security combines SIEM, SOAR, endpoint security, and threat hunting functions with the existing collection, search, and visualization capabilities of the core platform, all under a single license.
Why worth watching: The solution extends orchestration and automation capabilities by linking Elastic Security with your system of choice. The solution is open and transparent, offering numerous partners and integrations.
Exabeam – Exabeam was founded in 2013 in Silicon Valley. Exabeam offers a fully integrated security analytics management platform, which encompasses UBA, next-gen SIEM, threat intelligence, as well as SOAR.
Why worth watching: Exabeam Incident Responder and Exabeam Threat Hunter are two essential components that provide a full SOAR functionality. In addition, Exabeam has a wide range of connectors for various data sources and security tools, enabling deep integration and automated responses.
LogRhythm – LogRhythm is an information security company based in Boulder, Colorado and founded in 2003. Currently, the company offers a broad portfolio of security solutions beyond log management, including SIEM, UEBA, SOAR, as well as NDR and XDR products.
Why worth watching: LogRhythm provides a unified security intelligence platform combining next-generation SIEM, log management, network and endpoint monitoring and forensics with full threat lifecycle management and response orchestration.
Logsign – The company was founded in 2010 and has offices in the Netherlands, Turkey, and USA. The primary products are Logsign Next-Gen SIEM and Logsign SOAR.
Why worth watching: For Logsign SOAR, playbooks are enacted by "bots", including separate bots for investigations, analysis tasks, response, and remediation actions. This allows Logsign playbooks to process multiple activity streams in parallel rather than only sequentially.
MicroFocus – Founded in 1976, Micro Focus is a British multinational software company headquartered in Newbury, UK. The company is one of the world's largest enterprise software providers and offers mission-critical technology and consulting services to thousands of customers. MicroFocus acquired ATAR, a SOAR specialist, in 2020.
Why worth watching: The ArcSight ESM product is a next-generation SIEM solution which includes real-time detection, scalable event monitoring, threat intelligence feeds, and ArcSight’s native SOAR. With ArcSight ESM, threat data is aggregated, normalized, and enriched for greater threat visibility. MicroFocus SOAR will be covered in future reports.
Securonix – Securonix was formed in 2008 and is headquartered in Addison, Texas. The Securonix Security Operations and Analytics Platform provides security analytics technology for collecting, analyzing, and visualizing a wide range of business and security information and converting it into actionable intelligence.
Why worth watching: Their security analytics platform includes Data Lake, NDR (NTA), SIEM, UBA, and XDR. Securonix SOAR integrates with these components.
SIRP – SIRP is a start-up founded in 2017 and based in London. SIRP is a risk-based SOAR platform that combines security orchestration, playbook automation and case management capabilities to optimize processes for threat response and vulnerability management. The platform applies risk scoring and context to accelerate investigation and incident response.
Why worth watching: Their presence in the Middle East, both in terms of customers and sales target, is a plus for that region and for their own growth potential. Organizations that prefer a cost-effective and user-friendly SOAR solution for their mid-market and enterprise security needs should consider SIRP.
Leadership Compass SOAR 2020 Buyer's Compass SOAR Leadership Brief Find Your Route from SIEM to SIP to SOAR
Leadership Compass Security Operations Center as a Service
Leadership Compass Intelligent SIEM Platforms
Buyer’s Compass Security Operations Center as a Service
Executive View Palo Alto XSOAR
Executive View ManageEngine Log360
Advisory Note Architecting Your Security Operations Center
KuppingerCole Leadership Compass is a tool which provides an overview of a particular IT market segment and identifies the leaders within that market segment. It is the compass which assists you in identifying the vendors and products/services in that market which you should consider for product decisions. It should be noted that it is inadequate to pick vendors based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e. a complete assessment.
We look at four types of leaders:
For every area, we distinguish between three levels of products:
Our rating is based on a broad range of input and long experience in that market segment. Input consists of experience from KuppingerCole advisory projects, feedback from customers using the products, product documentation, and a questionnaire sent out before creating the KuppingerCole Leadership Compass, and other sources.
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
Security is primarily a measure of the degree of security within the product/service. This is a key requirement. We look for evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer, including authentication measures, access controls, and use of encryption. The rating includes our assessment of security vulnerabilities, the way the vendor deals with them, and some selected security features of the product/service.
Functionality is a measure of three factors: what the vendor promises to deliver, the state of the art and what KuppingerCole expects vendors to deliver to meet customer requirements. To score well there must be evidence that the product / service delivers on all of these.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
We focus on security, functionality, ease of delivery, interoperability, and usability for the following key reasons:
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
We also rate vendors on the following characteristics
Innovativeness is measured as the capability to add technical capabilities in a direction which aligns with the KuppingerCole understanding of the market segment(s). Innovation has no value by itself but needs to provide clear benefits to the customer. However, being innovative is an important factor for trust in vendors, because innovative vendors are more likely to remain leading-edge. Vendors must support technical standardization initiatives. Driving innovation without standardization frequently leads to lock-in scenarios. Thus, active participation in standardization initiatives adds to the positive rating of innovativeness.
Market position measures the position the vendor has in the market or the relevant market segments. This is an average rating over all markets in which a vendor is active. Therefore, being weak in one segment doesn’t lead to a very low overall rating. This factor considers the vendor’s presence in major markets.
Financial strength even while KuppingerCole doesn’t consider size to be a value by itself, financial strength is an important factor for customers when making decisions. In general, publicly available financial information is an important factor therein. Companies which are venture-financed are in general more likely to either fold or become an acquisition target, which present risks to customers considering implementing their products.
Ecosystem is a measure of the support network vendors have in terms of resellers, system integrators, and knowledgeable consultants. It focuses mainly on the partner base of a vendor and the approach the vendor takes to act as a “good citizen” in heterogeneous IT environments.
Again, please note that in KuppingerCole Leadership Compass documents, most of these ratings apply to the specific product and market segment covered in the analysis, not to the overall rating of the vendor.
For vendors and product feature areas, we use a separate rating with five different levels, beyond the Leadership rating in the various categories. These levels are
KuppingerCole tries to include all vendors within a specific market segment in their Leadership Compass documents. The scope of the document is global coverage, including vendors which are only active in regional markets such as Germany, Russia, or the US.
However, there might be vendors which don’t appear in a Leadership Compass document due to various reasons:
The target is providing a comprehensive view of the products in a market segment. KuppingerCole will provide regular updates on their Leadership Compass documents.
We provide a quick overview about vendors not covered and their offerings in chapter Vendors and Market Segments to watch. In that chapter, we also look at some other interesting offerings around the market and in related market segments.
© 2025 KuppingerCole Analysts AG. All rights reserved. Reproducing or distributing this publication in any form is prohibited without prior written permission. The conclusions, recommendations, and predictions in this document reflect KuppingerCole's initial views. As we gather more information and conduct deeper analysis, the positions presented here may undergo refinements or significant changes. KuppingerCole disclaims all warranties regarding the completeness, accuracy, and adequacy of this information. Although KuppingerCole research documents may discuss legal issues related to information security and technology, we do not provide legal services or advice, and our publications should not be used as such. KuppingerCole assumes no liability for errors or inadequacies in the information contained in this document. Any expressed opinion may change without notice. All product and company names are trademarks™ or registered® trademarks of their respective holders. Their use does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts supports IT professionals with exceptional expertise to define IT strategies and make relevant decisions. As a leading analyst firm, KuppingerCole offers firsthand, vendor-neutral information. Our services enable you to make decisions crucial to your business with confidence and security.
Founded in 2004, KuppingerCole is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as technologies enabling Digital Transformation. We assist companies, corporate users, integrators, and software manufacturers to address both tactical and strategic challenges by making better decisions for their business success. Balancing immediate implementation with long-term viability is central to our philosophy.
For further information, please contact clients@kuppingercole.com.